
All data funneled through centralized server.
There has been a lot of drama with Ledger recently. First, their servers got hacked and their data leaked to the darkweb. This is when everyone collectively realized that Ledger had been storing information on users that they never should have been storing in the first place. Names, addresses, and email addresses were leaked. People were literally kidnapped and murdered over this because Ledger doxed their userbase.
Did Ledger get in trouble for this?
Nope of course not.
Business just continued as usual after some bad press.
Then came the backdoor.
Now Ledger is under fire for creating a service that allows the seed to be stored across three different private corporations and able to be recovered with 2FA. Two out of the three shards allows the seed to be recovered. This is a heinous policy considering one server/corporation is in USA and one is in EU; collusion is inevitable.
Many have correctly assessed that this is a huge security breach, and even the CEO of Ledger itself has admitted that a court order would end in the forfeiture of all the crypto on the device. This is considered an "acceptable risk" because Ledger's target demographic are law abiding citizens with less than $50k in their wallet.
I think this is hilarious logic to employ considering the exponential growth of crypto. Crypto does a 100x and all of a sudden their target demographic no longer has <$50k worth of crypto but rather <$5M. To assume that government or other bad actors would not exploit this vulnerability is a childish notion. But I digress.
Here we see a tweet of a guy further criticizing Ledger for bragging about securing 20% of all crypto assets in existence. 20%? Wow I hope that's not true, but it probably is. Insane.
What this guy doesn't seem to understand is that every hardware wallet operator knows exactly how much crypto you have. It's a bit mind blowing that nobody actually knows how any of this works and they just assume that every part of the process is totally decentralized. It is not: decentralization is very difficult to achieve and inefficient in many cases.
Hardware wallet don't know which assets you control.
I bet if you were to ask 99% of hardware wallet owners if their device knows how much crypto they have they'd automatically say yes without even thinking about it. Okay, well... how would it know that? How could a hardware wallet possibly know how much money you have? It literally never connects to the Internet... ever.
Your crypto exists on the internet.
The public ledger is on the Internet for anyone to see. That's kind of the entire point. The ONLY thing a hardware wallet can do is sign messages with the private key. That's it. It doesn't know anything else. And guess what? In many cases the only way to organize an operation that needs a signature is with internet access.
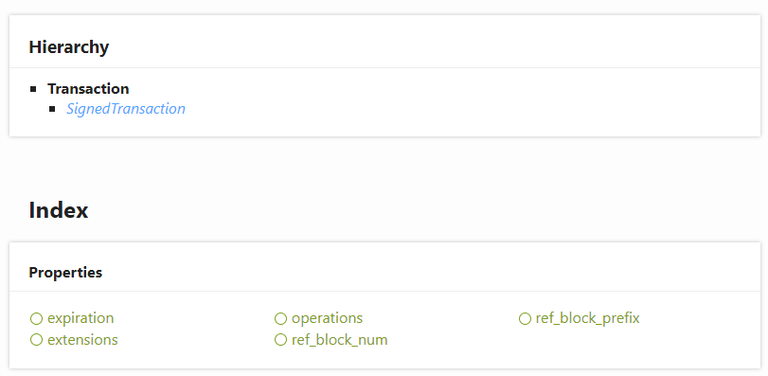
Take Hive for example
On a technical level every operation on Hive must have a ref_block_prefix and a ref_block_num. These variables basically point to a previous block on the current fork. The reason this is necessary is because imagine Hive forked to a new chain... we'll call this new chain Steem or Blurt or something.
Now imagine after the fork happens you try to do something simple like transfer Hive from account @xyz to @abc. What's to stop someone (account @abc) from rebroadcasting that public operation to all the other forks? Say you sent @abc 1000 Hive. @abc could just take that operation and broadcast it to both Blurt and Steem and steal 1000 coins on both chains that you never authorized. ref_block_prefix and a ref_block_num prevent this from happening by referencing a block on the chain long after the forks happened.
The problem is that in order to get a reference to a current block... well you'd need access to the internet to get that info. You need access to a node to setup the transaction so that the hardware wallet even has a valid message to sign in the first place. This means that every single hardware provider funnels all of your data through their private servers and can track anything and everything their customers do. They ALL do it, not just Ledger. Ledger is just blatant about it and even brags on it.
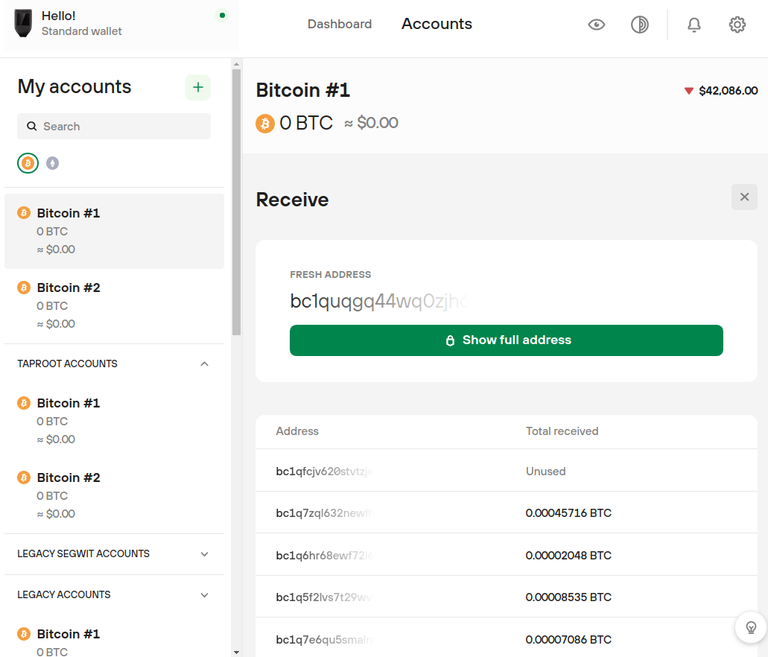
An example for Bitcoin
You know how on a hardware wallet you can have a Bitcoin "account" but that "account isn't actually just a single wallet? In fact, you can click the "deposit" button on an "account" and the Trezor/Ledger website will give you a different public key for every single deposit. This practice increases security/privacy in theory, especially from a on-chain data analysis perspective.
But again how does that work?
Right? Because when you go to spend the money you don't have to dick around and manage 10 different private keys even though you could have deposited money into 10 different public addresses. It "just works". Money sent.
But no see in the background their private centralized servers have to make a decision for you. Imagine you have 4 UTXOs (Unspent transaction outputs)
- 0.1 BTC
- 1 BTC
- 0.25 BTC
- 0.15 BTC
Still with me?
Account X is going to tell you you've got 1.5 BTC in your wallet, but in the background what you really have is the 4 UTXOs listed above. Let's say you wanted to transfer 0.25 BTC somewhere. Well the wallet has a dozen different ways it could actually do that. It could spend 0.25 BTC from the 1 BTC UTXO leaving 0.75 left. It could completely drain the 0.25 wallet leaving nothing left, which would be cheaper than spending the 0.1 BTC & 0.15 BTC UTXOs because it only requires the signature from a single private key.
Point being that none of this is possible without a centralized frontend to do all the heavily lifting to create a seamless user experience. The user is none the wiser, which is exactly why most people have absolutely have no idea how any of this stuff works. It's actually quite centralized in ways that are never even considered or even thought possible.
Metamask
Same story. You connect to a single centralized node and simply hope it's telling you the truth a lot of the time. How does Metamask know how to estimate the fee you need to pay to post an operation? Again, it's owned by a centralized company called ConsenSys and it is this company that pulls a lot of these strings and makes for a seamless user experience. Most haven't the slightest clue as to how it actually works. "It's decentralized, bruv."
Conclusion
Popular hardware wallets are data-harvesting user information and most people haven't the slightest clue. In fact we only express outrage when a company like Ledger straight up admits what they are doing and tells us straight to our faces. Imagine all the shady stuff they've done that they will never admit. Yeah. The optics are not great on that one. This is actually exactly why I had to stop using my COBO airgapped hardware wallet. The public data was being encrypted and I had absolutely no idea what kind of information was exiting the device.
The solution to this problem is to create hardware wallets implementations that aren't grossly centralized to companies and frontend nodes in this manner. Easier said than done obviously, as the way it works now is pretty convenient and considered a "good enough" solution. However we should be well aware that this ecosystem could change at any moment. How much longer until the NSA forces all hardware wallet producers to add in a secret backdoor that nobody even knows about? How do we know this isn't a thing already? We don't honestly.
Ultimately what needs to happen is that we develop air-gapped end-to-end encryption that can't be hacked or intercepted because the device sending the messages doesn't have an internet connection or even a USB port. The code must be open source and anyone must be able to boot up their own frontend-api for personal use or to share with others that trust them. Only this level of decentralization is secure enough for the endgame. I have faith we'll get there but it might take a while. Perhaps when we all have at least a couple million dollars on the line and the stakes are much higher. Wen moon?
Wallets really need to step out of the stone age.
And the hardware wallets are all in that stone age too.
We still don't have a way to make your wallet aware of your will, or the end of your life.
Current plans for recovering the seed phrase by the inheritors are large points of security breaches.
Also, i have not seen any business wallets.
Companies are going to need to spend bitcoin; both lightning and main net.
We don't have anything for authorizing accounting to spend X number of bitcoin/month
or a way to have the boss sign all the "checks"
It is interesting how opaque crytpos are even though most are open source.
People really think that their bitcoin is on their Ledger/Trezor
But, are they really wrong? Without the key, that crypto is lost to the world.
And the whole, send a little crypto first, and then send more to make sure address is correct just doubles the size of the block chain for no real gain. Maybe we need a "test net" to trial send?
We really have a long way to go.
Interestingly enough Hive has a potential solution for end of life transfers as well.
Given a certain trigger an automatic powerdown could be started and the vesting route changed to the beneficiaries.
The trigger could be something as simple as:
Hive really is ahead of the curve in a lot of these regards.
Something like this also stops a user from accidentally losing their keys and all their money along with it.
That is an interesting idea.
I don't even think it would take hard fork.
I like the idea of "powering down" because, it alerts you that the thing has triggered, in case you just spent the last year in the Congo, or under a rock, and forgot, so you can correct it without losing everything.
The addition of named accounts solves a lot of problems, except anonymity.
Compared to HIVE, bitcoin is really in the stone age. And i am thinking that bitcoin will stay in the stone age. When you have something that is basically the savings account of the world, you want it slow and hard to work with. Lightning or Litecoin will handle the real transactions.
Yep
If you care about anonymity the accounts in question could be proxies who's only purpose are the transfer the wealth. Then it's just a matter of bridging that wealth to a privacy solution.
Looks like the world of crypto isn't what we expected it to be...
I use a software wallet and I bet it's the same shit as with metamask.
I guess I forgot to mention how great timelocks are on Hive in conjunction with account recovery.
The system we have going here is very secure and one that most others can't copy.
Yep
That is a great insightful post.
What I wonder is:
What is your best-proposed solution to store large amounts of crypto? Crypto that is to be stored, and rarely needed for something (ie not for trading, spending and whatnot).
What is your best-proposed solution to store larger amounts of crypto that is more practical when using more often, for eg trading, spending and whatnot?
And what about smaller amounts of crypto? Like 1k to 5k$?
I still use hardware wallets all the time.
They are still good enough for now.
The bulk of my Hive sits behind a timelock as HP.
Which is then enforced by account recovery even if my keys get stolen.
That's a pretty good long-term solution and doesn't even require hardware.
Although a hardware wallet could still be used in addition to that security.
Small amounts of crypto can be stored on your phone or even an exchange.
The easiest way to leverage trade is still via centralized exchange.
am not a user of a hardware wallet, but thinking of getting one.
that said...
the other thought I have is to use my employer's laptop, controlled and all by the IT systems in place, as the one holding a new seed phrase wallet for holding my larger funds, a wallet only to be used to tx funds to/from my everyday wallet(s). still something can go wrong on that laptop, but never use this one for crypto stuff, therefore highly unlikely that this laptop is targeted by a keyboard or copy/paste software by crypto stealers. and when they do, its likely detected by the IT filters applied to that solution. and if when its comes in undetected, it is highly unlikely I click a malicious link. Instead of that laptop, I could also use one of my older smartphones I don't use anymore, but I think I prefer my employer's laptop.
regarding hive key recovery. am thinking of something similar. use my employers laptop to create a recovery account I myself control, instead of keeping this in the hands of a 'trusted' third party.
whats your opinion on my ideas? bin material? mucho better to go for a hardware wallet?
true that CEX is better for trading than DEX. through pancakerouter hack, connected to a trusted DEX frontend, a nice amount of funds from my wallet got stolen last november.
Uhm… How do you sign a transaction if you don’t exchange any data with the wallet, or how couldn’t that transferred data contain any exploit?
The amount of data that the device receives is only exactly what it needs.
It's not programmed to do anything with extra data.
The device tells you what it's doing; you sign it (normal HW stuff).
Then it transfers the information to your phone with a QR code.
You then confirm the same information on your phone and broadcast the data to the Internet.
Both your phone and your offline hardware device would have to be hacked with the same exploit in order for this to fail. Seems pretty unlikely, especially if you verified and compiled the code yourself. Anyone without those technical skills needs to acquire the hardware device from an entity they trust (or at least someone who will never have access to their phone). Theoretically you could even have an offline device whose sole purpose is to read QR codes which would make it quite impossible to leak private keys from the device.
Also, you should never acquire a hardware wallet from someone and then also use that person's frontend node to broadcast transaction. This would give the same entity access to both endpoints. In theory such an exploit could still be intercepted and squashed when filtered through the QR code to the phone, so the app on the phone also shouldn't be the same person we get the hardware wallet from.
Regardless of all this I'm grateful to have access to Hive's recovery feature.
This is truly the ultimate oh-shit button that many are taking for granted.
I did not think this through. The phone could get hacked and malformatted transaction could theoretically infect the device and make it produce transactions for the attacker but the return path should filter them out before they are broadcasted. 3 device chain has quite robust security.
I was under the impression that Bip 32, 39, 44 (hierarchical deterministic wallet implementations) have a specific chain based upon hashes of derivation paths to seed phrases and that the wallet just starts from the first entry in the array and assumes after about 5 blank addresses, that there are no more UTXO's to be found in the array.
I remember a warning being given out not skip too many addresses while generating new payment addresses if you wanted the wallet to find those UTXO's and update the total balance.
I mean sure that's how those specific implementations operate, but the larger point was that all these options exist that most people don't even know about. And then those background technicalities create threat vectors that one would never be able to fathom without the initial knowledge.
Hardware wallet = centralization
And will always be...
In theory there is nothing stopping someone from creating a hardware wallet that's 100% under their control.
It would just be very difficult and expensive given the current tech stack.
Easier to outsource that work to a centralized agent at the moment.
Since we entered the internet I think there is no longer privacy, we are exposed to the sale of data, hacking, etc., all wallets do not offer several layers of security but they always find a way to intervene and always have a trace in each operation, for governments cryptocurrencies They have caused million-dollar losses in taxes, so they will always look for a way to intervene and companies will not recognize it, affecting us all.
Yea, I agree... I do see the value in a hardwallet, but also, more inherent risk. I open one day, better solutions will be presented, perhaps bio encrypting with meta brain wave tags or something like that.
Honestly most of us don't have good knowledge or idea about hardware wallets. Thanks for presenting the topic nicely.
I never knew hardware stores' information they shouldn't, and just reading through made me realize why high valued security is needed, like encryption that can not be hacked because it changes every second.
Ledger did make theirs obvious, but what about others? What more information do they own of our privacy that we don't know?
I can't believe that the only thing Ledger gained was bad press after putting ending so many lives and even those of other people, still at risk?
Kind of sad that adequate action is not taken against things like these. Just imagine the amount of crypto wallets that are in jeopardy and the owners don't even know. Decentralisation, like you said,is not so easy to achieve and maybe there's still elements of centralisation in the things we claim aren't centralised.
That's amazing so the hardware wallet stores all of these informations
Thanks so much for the hint
A year ago I purchased a Trezor model T and have never opened the package. Not sure why but my guess is that I don't know what I'm doing lol. Will I ever use it?? Don't have any plans to now lol
How scary!!!, this is f***ing crazy, we lack a lot of decentralization, in all aspects. I need to improve my game ASAP.
Man, I was really digging the new Trezor Safe 3.
What cracks me up about these so called "hardware wallets" is that whole time they've had some software components in there, lmao, talking about another misdefinition of what really is in crypto, where does it end?