This Week I am allowed to join a training session about IT Security.
Here are my notices and thoughts, that I got during the sessions:
SQL-Injection
"Sqlmap" is a SQL-injection script that scans the vulnerability of the server.
It can deliver the versions of the participated software (Apache version, operation system,…) and shows other open doors. Sometimes even a shell is possible.
Cross-Site Request Forgery (CSRF)
CSRF is an attack that forces users to execute unwanted actions.
When you move your mouse over an infected blog entry, it is possible, that the evil author of this blog does something with your credentials. (I.e. write a blog with your account).
Clickjacking
A invisible frame is laid under the mousepointer and when you click somewhere in an infected webpage, you get forwarded to another webpage that looks identical. One cannot see the difference in the URL, because some letters look the same (I =l (ie looks like ell)). When you are on the server of the attacker, he can do with you what he wants (i.e. get your password).
HTML5 - Cross Origin Resource Sharing
AJAX: Asynchronous Java Script, that exchanges data between browser and server.
When on a webserver the header "Access-Control_Allow-Origin"is set to "*", then it allows every other servers to use the API. When this header is set false, then the complete website can be hacked. (This has happened with a Bitcoin trade exchange).
Content Security Policy
Restricts which kind of data (styles, images,…) is allowed to import from other servers via AJAX.
It should be worked with whitelists.
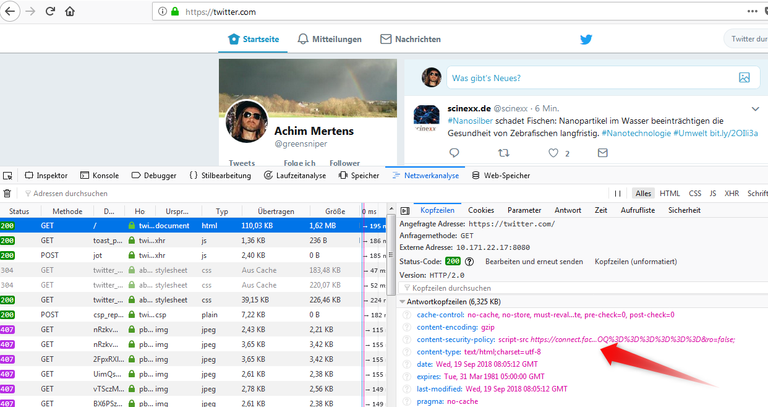
Twitter uses content security policies
By The Way (NoScript)
Facebook has forced other companies to install a tracking pixel. That means, when you open a webpage with this invisible pixel, your data is sent to Facebook, even if you have no account on Facebook. There is a rumour, that Facebook has shadow-accounts of every internet user, independent if they use Facebook or not.
NoScript is a plugin for Firefox.
When it is installed then one can see to which other servers a website tries to open a connection:
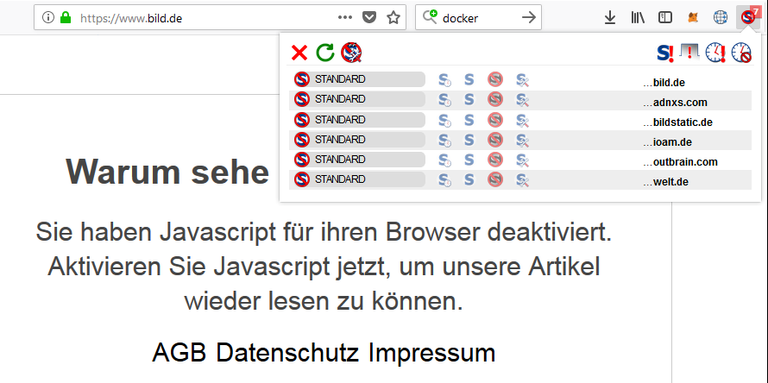
Example with bild.de
Microservices
Microservices are loosely coupled modules that communicate with each other. They are autonomous and can be deployed independent of other services.
But it is very complex and hard to operate.
Philosophie: "Do one thing and do it well", fine grained services, embrace failure,…
In the API Gateway a lot of security features can be installed:
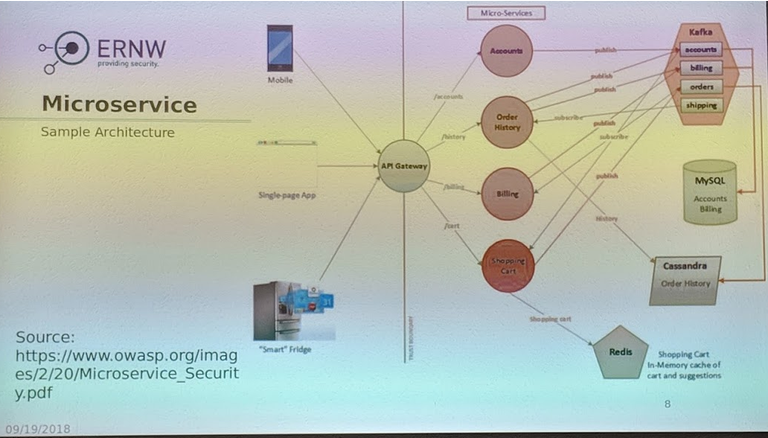
Microservices and API-Gateway
OAuth
Oauth is an open protocol to allow secure authorization in a simple and standard method from web, mobile and desktop applications.
It bases on https.
Some terms:
- Resource Owner is the user
- Resource server is the server that contains the contacts
- Client - Application Server
- Authorization Server
A user accesses a website (Application Server), that asks for access to another server (Authorization Server). Then she logs in into that other server (i.e. google.com) and allows the first server (client) to use this session. It is then enabled (for a given time) to implement the data from Google into the first server.
OpenID Connect
- Identity layer on top of Oauth
- ID-Token - Standard Claims
- https://demo.identityserver.io
- Advantage: Microservice Web Applications are possible
JSON Web Token (JWT)
JSON Web Token is a compact URL-safe means of representing claims to be transferred between two parties. (wiki)
Google, twitter, Facebook,… uses it.
Jtokens are convenient but another possible door for insecurity.
Claims are groups of trust.
Most Common Vulnerabilities
See https://www.cvedetails.com
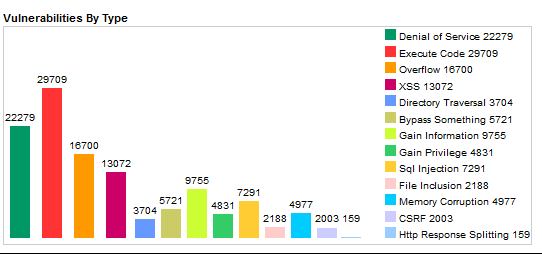
overall vulnerabilities of the last 19 years, https://www.cvedetails.com/vulnerabilities-by-types.php
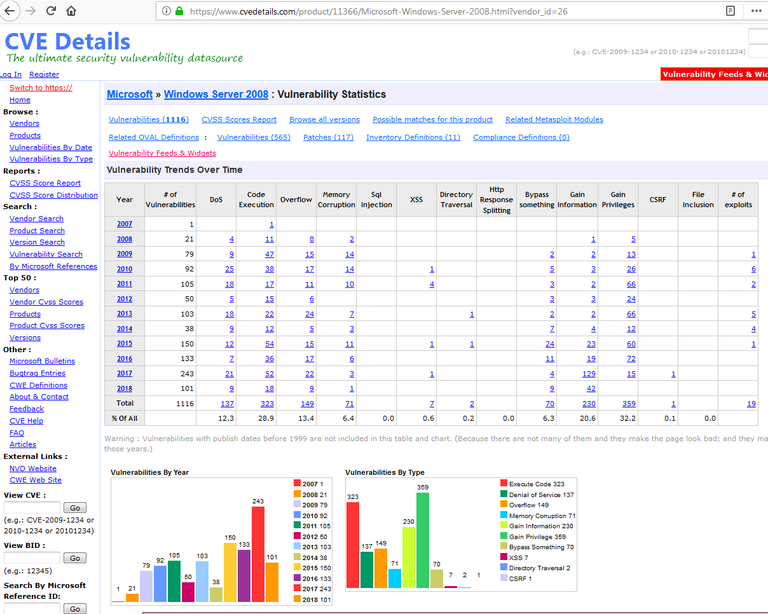
Vulnerability Statistics of Microsoft Windows 2008 in the last 12 years
Some more statistics: https://www.shodan.io/report/89bnfUyJ
SOAP & WSDL
SOAP: Simple Object Access Protocol, XML based, defines APIs with WSDL files.
WSDL: Web Service Description Language.
Webservices are represented by an URI.
WS are independent of the protocol, have open standards and are independent of programming languages.
But it enhances complexity, network traffic and security leaks.
WS-Security defines some security features.
REST
Is an alternative to SOAP
Rest has resources that are addressable.
Representational State Transfer (REST) is an architectural style that defines a set of constraints to be used for creating web services. (wikipedia)
It can use Webservices, JSON, …
For example, a traditional URL looks like …/username=xxx&link=yyy -> with REST it looks like …/xxx/yyy
JSON
JSON is a language-independent datachange format. It was derived from JavaScript. (Wikipedia)
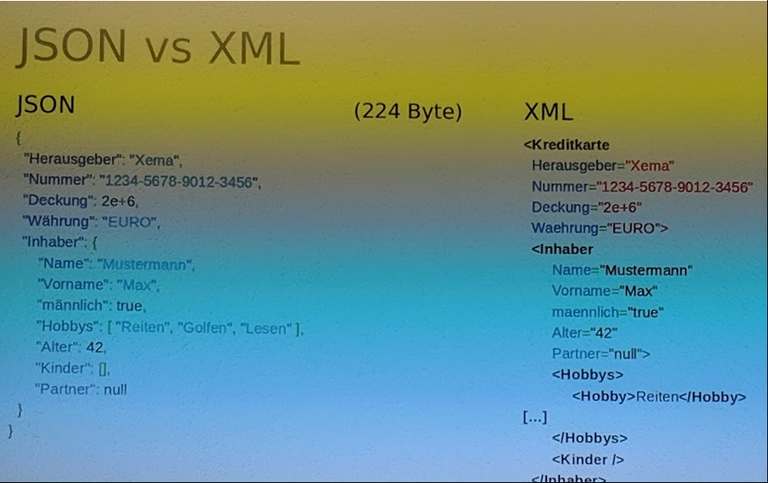
JSON vs xml
For more details see https://www.json.org
Example of a json webservice
When you click on https://venmo.com/api/v5/public?limit=10 you can see clear data from peoples account-traffic.
The page https://publicbydefault.fyi/ has done some data collection from it and demonstrates what we can see from some people. This is an example of a user, that asserts on facebook, to be a healthy person. But her public viewable data shows the opposite:
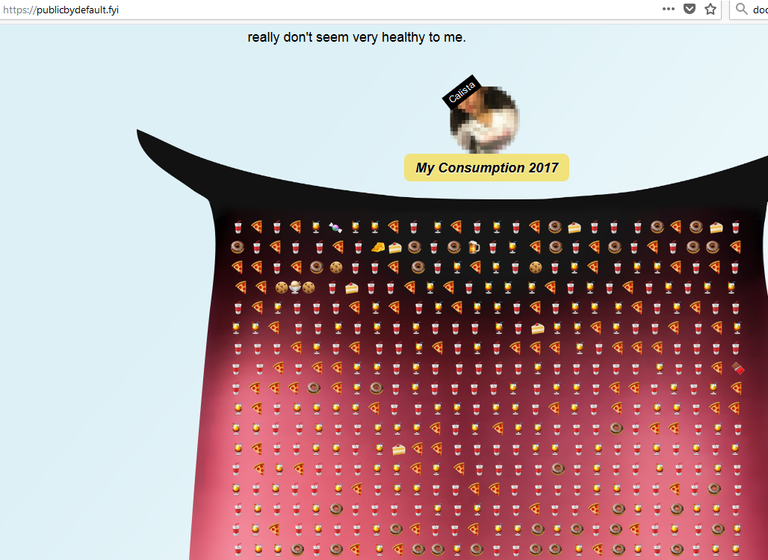
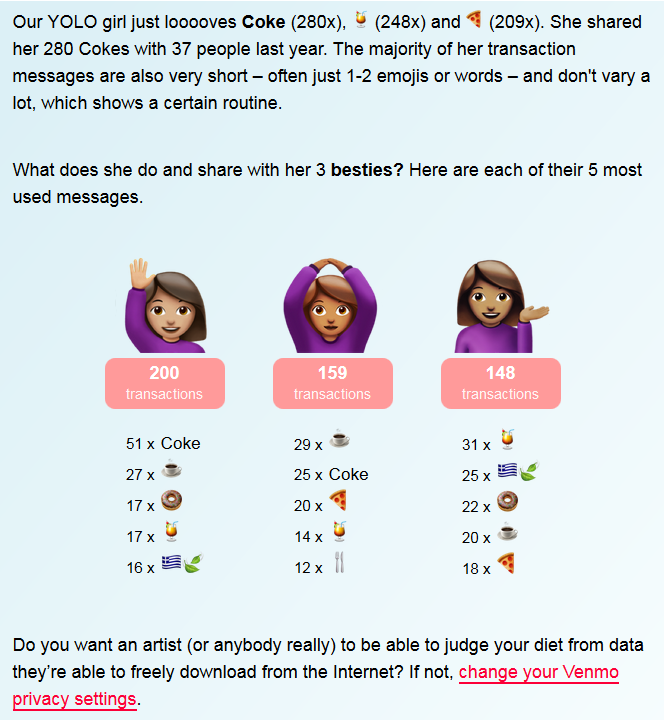
The meal-profile of a user from Venmo
Timing Attack
When you send a request to a server with a wrong signature, than the server sends an error back. But the time differs depending how many bytes from the signature are wrong. An intelligent algorithm is able to try very often to change the signature and learns by doing (similar to the game "Mastermind"). At the end it is able to estimate the right signature.
Web Application Firewall (WAF)
The WAF works against insecure Application with maybe already known vulnerability, works with white- and black lists
It can be bind into the network with network monitors, Layer 2 Bridges, Reverse Proxy or server based.
Some words to the hotel and people here
Yesterday evening I went in front of the hotel were some colleagues sat on two benches with several boxes of beer. It was a warm late summer evening so I sat to them. We talked and laughed a lot. I went to bed late and today I had a little hangover ;-) but It was worth it (Networking is very important ;-))
This evening we are going to have a party, so the challenge goes on.
Here are some pictures from our area:


Regards, Achim
I followed and up votes you. please followback @huanmv