About a month ago I was hacked, and I got hacked pretty hard but not financially. They stole my phone number, logged into my yahoo account, and ran a script to password reset just about every account I had tied to it. They stole some freebies from coinbase, and took an even smaller amount on a small exchange I use. It only took a few hours for the attackers to steal the crypto from logging into a new devise, despite coinbases password reset policy which is the standard 24 hours. 24 hours isn't much; I used to spend 16 hours a day going to, at, or coming back from the university a day+time you consider sleep-the 24 hour freeze offers little to no protection at all. Also plenty of folks who hardly ever use their phone & email. Needless to say my bittrex account was more secure than sms 2fa, but they still let the attacker change my password. Gemini froze my account luckily.
The attacker was using a mullvad vpn, and mullvad claims not to log ip addresses and they are a swiss based company. So pretty much filing a police report does no good. I chewed out coinbase; how could they violate their TOS, how could they let a user into my account on a vpn, how could let let a user log in in Montreal one moment then 2 hours later let them log on in Atlanta some 1200 miles away. The response from coinbase has been to ignore the issue, and let the hacker steal about $6000 of eth based tokens from users...and maybe closer to 40k between tokens and eth.
One thing I learned from this is not to use SNS based 2fa. Upgrade them to google authenticator-at a minimum-if possible.
So I closed out my bank account to prevent unauthorized wiring of money. Last month I got a brand new phone, and new phone number to start securing my accounts better and to be separated from yahoo. Only I could not register the product nor get the software to work without registering it, so it has been sitting on the sideline. So needless to say I get a call this morning that I was hacked...again. Not this again. But luckily I stepped up security from last time. My coinbase account remains frozen from last month, but lo and behold I get emails saying that someone changed my ip address....from a mullvad based VPN. So they literally had a month to block mullvad ip addresses after being put on notice. So not only do they not follow their own security policy on password reset, they also refuse to close known security vulnerabilities.
So this morning I was kind of more prepared than last month. My important accounts were secure. So I called my phone provider to get my phone # back, before commencing rescues,and to see if they got in through a web portal. Turns out the attackers were calling just the phone representative to transfer my phone number to them. Social engineering, from likely another stolen phone number.
I also go through my yahoo account, which just had a nice password reset a month ago to something very unique. Still they got in, something called "Signed in using phone verification". So something was off. Was there a session hijacking which triggered a 2fa, did someone have remote/viral access to my pc, did someone answer my recover questions, did someone hack my recovery account, was there an "account key" back door. How did this happen? I needed to know so I could secure my account. So I called yahoo's number. They initially thought it was coming from the recovery email address, but then they also noted that it wasn't the case because they got in through a phone. What happens is if you mess up on your password enough times, a text message gets sent to the phone. Ultimately, if an attacker knows there is a phone number attached to your yahoo email address, all they need do is steal your phone number to gain access. Just through social engineering; it's like you have no password at all guarding your crypto. The code they send to your phone number on their phone is all [possibly the 2fa also which ordinarily is codes sent to that phone] they need to get in. Yahoo doesn't offer any extra tools to block users from VPNs from accessing accounts.
Supposedly Yahoo was supposed to rolled out google 2fa back on july 6th which could keep the attacker out if they stole my phone # again, but after checking a few devices and browsers it turns out it wasn't rolled out yet. I'm Not sure when that will be rolled out, but until then if you have a recovery phone number on your yahoo account you are at great risk.
A big company like coinbase, yahoo, gemini, bittrex, ought to allow users to block vpns by default [unless account created through vpn]. There are legitimate uses for VPNs, but outside of these special use cases, companies need to treat them with aggressive hostility. I remember rolling out my social media platform and being hit by spam bots. First thing I did was block the bad ip addresses, blocked guest users [who weren't supposed to be there anyways], and added capchas for users to log in. That isn't a viable solution for say universities, and hence the need to develop intelligence systems to block certain patterns of abuse. But it seems along that way, VPN security vulnerabilities has been ignored by bigtech in favor off algorithms. Now there are online services that supposedly detect if an ip address uses a vpn, but I can understand for privacy reason a company may not want to shed that kind of info to a 3rd party vendor. But still, you can freaking get interns for free to hunt down vpns, put them in a csv , the source of info, and hand them to a chief security officers to process through an algorithm. I'm Pretty sure that will save hours of customer service and even prevent costly litigation.
Sure they could go to say a university, a coffee shop, a macdonalds, etc, as an alternative to a VPN. But if they do that, you pretty much know the attackers real location, and they might even show up on video somewhere. Establishing identity is legally very important. Sure, maybe they'll try to control a zombie net, but the attackers don't sound that sophisticated. Their script is, but the attackers seem amateur for now.
I have been able to trace some of the attackers crypto to a certain eth address.
https://etherscan.io/address/0x544d75cA25DD1c051A4864dFFdd271D94fc5752C#tokentxns
The holder of the keys sent the crypto to kucoin. I asked kucoin them to freeze the account and check with coinbase security, they adamantly refused and needed law enforcement or a court order. claiming it was about protected a users assets. Since when does freezing assets steal assets; how does that breach the duty of a fiduciary? I been meaning to swear out a criminal search warrant myself (F___ the police; let's take power back from them), but I don't presently have meaningful physical access to the courts; I emailed the clerk about electronically filing an affidavit for a search warrant; Silence. I could similarly file a subpoena if I do a small claims against coinbase, but it takes such a long time. I think with a court order that I might just end up with a name and photo of another one of their victims. I know what I can do to at least get geographic information on the attackers.
Anyways, it seems the attacker has stolen at least $27k+ worth of crypto. https://etherscan.io/address/0x544d75cA25DD1c051A4864dFFdd271D94fc5752C But pretty much my gut feeling is, especially with coinbase who violates their own password reset policies to let attackers insta-drain an account, is that they are knowing and willing participants is money laundering. It is really one of the few ways that crypto held in the KYC realm gets converted back into anonymous crypto. It can still be tracked, but they aren't interested in stopping it unless the breach earned mega clout status.
Pretty much the responses I received from most exchanges about the issue is, please we want you to trade with us [and we refuse to listen to your concerns about security holes]. They can't even assured me that they haven't taken appropriate steps to stop this attack vector.
I'm not a fan of coinbase because of their relatively high fees. On the other hand, living in the U.S., there really isn't another reasonable entity, certainly not one I trust more, if you need to move fiat to crypto or vice versa. I do use Google's Authenticator 2FA app though. For some reason i thought coinbase was forcing non-SMS 2fa these days...
I started with coinbase when I was interested in selling some erc-20s I recieved back in late 2017. if they stopped using sms-2fa, seems my account was grandfathered and their webpage says they still use sms. https://help.coinbase.com/en/coinbase/getting-started/verify-my-account/how-do-i-set-up-2-factor-authentication
I quit buying from coinbase when they ban Milo; when other members of the then colibra project were banning conservatives across the spectrum. That is the mark of the beast stuff there, and one of the first things the NAZI's tried to do once they gained power was force the boycott of Jewish companies. Nonetheless, I would participate in the air drops. It was ultimately the withdrawal of the free crypto emails in my yahoo mail notice bar that alerted me something was wrong when I was reading a news article.
I switched to Gemini not knowing they were still connected to facebook. Supposedly Bittrex started using wire transfers of debit cards and that would save me the middle man, but it'll be a while before I put new money in crypto after this incident-and I'll certainly have to create a new bank account just for wiring money before I do.
The fact that they [all] allow[ed] VPN access to the accounts of unwilling Americans is beyond unprofessional and insecure. I am not sure that I can trust any of them.
The crypto choices on Gemini kind of Suck. But they were the only exchange who really noticed something wasn't quite right and [allegedly] took immediate action. Upon reviewing my email they claim they have a 72 hour waiting period in which they freeze withdrawal activity, but their in account notices makes me wonder otherwise. I just made sure to contact them ASAP.
gemini notice:
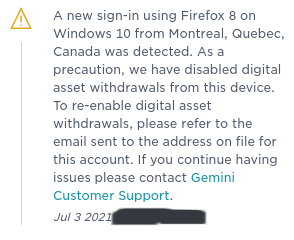
...I never been to Canada
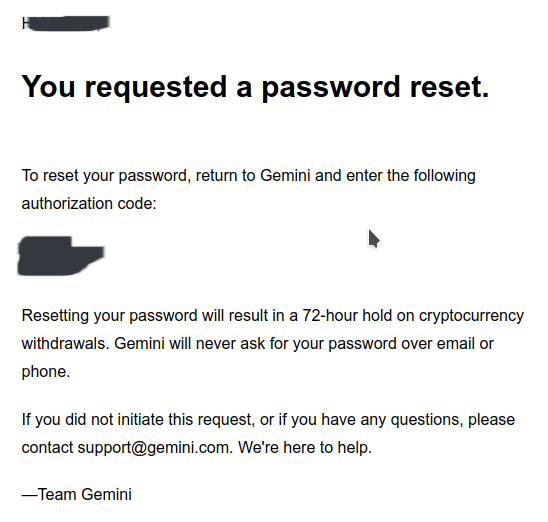
gemini email:
I started using Authenticator because some site forced me to. I only use it for 2 or 3 things so I had thought it had been Coinbase that forced me to use it but I could easily be mistaken.
As far as Milo being banned from Coinbase, other than his say-so, I'm not aware of any evidence that he has been nor am I aware of him or Coinbase providing a reason (if it really happened and one was given). Certainly he could have been and while I defend his right to free speech and do not approve of companies banning individuals for political differences, I don't find Milo to be a particularly trustworthy individual so I'm not exactly going to take his word for it.
At the end of the day, the choices for an exchange, at least one that provides a reasonable path to and from fiat, are still poor. Right now, I consider Coinbase my only reasonable option. Of course, that would be different if my account were hacked and I lost whatever I happened to have there. It's best to use it purely as an exchange and not as storage anyway. As much as I dislike Google too, hopefully their 2FA app provides better protection as there are not options there either.
Congratulations @firstamendment! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
Your next target is to reach 24000 upvotes.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPdrudge featured this cnbc article today on the topic of coinbase fraud.
https://www.cnbc.com/2021/08/24/coinbase-slammed-for-terrible-customer-service-after-hackers-drain-user-accounts.html
So once agin, like clock work, the attackers stole my phone number again. haha, I cut them off at the pass by removing it from my yahoo yahoo. Wrong!
The attackers were able to re-attach the phone number as the recovery account again, then gain access. Luckily my crypto accounts are still frozen. I called up yahoo again, this time they blocked the number-or claimed to. We'll find out next month.