.jpg)
I just completed 2nd week of course 5 in 2 days.
What I (We) learn in the 2nd week of this course?
In the second week of this course, we'll learn about cryptology. We'll explore different types of encryption practices and how they work. We'll show you the most common algorithms used in cryptography and how they've evolved over time. By the end of this module, you'll understand how symmetric encryption, asymmetric encryption, and hashing work; you'll also know how to choose the most appropriate cryptographic method for a scenario you may see in the workplace.
To Join this course click on the link below
.jpg)
Google IT Support Professional Certificate http://bit.ly/2JONxKk
Our main objectives.
- Define and recognize security risks, vulnerabilities and threats.
- Be able to identify the most common security attacks.
- Understand how security revolves around the CIA principle.
Meet Our trainer(s) for Course 5

Gian Spicuzza
His name is Gian Spicuzza, and I'm the Program Manager in Android Security. He helps protect Androids, two billion plus devices, by managing and driving new security features for each Android design release or versions of Android.
Theory covered in Week 2
1. Cryptography
When you were little, did you and your siblings ever communicate in a secret language around your parents? It didn't really matter what you were talking about, as long as your parents didn't know what it was. That was the fun part, right? It may have seemed like a fun game when you were younger. But for as long as humans have been around, we've created ways to keep messages secret from others. In this lesson, we'll cover how this plays out through symmetric encryption, asymmetric encryption, and hashing. We'll also go over how to describe the most common algorithms in cryptography. And learn how to choose the most appropriate cryptographic method in any given scenario. But before we dive into the nitty-gritty details of cryptography, the various types that exist in our applications, let's go over some terminology and general principles that will help you understand the details later. The topic of cryptography, or hiding messages from potential enemies, has been around for thousands of years. It's evolved tremendously with the advent of modern technology, computers and telecommunications. Encryption is the act of taking a message, called plaintext, and applying an operation to it, called a cipher. So that you receive a garbled, unreadable message as the output, called ciphertext. The reverse process, taking the garbled output and transforming it back into the readable plain text is called decryption. For example, let's look at a simple cipher, where we substitute e for o and o for y. We'll take the plaintext Hello World and feed it into our basic cipher. What do you think the resulting ciphertext will be? Hopefully, you've got Holly Wyrld.

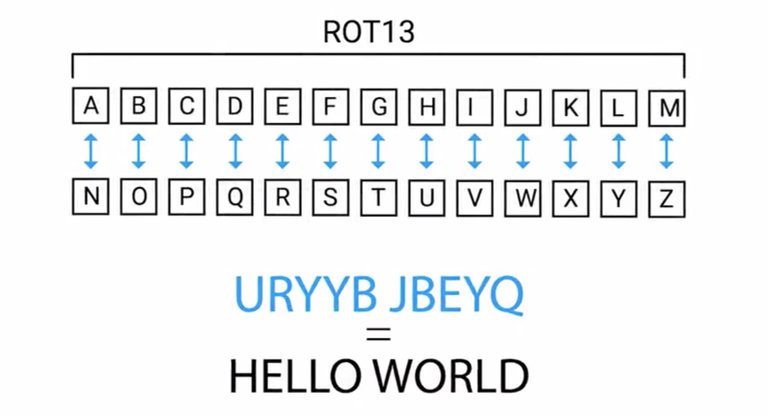
It's pretty easy to decipher the ciphertext since this is a very basic example. There are much more complex and secure ciphers or algorithms that we'll cover later in the section. A cipher is actually made up of two components, the encryption algorithm and the key. The encryption algorithm is the underlying logic or process that's used to convert the plaintext into ciphertext. These algorithms are usually very complex mathematical operations. But there are also some very basic algorithms that we can take a closer look at that don't necessarily require a PhD in math to understand.
The other crucial component of a cipher is the key, which introduces something unique into your cipher. Without the key, anyone using the same algorithm would be able to decode your message, and you wouldn't actually have any secrecy. So to recap, first you pick an encryption algorithm you'd like to use to encode your message, then choose a key. Now you have a cipher, which you can run your plaintext message through and get an encrypted ciphertext out ready to be sent out into the world, safe and secure from prying eyes. Doesn't this make you feel like an international person of mystery? Just wait, given that the underlying purpose of cryptography is to protect your secrets from being read by unauthorized parties, it would make sense that at least some of the components of a cipher would need to be kept secret too, right? You can keep the argument that by keeping the algorithm secret, your messages are secured from a snooping third party, and technically you wouldn't be wrong. This general concept is referred to as, security through obscurity, which basically means, if no one knows what algorithm were using or general security practice, then we're safe from attackers. Think of hiding your house key under you doormat, as long as the burglar doesn't know that you hide the spare key under the mat, you're safe.

But once that information is discovered, all security goes out the window along with your valuables. So clearly, security through obscurity isn't something that you should rely on for securing communication or systems, or for your house for that matter. This overall concept of cryptography is referred to as Kerchoff's principle. This principle states that a cryptosystem, or a collection of algorithms for key generation and encryption and decryption operations that comprise a cryptographic service should remain secure, even if everything about the system is known except for the key. What this means is that even if your enemy knows the exact encryption algorithm you use to secure your data, they're still unable to recover the plaintext from an intercepted ciphertext. You may also hear this principle referred to as Shannon's maxim or the enemy knows the system. The implications are the same.
The system should remain secure, even if your adversary knows exactly what kind of encryption systems you're employing, as long as your keys remain secure. We already defined encryption, but the overarching discipline that covers the practice of coding and hiding messages from third parties is called cryptography. The study of this practice is referred to as cryptology. The opposite of this looking for hidden messages or trying to decipher coded message is referred to as cryptanalysis. These two fields have co-evolved throughout history with new ciphers and cryptosystems being developed as previous ones were broken or found to vulnerable. One of the earliest recorded descriptions of cryptanalysis is from a ninth century Arabian mathematician. Who described a method for frequency analysis to break coded messages. Frequency analysis is the practice of studying the frequency with which letters appear in ciphertext. The premise behind this type of analysis is that in written languages, certain letters appear more frequently than others, and some letters are more commonly grouped together than others. For example, the most commonly used letters in the English language are e, t, a, and o. The most commonly seen pairs of these letters are th, on, and an. Some ciphers, especially classical transposition and substitution ciphers preserve the relative frequency of letters in the plaintext. And so our potentially vulnerable to this type of analysis. During World War I and World War II, cryptography and cryptanalysis played an increasingly important role. There was a shift away from linguistics and frequency analysis and a move towards more mathematical based analysis. This was due to more complex and sophisticated ciphers being developed. A major turning point in the field of cryptanalysis was during World War II when the US allies began to incorporate sophisticated mathematics to aid in breaking access encryption schemes. This also saw the first use of automation technology applied to cryptanalysis in England at Bletchley Park.

The first programmable digital computer, named Colossus, was developed to aid in this effort. While early computers were applied to breaking cryptography, this opened the door for a huge leap forward and a development of even more sophisticated and complex cryptosystems. Steganography is a related practice but distinctly different from cryptography. It's the practice of hiding information from observers, but not encoding it. Think of writing a message using invisible ink. The message is in plaintext and no decoding is necessary to read the text but the text is hidden from sight. The ink is invisible and must be made visible using a mechanism known to the recipient.
Modern steganographic techniques include embedding messages and even files into other files like images or videos. To a casual observer, they would just see a picture of a cute puppy. But if you feed that image into steganography software, it would extract a message hidden within the image file. What's not so secret is how fun it is to learn about all of this spy stuff, don't you think? Stick around, because next, we'll talk about specific cryptographic methods and systems.
It’s been said that the advent of modern computing has spelled the death of the field of cryptanalysis; but the practice is still alive and well -- it’s the methodology that’s changed as technology has transformed the landscape. As quantum computing continues to develop, there’re concerns that modern encryption could be at risk of being broken. This is because most modern encryption algorithms are based on large prime number factorization being computationally difficult, something that can be significantly sped up by quantum computing. Because of this, quantum computing would allow for significantly faster factorization and brute-force attacks on encryption keys, making the future of modern cryptography questionable in the looming quantum computing era.
https://en.wikipedia.org/wiki/Integer_factorization
2. Symmetric Cryptography
Before we dive into things like bringing down digital thieves, let's get some of the terminology out of the way. We'll be using these terms throughout the entire course. So you should know them inside and out before we get started. The first one is Risk. The possibility of suffering a loss in the event of an attack on the system. Let's say that you buy a new phone. One security measure you can take to protect your device, is to set up a screen lock using a password or pattern that you add to prevent others from accessing your info. A screen lock is a security feature that helps prevent unwanted access by creating an action you have to do to gain entry. If you choose not to add a screen lock to your phone, the risk that you take is that someone could easily gain access to your phone and steal your data. Even adding something as simple as a passcode or a screen lock can help you protect your personal or company data from getting into the wrong hands. Next up is the term Vulnerability. A flaw in the system that could be exploited to compromise the system. Vulnerabilities can be holes that you may or may not be aware of. Maybe you go away for a long vacation and lock every door and window in your house before you leave. But you forget to lock the bathroom window. That bathroom window is now a vulnerability that burglars can use to break into your house. Another example is when you're writing a web app and enable a de-bug account for testing during development but forget to disable it before launching the app. You now have a vulnerability in your app that an attacker can potentially discover. There's a special type of vulnerability called a 0-day vulnerability or zero day for short. Which is a vulnerability that is not known to the software developer or vendor, but is known to an attacker. The name refers to the amount of time the software vendor has had to react to and to fix the vulnerability, zero days. Another key term is Exploit. Software that is used to take advantage of a security bug or vulnerability. Attackers will write up exploits for vulnerabilities they find in software to cause harm to the system. Let's say the attacker discovers a zero day vulnerability. She decides to take advantage of the previously unknown bug and writes a zero day exploit code. That code will specifically target and take advantage of this unknown bug to gain access and cause damage to systems. Not cool. The next term to know is Threat. The possibility of danger that could exploit a vulnerability. Threats are just possible attackers, sort of like burglars. Not all burglars will attempt to break into your home to steal your most prized possessions, but they could, and so they're considered threats. Next up, Hacker. A hacker in the security world is someone who attempts to break into or exploit a system. Most of us associate hackers with malicious figures. But there are actually two common types of hackers. You have black hat hackers, who try to get into systems to do something malicious. There are also white hat hackers who attempt to find weaknesses in a system, but also alert the owners of those systems so that they can fix it before someone else does something malicious.

While there are other types of hackers, these are the two main ones and the most important for us to understand right now. The last term to know is Attack. Which is an actual attempt at causing harm to a system. It's super important to be aware of possible threats and vulnerabilities to your system so that you can better prepare for them. The sad reality is that there will always be attacks on your system. But before you start searching for an underground bunker to spend the rest of your days in, remember that there are ways that you can detect and mitigate attacks and we're here to help you learn how to do just that. In this module, we'll be talking about some of the common attacks that you will encounter at home and in the workplace. Throughout the course, you'll learn how to harden your systems against these attacks. Turns out, there are hundreds of ways that your system can be attacked. But there are also hundreds of ways that you can prevent them. We won't talk about all of them, but we will cover the major ones. So abandon the bunker idea and prepare to dive in because things are about to get real. Real secure.
3. Symmetric Cryptography
So far, we've been talking pretty generally about cryptographic systems and focusing primarily on encryption concepts but not decryption. It makes sense that if you're sending a protected message to someone, you'd want your recipient to be able to decode the message and read it, and maybe even reply with a coded message of their own. So let's check out the first broad category of encryption algorithms and dive into more details about how it works along with some pros and cons. When we covered Kerchhoff's principle earlier, do you remember which component of the cipher is crucial to keep secret? That's right. The key must be kept private to ensure that an eavesdropper wouldn't be able to decode encrypted messages. In this scenario, we're making the assumption that the algorithm in use is what's referred to as symmetric-key algorithm. These types of encryption algorithms are called symmetric because they use the same key to encrypt and decrypt messages. Let's take a simple example of a symmetric key encryption algorithm to walk through the overall process of encrypting and decrypting a message. A substitution cipher is an encryption mechanism that replaces parts of your plaintext with ciphertext. Remember our hello world example from earlier. That's an example of substitution cipher since we're substituting some characters with different ones. In this case, the key would be the mapping of characters between plaintext and ciphertext without knowing what letters get replaced with. You wouldn't be able to easily decode the ciphertext and recover the plaintext. If you have the key or the substitution table, then you can easily reverse the process and decrypt the coded message by just performing the reverse operation. A well-known example of a substitution cipher is the Caesar cipher, which is a substitution alphabet. In this case, you're replacing characters in the alphabet with others usually by shifting or rotating the alphabet, a set of numbers or characters. The number of the offset is the key. Another popular example of this is referred to as R O T 13 or ROT-13, where the alphabet is rotated 13 places, but really ROT-13 is a Caesar cipher that uses a key of 13. Let's go back to our hello world example and walk through encoding it using our ROT-13 cipher. Our ciphertexts winds up being URYYB JBEYQ. To reverse this process and go back to the plaintext, we just performed the reverse operation by looking up the characters in the output side of the mapping table.
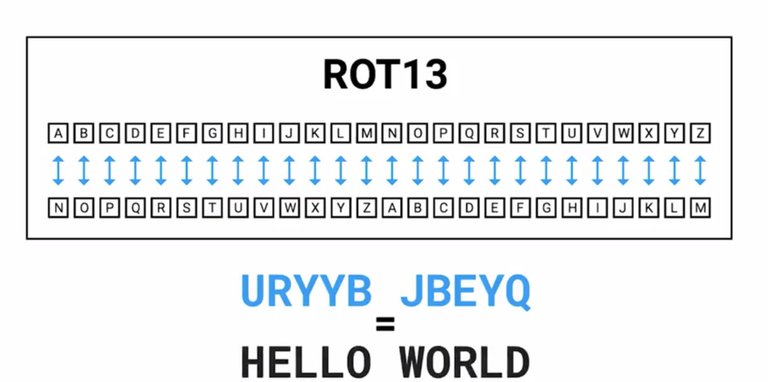
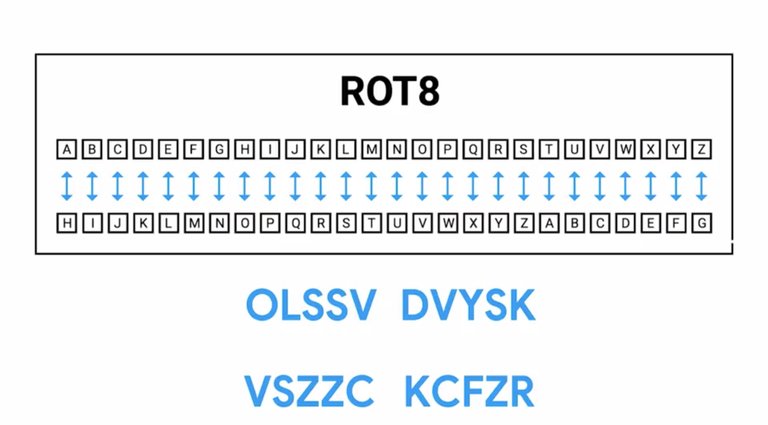
You might notice something about the ROT-13 mapping table or the fact that we're offsetting the alphabet by 13 characters. Thirteen is exactly half of the alphabet. This results in the ROT-13 cipher being an inverse of itself. What this means is that you can recover the plaintext from ciphertext by performing the ROT-13 operation on the ciphertext. If we were to choose a different key, let's say eight, can we do the same thing? Let's check. Here's the mapping table for an offset of eight, which gives us the ciphertext of OLSSV DVYSK. If we run this through the cipher once more, we get the following output VSZZC KCFZR. That doesn't work to reverse the encryption process, does it?
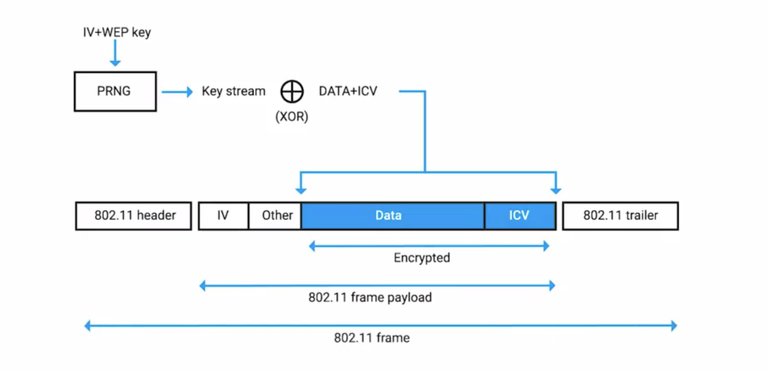
There are two more categories that symmetric key ciphers can be placed into. They're either block ciphers or they're stream ciphers. This relates to how the ciphers operate on the plaintext to be encrypted. A stream cipher as the name implies, takes a stream of input and encrypts the stream one character or one digit at a time, outputting one encrypted character or digit at a time. So, there's a one- to-one relationship between data in and encrypted data out. The other category of symmetric ciphers is block ciphers. The cipher takes data in, places that into a bucket or block of data that's a fixed size, then encodes that entire block as one unit. If the data to be encrypted isn't big enough to fill the block, the extra space will be padded to ensure the plaintext fits into the blocks evenly. Now generally speaking, stream ciphers are faster and less complex to implement, but they can be less secure than block ciphers. If the key generation and handling isn't done properly, if the same key is used to encrypt data two or more times, it's possible to break the cipher and to recover the plaintext. To avoid key reuse, initialization vector or IV is used. That's a bit of random data that's integrated into the encryption key and the resulting combined key is then used to encrypt the data. The idea behind this is if you have one shared master key, then generate a one-time encryption key. That encryption key is used only once by generating a new key using the master one and the IV. In order for the encrypted message to be decoded, the IV must be sent in plaintext along with the encrypted message. A good example of this can be seen when inspecting the 802.11 frame of a WEP encrypted wireless packet. The IV is included in plaintext right before the encrypted data payload. , we'll explore symmetric encryption in more detail, illustrating some of the more popular algorithms and dive into the pros and cons of using symmetric encryption.
4. Symmetric Encryption Algorithms
In the last section, we covered the basics of what exactly symmetric encryption algorithms are and gave a basic example of the Caesar cipher, a type of substitution cipher. We couldn't possibly protect anything of value using the cipher though, right? There must be more complex and secure symmetric algorithms, right? Of course, there are. One of the earliest encryption standards is DES, which stands for Data Encryption Standard. DES was designed in the 1970s by IBM, with some input from the US National Security Agency. DES was adopted as an official FIPS, Federal Information Processing Standard for the US. This means that DES was adopted as a federal standard for encrypting and securing government data. DES is a symmetric block cipher that uses 64-bit key sizes and operates on blocks 64-bits in size. Though the key size is technically 64-bits in length, 8-bits are used only for parity checking, a simple form of error checking. This means that real world key length for DES is only 56-bits.
A quick note about encryption key sizes since we haven't covered that yet. In symmetric encryption algorithms, the same key is used to encrypt as to decrypt, everything else being the same.
The key is the unique piece that protects your data and the symmetric key must be kept secret to ensure the confidentiality of the data being protected. The key size, defined in bits, is the total number of bits or data that comprises the encryption key. So you can think of the key size as the upper limit for the total possible keys for a given encryption algorithm. Key length is super important in cryptography since it essentially defines the maximum potential strength of the system. Imagine an ideal symmetric encryption algorithm where there are no flaws or weaknesses in the algorithm itself. In this scenario, the only possible way for an adversary to break your encryption would be to attack the key instead of the algorithm. One attack method is to just guess the key and see if the message decodes correctly. This is referred to as a brute-force attack. Longer key lengths protect against this type of attack. Let's take the DES key as an example. 64-bits long minus the 8 parity bits gives us a key length of 56-bits. This means that there are a maximum of 2 to the 56th power, or 72 quadrillion possible keys. That seems like a ton of keys, and back in the 1970s, it was. But as technology advanced and computers got faster and more efficient, 64-bit keys quickly proved to be too small. What were once only theoretical attacks on a key size became reality in 1998 when the EFF, Electronic Frontier Foundation, decrypted a DES-encrypted message in only 56 hours. Because of the inherent weakness of the small key size of DES, replacement algorithms were designed and proposed. A number of new ones appeared in the 1980s and 1990s. Many kept the 64-bit block size, but used a larger key size, allowing for easier replacement of DES. In 1997, the NIST, National Institute of Standards and Technology, wanted to replace DES with a new algorithm, and in 2001, adopted AES, Advanced Encryption Standard, after an international competition. AES is also the first and only public cipher that's approved for use with top secret information by the United States National Security Agency. AES is also a symmetric block cipher similar to DES in which it replaced. But AES uses 128-bit blocks, twice the size of DES blocks, and supports key lengths of 128-bit, 192-bit, or 256-bit. Because of the large key size, brute-force attacks on AES are only theoretical right now, because the computing power required (or time required using modern technology) exceeds anything feasible today. I want to call out that these algorithms are the overall designs of the ciphers themselves. These designs then must be implemented in either software or hardware before the encryption functions can be applied and put to use. An important thing to keep in mind when considering various encryption algorithms is speed and ease of implementation. Ideally, an algorithm shouldn't be overly difficult to implement because complicated implementation can lead to errors and potential loss of security due to bugs introduced in implementation. Speed is important because sometimes data will be encrypted by running the data through the cipher multiple times. These types of cryptographic operations wind up being performed very often by devices, so the faster they can be accomplished with the minimal impact to the system, the better. This is why some platforms implement these cryptographic algorithms in hardware to accelerate the processes and remove some of the burden from the CPU. For example, modern CPUs from Intel or AMD have AES instructions built into the CPUs themselves. This allows for far greater computational speed and efficiency when working on cryptographic workloads. Let's talk briefly about what was once a wildly used and popular algorithm but has since been proven to be weak and is discouraged from use. RC4, or Rivest Cipher 4, is a symmetric stream cipher that gained widespread adoption because of its simplicity and speed. RC4 supports key sizes from 40-bits to 2,048-bits. So the weakness of RC4 aren't due to brute-force attacks, but the cipher itself has inherent weaknesses and vulnerabilities that aren't only theoretically possible, there are lots of examples showing RC4 being broken. A recent example of RC4 being broken is the RC4 NOMORE attack. This attack was able to recover an authentication cookie from a TLS-encrypted connection in just 52 hours. As this is an attack on the RC4 cipher itself, any protocol that uses this cipher is potentially vulnerable to the attack. Even so, RC4 was used in a bunch of popular encryption protocols, like WEP for wireless encryption, and WPA, the successor to WEP. It was also supported in SSL and TLS until 2015 when RC4 was dropped in all versions of TLS because of inherent weaknesses. For this reason, most major web browsers have dropped support for RC4 entirely, along with all versions of SSL, and use TLS instead. The preferred secure configuration is TLS 1.2 with AES GCM, a specific mode of operation for the AES block cipher that essentially turns it into a stream cipher. GCM, or Galois/Counter Mode, works by taking randomized seed value, incrementing this and encrypting the value, creating sequentially numbered blocks of ciphertexts. The ciphertexts are then incorporated into the plain text to be encrypted. GCM is super popular due to its security being based on AES encryption, along with its performance, and the fact that it can be run in parallel with great efficiency. You can read more about the RC4 NOMORE attack in the next reading. So now that we have covered symmetric encryption and some examples of symmetric encryption algorithms, what are the benefits or disadvantages of using symmetric encryption? Because of the symmetric nature of the encryption and decryption process, it's relatively easy to implement and maintain. That's one shared secret that you have to maintain and keep secure. Think of your Wi-Fi password at home. There's one shared secret, your Wi-Fi password, that allows all devices to connect to it. Can you imagine having a specific Wi-Fi password for each device of yours? That would be a nightmare and super hard to keep track of. Symmetric algorithms are also very fast and efficient at encrypting and decrypting large batches of data. So what are the downsides of using symmetric encryption? While having one shared secret that both encrypts and decrypts seems convenient up front, this can actually introduce some complications. What happens if your secret is compromised? Imagine that your Wi-Fi password was stolen and now you have to change it. Now you have to update your Wi-Fi password on all your devices and any devices your friends or family might bring over. What do you have to do when a friend or family member comes to visit and they want to get on your Wi-Fi? You need to provide them with your Wi-Fi password, or the shared secret that protects your Wi-Fi network. This usually isn't an issue since you hopefully know the person and you trust them, and it's usually only one or two people at a time. But what if you had a party at your place with 50 strangers? Side note, why are you having a party at your home with 50 strangers? Anyhow, how could you provide the Wi-Fi password only to the people you trust without strangers overhearing? Things could get really awkward really fast. In the next lesson, we'll explore other ways besides symmetric key algorithms to protect data and information.
For more information about symmetric encryptions, check out the following link here. http://www.rc4nomore.com/
5. Asymmetric Cryptography
In the previous lesson, we covered one of two major categories that encryption ciphers fall into, symmetric key ciphers. In this next lesson, we'll cover the second class of ciphers called asymmetric or public key ciphers. Remember why symmetric ciphers are referred to as symmetric? It's because the same key is used to encrypt as to decrypt. This is in contrast to asymmetric encryption systems because as the name implies, different keys are used to encrypt and decrypt. So how exactly does that work? Well, let's imagine here that there are two people who would like to communicate securely, we'll call them Suzanne and Daryll. Since they're using asymmetric encryption in this example, the first thing they each must do is generate a private key, then using this private key, a public key is derived. The strength of the asymmetric encryption system comes from the computational difficulty of figuring out the corresponding private key given a public key. Once Suzanne and Daryll have generated private and public key pairs, they exchange public keys. You might have guessed from the names that the public key is public and can be shared with anyone, while the private key must be kept secret. When Suzanne and Daryll have exchanged public keys, they're ready to begin exchanging secure messages. When Suzanne wants to send Daryll an encrypted message, she uses Daryll's public key to encrypt the message and then send the ciphertext. Daryll can then use his private key to decrypt the message and read it, because of the relationship between private and public keys, only Daryll's private key can decrypt messages encrypted using Daryll's public key.
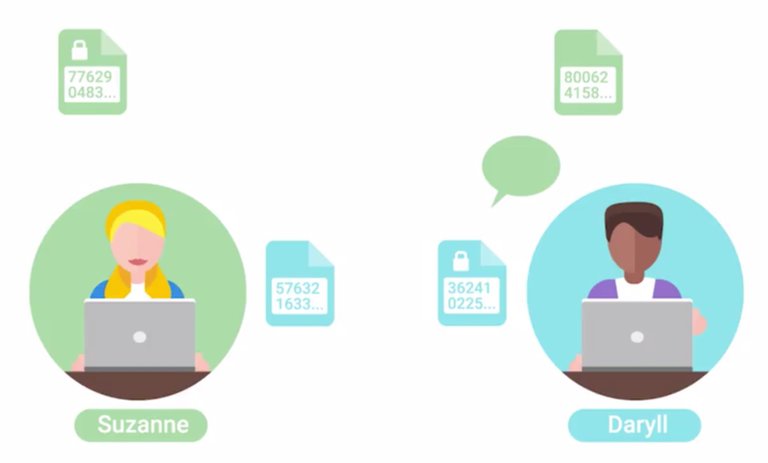
The same is true of Susanne's key pairs. So when Daryll is ready to reply to Suzanne's message, he'll use Suzanne's public key to encode his message and Suzanne will use her private key to decrypt the message. Can you see why it's called asymmetric or public key cryptography? We've just described encryption and decryption operations using an asymmetric cryptosystem, but there's one other very useful function the system can perform, public key signatures. Let's go back to our friends Suzanne and Daryll. Let's say, Suzanne wants to send a message to Darryll and she wants to make sure that Daryll knows the message came from her and no one else, and that the message was not modified or tampered with. She could do this by composing the message and combining it with her private key to generate a digital signature. She then sends this message along with the associated digital signature to Daryll. We're assuming Suzanne and Daryll have already exchanged public keys previously in this scenario. Daryll can now verify the message's origin and authenticity by combining the message, the digital signature, and Suzanne's public key. If the message was actually signed using Susanne's private key and not someone else's and the message wasn't modified at all, then the digital signature should validate. If the message was modified, even by one whitespace character, the validation will fail and Daryll shouldn't trust the message. This is an important component of the asymmetric cryptosystem. Without message verification, anyone could use Daryll's public key and send him an encrypted message claiming to be from Suzanne. The three concepts that an asymmetric cryptosystem grants us are confidentiality, authenticity, and non-repudiation. Confidentiality is granted through the encryption-decryption mechanism. Since our encrypted data is kept confidential and secret from unauthorized third parties. Authenticity is granted by the digital signature mechanism, as the message can be authenticated or verified that it wasn't tampered with. Non-repudiation means that the author of the message isn't able to dispute the origin of the message. In other words, this allows us to ensure that the message came from the person claiming to be the author. Can you see the benefit of using an asymmetric encryption algorithm versus a symmetric one? Asymmetric encryption allows secure communication over an untrusted channel, but with symmetric encryption, we need some way to securely communicate the shared secret or key with the other party. If that's the case, it seems like asymmetric encryption is better, right? Well, sort of. While asymmetric encryption works really well in untrusted environments, it's also computationally more expensive and complex. On the other hand, symmetric encryption algorithms are faster, and more efficient, and encrypting large amounts of data. In fact, what many secure communications schemes do is take advantage of the relative benefits of both encryption types by using both, for different purposes. An asymmetric encryption algorithm is chosen as a key exchange mechanism or cipher. What this means, is that the symmetric encryption key or shared secret is transmitted securely to the other party using asymmetric encryption to keep the shared secret secure in transit. Once the shared secret is received, data can be sent quickly, and efficiently, and securely using an asymmetric encryption cipher. Clever? One last topic to mention is somewhat related to asymmetric encryption and that's MACs or Message Authentication Codes, not to be confused with media access control or MAC addresses. A MAC is a bit of information that allows authentication of a received message, ensuring that the message came from the alleged sender and not a third party masquerading as them. It also ensures that the message wasn't modified in some way in order to provide data integrity. This sounds super similar to digital signatures using public key cryptography, doesn't it? While very similar, it differs slightly since the secret key that's used to generate the MAC is the same one that's used to verify it. In this sense, it's similar to symmetric encryption system and the secret key must be agreed upon by all communicating parties beforehand or shared in some secure way. This describes one popular and secure type of MAC called HMAC or a Keyed-Hash Message Authentication Code. HMAC uses a cryptographic hash function along with a secret key to generate a MAC. Any cryptographic hash functions can be used like Shahwan or MD5 and the strength or security of the MAC is dependent upon the underlying security of the cryptographic hash function used. The MAC is sent alongside the message that's being checked. The Mac is verified by the receiver by performing the same operation on the received message, then comparing the computed MAC with the one received with the message. If the MACs are the same, then the message is authenticated. There are also MACs based on symmetric encryption ciphers, either block or stream like DES or AES, which are called CMACs or Cipher-Based Message Authentication Codes. The process is similar to HMAC, but instead of using a hashing function to produce a digest, a symmetric cipher with a shared keys used to encrypt the message and the resulting output is used as the MAC. A specific and popular example of a CMAC though slightly different is CBC-MAC or Cipher Block Chaining Message Authentication Codes. CBC-MAC is a mechanism for building MACs using block ciphers. This works by taking a message and encrypting it using a block cipher operating in CBC mode. CBC mode is an operating mode for block ciphers that incorporates a previously encrypted block cipher text into the next block's plain text. So, it builds a chain of encrypted blocks that require the full, unmodified chain to decrypt. This chain of interdependently encrypted blocks means that any modification to the plain text will result in a different final output at the end of the chain, ensuring message integrity. In the next section, we'll check out some common examples of asymmetric encryption algorithms and systems. I'll see you there.
6. Asymmetric Encryption Algorithms
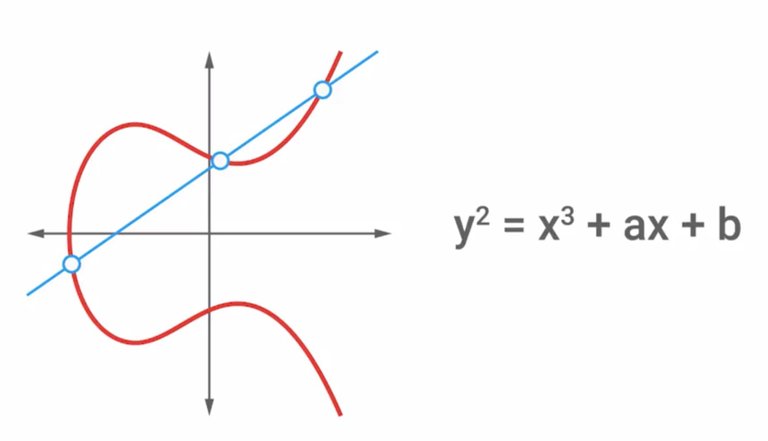
So, one of the first practical asymmetric cryptography systems to be developed is RSA, name for the initials of the three co-inventors. Ron Rivest, Adi Shamir and Leonard Adleman. This crypto system was patented in 1983 and was released to the public domain by RSA Security in the year 2000. The RSA system specifies mechanisms for generation and distribution of keys along with encryption and decryption operation using these keys. We won't go into the details of the math involved, since it's pretty high-level stuff and beyond the scope of this class. But, it's important to know that the key generation process depends on choosing two unique, random, and usually very large prime numbers. DSA or Digital Signature Algorithm is another example of an asymmetric encryption system, though its used for signing and verifying data. It was patented in 1991 and is part of the US government's Federal Information Processing Standard. Similar to RSA, the specification covers the key generation process along with the signing and verifying data using the key pairs. It's important to call out that the security of this system is dependent on choosing a random seed value that's incorporated into the signing process. If this value was leaked or if it can be inferred if the prime number isn't truly random, then it's possible for an attacker to recover the private key. This actually happened in 2010 to Sony with their PlayStation 3 game console. It turns out they weren't ensuring this randomized value was changed for every signature. This resulted in a hacker group called failOverflow being able to recover the private key that Sony used to sign software for their platform. This allowed moders to write and sign custom software that was allowed to run on the otherwise very locked down console platform. This resulted in game piracy becoming a problem for Sony, as this facilitated the illicit copying and distribution of games which caused significant losses in sales. I've included links to more about this in the next reading, in case you want to dive deeper. Earlier, we talked about how asymmetric systems are commonly used as key exchange mechanisms to establish a shared secret that will be used with symmetric cipher. Another popular key exchange algorithm is DH or Diffie-Hellman named for the co-inventors. Let's walk through how the DH key exchange algorithm works. Let's assume we have two people who would like to communicate over an unsecured channel, and let's call them Suzanne and Daryll. I've grown pretty fond of these two. First, Suzanne and Daryl agree on the starting number that would be random and will be very large integer. This number should be different for every session and doesn't need to be secret. Next, each person chooses another randomized large number but this one is kept secret. Then, they combine their shared number with their respective secret number and send the resulting mix to each other. Next, each person combines their secret number with the combined value they received from the previous step. The result is a new value that's the same on both sides without disclosing enough information to any potential eavesdroppers to figure out the shared secret. This algorithm was designed solely for key exchange, though there have been efforts to adapt it for encryption purposes. It's even been used as part of a PKI system or Public Key Infrastructure system. We'll dive more into PKI systems later in this course. Elliptic curve cryptography or ECC is a public key encryption system that uses the algebraic structure of elliptic curves over finite fields to generate secure keys. What does that even mean? Well, traditional public key systems, make use of factoring large prime numbers whereas ECC makes use of elliptic curves. And elliptic curve is composed of a set of coordinates that fit in equation, similar to something like Y to the second equals X to the third, plus A X plus B. Elliptic curves have a couple of interesting and unique properties. One is horizontal symmetry, which means that at any point in the curve can be mirrored along the x axis and still make up the same curve. On top of this, any non-vertical line will intersect the curve in three places at most. Its this last property that allows elliptic curves to be used in encryption.
The benefit of elliptic curve based encryption systems is that they are able to achieve security similar to traditional public key systems with smaller key sizes. So, for example, a 256 bit elliptic curve key, would be comparable to a 3,072 bit RSA key. This is really beneficial since it reduces the amount of data needed to be stored and transmitted when dealing with keys. Both Diffie-Hellman and DSA have elliptic curve variants, referred to as ECDH and ECDSA, respectively. The US NEST recommends the use of EC encryption, and the NSA allows its use to protect up the top secret data with 384 bit EC keys. But, the NSA has expressed concern about EC encryption being potentially vulnerable to quantum computing attacks, as quantum computing technology continues to evolve and mature. I'm going to buy Suzanne and Darryl drink today for all their hard work. In the meantime, we've cooked up an assignment for you that will test your encryption and decryption skills. Take your time to decode all the details, and I'll see you all in the next lesson.
An asymmetric encryption attack happened in 2010 to Sony with their Playstation 3 game console. https://nakedsecurity.sophos.com/2012/10/25/sony-ps3-hacked-for-good-master-keys-revealed/
It turns out they weren’t ensuring the randomized seed value was changed for every signature. This resulted in a hacker group called 'fail0verflow' being able to recover the private key that Sony used to sign software for the platform. This allowed modders to write and sign custom software that was allowed to run on the otherwise very locked down console platform. This resulted in game piracy becoming a problem for Sony, as this facilitated the illicit copying and distribution of games, causing a significant loss in sales.
https://www.theguardian.com/technology/gamesblog/2011/jan/07/playstation-3-hack-ps3
This is part 1 of Week 2 .For Part 2 Click here http://bit.ly/2CQ4LsB
To Join this course click on the link below
.jpg)
Google IT Support Professional Certificate http://bit.ly/2JONxKk
LInks to previous weeks Courses.
[Week 1] Google IT Support Professional Certificate #29 | Course 5 IT Security: Defense against the digital dark arts
http://bit.ly/2x8hulk
Google IT Support Professional Certificate #0 | Why you should do this Course? | All details before you join this course.
http://bit.ly/2Oe2t8p
#steemiteducation #Computerscience #education #Growwithgoogle #ITskills #systemadministration #itprofessional
#googleitsupportprofessional
Atlast If you are interested in the IT field, this course, or want to learn Computer Science. If you want to know whats in this course, what skills I learned Follow me @hungryengine. I will guide you through every step of this course and share my knowledge from this course daily.
Support me on this journey and I will always provide you with some of the best career knowledge in Computer Science field.
