some information About ransomware attack by the BBC
for more info please here is the original link
be aware don't open unknown files or emails be safe
http://www.bbc.com/news/technology-40416611

Companies across the globe are reporting that they have been struck by a major ransomware cyber-attack.
British advertising agency WPP is among those to say its IT systems have been disrupted as a consequence.
Ukrainian firms, including the state power company and Kiev's main airport were among the first to report issues.
The Chernobyl nuclear power plant has also had to monitor radiation levels manually after its Windows-based sensors were shut down.
Experts suggest the malware is taking advantage of the same weaknesses used by the Wannacry attack last month.
"It appears to be a variant of a piece of ransomware that emerged last year," said computer scientist Prof Alan Woodward.
"It was updated earlier in 2017 by the criminals when certain aspects were defeated. The ransomware was called Petya and the updated version Petrwrap."
WannaCry and the malware hall of fame
WannaCry: What can you do to protect your business?
Cyber-attack: Is my computer at risk?
WannCry: Your questions answered
Andrei Barysevich, a spokesman for security firm Recorded Future, told the BBC that it had seen the malware for sale on many forums over the last 12 months.
"It only costs $28 (£22) on the forums," he said. "But we are not sure if they used the latest version or a new variant of it.
Mr Barysevich said the attacks would not stop because cyber-thieves found them too lucrative.
"A South Korean hosting firm just paid $1m to get their data back and that's a huge incentive," he said. "It's the biggest incentive you could offer to a cyber-criminal."
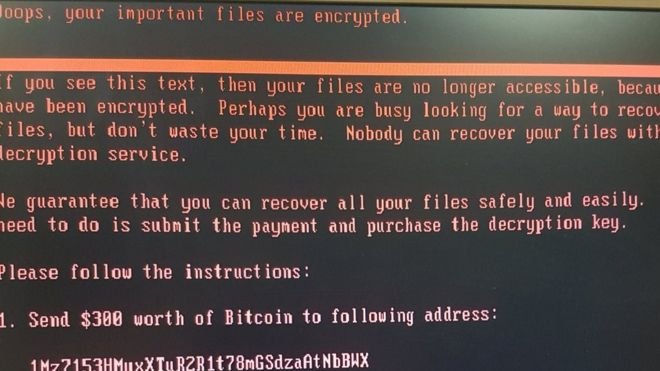
A bitcoin wallet associated with the outbreak has received several payments since the outbreak began. The wallet currently holds 1.5 bitcoins - equivalent to $3,500.
Network down
Others reporting problems include the Ukrainian central bank, the aircraft manufacturer Antonov, and two postal services.
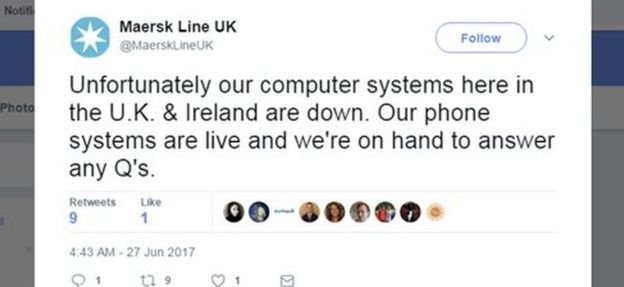
Russian oil producer Rosneft and Danish shipping company Maersk also say they face disruption, including its offices in the UK and Ireland.
"We can confirm that Maersk IT systems are down across multiple sites and business units due to a cyber-attack," the Copenhagen-headquartered firm said via Twitter.
"We continue to assess the situation. The safety of our employees, our operations and customers' business is our top priority."
Spanish media reports that the offices of large multinationals such as food giant Mondelez and legal firm DLA Piper have suffered attacks.
And French construction materials company St Gobain has said that it had fallen victim.
The attacks come two months after another global ransomware assault, known as Wannacry, which caused major problems for the UK's National Health Service.
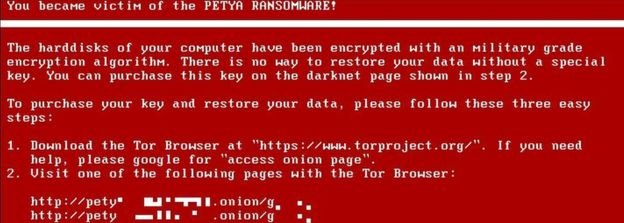
What is Petya/Petrwrap?
By: Prof Alan Woodward, University of Surrey
Petya is a type of ransomware that appeared in early 2016 and returned to a trick first seen in the early 1990s, whereby criminals do not encrypt all the files on your computer but instead they attack a part of the operating system called the Master File Table (MFT).
The MFT is essential for the system to know where to find files on the computer, so it has the same effect as if each file had been locked separately.
The big difference is that it is very much faster to attack the MFT than to encrypt each file separately.
In early 2017, a new form of Petya, dubbed Petrwrap, emerged which built on Petya but it corrected some of the weaknesses in the original code that allowed security companies to help people unlock their systems.
Whilst Petrwarp is detectable by antivirus checkers, if it manages to gain a foothold before it is stopped its encryption is so strong that you are unlikely to be able to break through to recover your files.
Now it appears that whilst the initial attack is probably still via something such as an infected spreadsheet arriving in an email, it can spread, at least in part, across a network using what appears to be the same weakness as was used in the Wannacry ransomware outbreak.
No defence
Veteran security expert Chris Wysopal from Veracode said the malware seemed to be spreading via some of the same Windows code loopholes exploited by Wannacry. Many firms did not patch those holes because Wannacry was tackled so quickly, he added.
Those being caught out were also industrial firms that often struggled to apply software patches quickly.
"These organisations typically have a challenge patching all of their machines because so many systems cannot have down time," he said. "Airports also have this challenge."
Copies of the virus have been submitted to online testing systems that check if security software, particularly anti-virus systems, were able to spot and stop it.
"Only two vendors were able to detect it so many systems are defenceless if they are unpatched and relying on anti-virus," he said
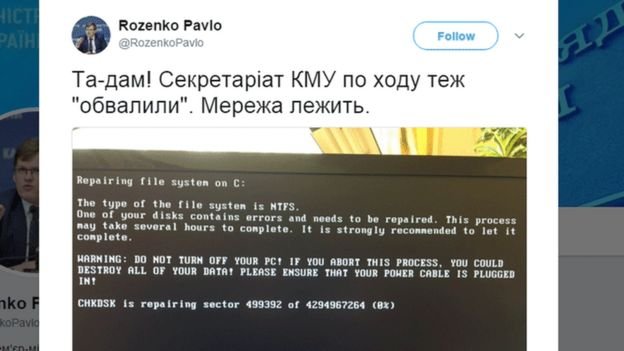
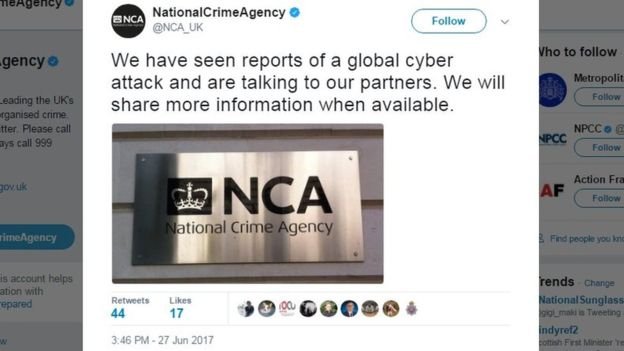
Ukraine seems to have been particularly badly hit this time round.
Reports suggest that the Kiev metro system has stopped accepting payment cards while several chains of petrol stations have suspended operations.
Ukraine's deputy prime minister has tweeted a picture appearing to show government systems have been affected.
His caption reads: "Ta-daaa! Network is down at the Cabinet of Minister's secretariat."