BTC Review | PART 02

Read Part 01
Bitcoin Security

Its practical or theoretical use has been considered as a possible attack and payment method in the Bitcoin network. There are some features of the Bitcoin Protocol that can prevent unauthorized attacks like unauthorized costs, double costs, bitcoin frauds and blockchain tempering. Users need enough caution in other attacks, such as stealing personal keys.
Unauthorized expenditure
With the implementation of public-private key cryptography, the amount of unauthorized expenditure can be reduced. For example, when Elise sends Bitcoin to Bob, Bob is the new owner of Bitcoin. If someone named Eve can see the transaction, he might want to spend the bits received by Bob, but he cannot sign the transaction if he or she does not know what is private.
Dual expenditure
The problem that must be resolved on the internet payment system is "double spending", where a user gives the same bitcoin to two or more customers. For example, such a problem will arise if Eve sends the same bitcoin first Alice and then sends Bob. To protect against double exposure, the Bitcoin Network records all Bitcoin transactions in an account (Blockchain) which is visible to all users and ensures that the bits used are never spent before.
Race Attack
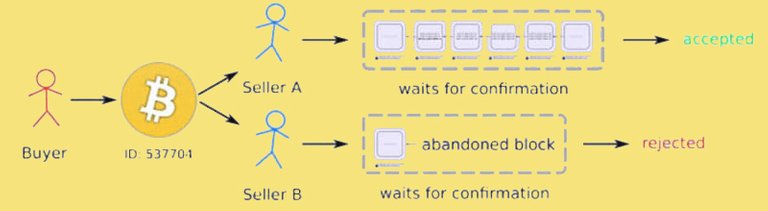
If Eve gives Elise the money in exchange for a commodity and also sign contracts for the transaction, at the same time it can arrange for the same bitcoin to send to Bob. According to the rules, the network will only accept a transaction. This is called a "race attack" because there is a race competition about which transactions will be accepted before. Alice can reduce the risk of race attacks by imposing this condition of the contract, that unless they make payments in Blockchain, they will not be able to deliver the product.
History changes
There is a block containing the transaction information given at the beginning of every block added to Blockchain which is called the approval of that transaction. In the typical case, before accepting the payment, the business and services that accept payment through Bitcoin should wait for at least one approved distribution network. If a trader waits for more approval, it is also difficult for an attacker to reverse the blockchain transaction - unless the attacker brings more than half of the total network capacity, ie 51% attacks.
Deanimization of Clients
For data mining, Deanimization is a technique by which the anonymous data is matched to other data sources to be re-indexed. An analysis of transaction graph analysis (which may reveal connections between Bitcoin's pseudo-addresses) may also be an attack that may alter the user's pseudonym with its IP address. If the peer connection uses "tor", it is attacked in a way that the tire network Peer connections are disconnected, then for the next transaction, their actual IP is locked to use force to another. Such attacks may also mislead Bitcoin's peer address and anti-dose protection transmission methods. Costs less than € 1500 per month for attacks on a complete Bitcoin network.
Payment verification
In each block, there will be no transactions, and not every miner can determine. The number of transactions in a single block is not equal to the higher level of computational power required to solve the block.
After receiving a new transaction information, a node must verify it; Especially the transaction has to be sure that no input has been spent before. Then, the nodes needed to access the blockchain are also to be checked. If a user cannot rely on the neighbors of his network, then he must keep a full copy of the blockchain, as any input can be verified.
As the white paper in Nakamato is written - it is possible to verify Bitcoin payment (which is called simplified payment verification) without a full network node. In this process, a user's longest chain block headers require only a copy - to find network nodes until they get the longest chain. The 'Marcol' branch is then connected to the fixed block by linking it. In relation to linking the transaction in the chain, it is understood that the network node has accepted it, and the added blocks are further guaranteed.
Blockchain Data
The blockchain is possible to store any digital files - the size of the transaction is as big as the size of the transaction, the more the amount of the relevant fee. Various types of content - Child pornography from URL, ASCII art image of Ben Bernanke, Any content of WikiLeaks cable, Bitcoin miner's prayer and original Bitcoin can be rooted in white paper.
Criminal activity
The use of Bitcoin for criminals has attracted the attention of the regulator, lawmaker and enforcement agencies and the media. In this regard, the FBI has created an intelligence assessment, the SEC has issued a warning message about the investment process using virtual currency, and in the US Senate in November 2013 a virtual currency the hearing was held.
Several news organizations have claimed that the increase in the popularity of Bitcoin increased the opportunity of purchasing illegal goods. In 2014, researchers from the University of Kentucky found strong evidence that the encouragement and illegal activity of computer programming increased the attraction of Bitcoin They are limited or free to use Bitcoin for political and investment purposes Did not find relief support.
Black market

According to a CMU researcher, in 2012, 4.5% to 9% of Transaction London-based drug trade operates on a single web drug market. Black marketing sites have complaints of child pornography, mercenary murders and arms bits for sale. Because the sites are anonymous and lacking central control in this market, it becomes difficult to know whether these services are really real or difficult to take bits.
Various authorities have blocked the black market of some deep web. In 2013, the US law enforcement agency closed Silk Road - thereby reducing the price of Bitcoin for a short time. In 2015, the founder of the site was sentenced to life imprisonment. But alternate sites were available in a while because in the first half of 2014 the Australian Broadcasting Corporation reported that the closure of the Silk Road has made little impact on the online drug trade of Australians, but the amount of drug sales has increased.
In early 2014, the Australian Broadcasting Corporation reported that the closure of the Silk Road has made little impact on the online drug trade of Australians, but the amount of drug sales has increased. In early 2014, Dutch authorities closed the online market of illegal goods, Utopia and confiscated 900 bits. At the end of 2014, at the end of a joint police campaign, the authorities of Europe and America confiscated many Bitcoins and closed 400 dip websites, including the illegal goods market, Silk Road 2.0. Several such criminals were sentenced due to such activities of law enforcement agencies. In December 2014, Charlie Sharm was imprisoned for two years for indirect help to send 1 million dollars to the drug trading site Silk Road. In February 2015, Silk Road founder Ross Woolbrich was convicted of the drug trade - he was sentenced to life imprisonment.
Some black marketers may betray bitcoins from customers. Bitcoin identified a site called Community Ship Marketplace as a fraud. After the site has been accused of stealing Bitcoin, the way to lift Bitcoin is blocked and closed. In a separate incident, in the first half of 2014, due to ownership of several black market patrons, Bitcoin escrow accounts were hacked.
According to a UK-based charity, the Internet Watch Foundation reports, Bitcoin is used in child pornography business; about 200 websites accept Bitcoin as a payment medium. But Bitcoin is not the only means of online child pornography. In this regard, O'Reouling, chief of the cybercrime unit of Europol, said, "UCash and Pasephcard ... are also used to pay for such materials." However, the Internet Watch Foundation lists about 30 sites that only accept Bitcoin. Some of these sites have been closed, including the Crowdfunding website of the Deep Web which aims to raise money for new child pornography. Furthermore, when transactions are done, the hyperlink of the child porn website is added to blockchain as a free database.
Money Laundering
Bitcoins may not be ideal for money laundering because all transactions are made publicly. Different authorities such as the European Banking Authority, the FBI and the Finance Action Task Force of G Seven have expressed concern that bid quotes may be used for money. In early January 2014, US Bitcoin Exchange operator Charlie Sharm was arrested for money laundering Later; he was sentenced to two years in prison for the "help and support of the unpaid money transfer business". On July 25, 2007, BTC-e's so-called owner Alexander Vinik was arrested in Greece for allegedly laundering $ 4 billion in money laundering laws, violating US law laundering laws. According to a report titled "UK Money Laundering and Risk Assessment of Terrorist Financing" from the treasury and home office of the UK, it is found that Money Laundering is the lowest risk of using bitcoin and its use as the most common means of money laundering as banks.
Ponzi Project

Between 2011 and 2012, a Ponzi scheme or fraudulent scheme About 7 lakh bits of coins are collected by investors, making promises to profit up to 7% a week. In July 2013, the US Security and Exchange Commission accused the company and its founder of "cheating with investors in the PNG scheme of bitcoinss". In September 2014, Judge Bitcoin Savings and Trust and his owner fined $ 40 million.
BTC Review-Part 01
Upvote, Resteem & Reply for Stay With US click here
Thanks All Crypto Lover
Source
#introduceyourself/#introducemyself
The “introduceyourself/introducemyself” tag is for creating one introductory post that tells us about you. Users are encouraged to use this tag exclusively for that, and not to reuse it.
More information:
The Game of Tags
Welcome to Steem @nbadolsm.
Do read A thumb rule for steemit minnows - 50:100:200:25 for starter tips.
Spend time reading Steem Blue Paper to know how Steem blockchain works and if you still have any queries ask them on our Ask me anything about Steemit post and we will try to answer that.
All the Best!!!
Welcome to Steem, @nbadolsm!
I am a bot coded by the SteemPlus team to help you make the best of your experience on the Steem Blockchain!
SteemPlus is a Chrome, Opera and Firefox extension that adds tons of features on Steemit.
It helps you see the real value of your account, who mentionned you, the value of the votes received, a filtered and sorted feed and much more! All of this in a fast and secure way.
To see why 3438 Steemians use SteemPlus, install our extension, read the documentation or the latest release : SteemPlus 2.20: Utopian + SteemPlus Partnership = Bigger upvotes.
Welcome to Steem! Partiko is a fast and beautiful mobile app for Steem and we upvote our users to help them grow! Please feel free to download the Android app here and the iOS app here.
To learn more about us and stay connected with us, please join our Discord server here: https://discord.gg/N7Et97G