Blockchain, mostly known as the backbone technology behind Bitcoin, is one of the hottest and most intriguing technologies currently in the market. Since 2013 Google searches for “blockchain” have risen by 1900%. Similar to the rising of the internet, blockchain has the potential to truly disrupt multiple industries and make processes more secure, transparent, and efficient. Entrepreneurs, startup companies, investors, global organizations and governments have all identified blockchain as a revolutionary technology. Lots of industries organizations have been exploring how they can harness blockchain to transform their businesses, enable more efficient markets, or create new products and services. However, due to the inadequacies of the blockchain system, this feat is yet to be achieved. Challenges such as scalability, large energy consumption, high technical difficulties and anonymity related issues have been implicated in drawbacks for massive adoption of the blockchain system by the above mentioned sectors. Due to the anonymous nature of some blockchain such as bitcoin, it is being used to perpetuate cyber-crimes and fraud, thus rendering it less safe for reputable organizations. A responsible factor for this is that existing blockchain system focus on anonymous transactions. To solve these problems of existing blockchain technology and foster its incorporation into legalized sectors, Usechain platform was birthed.
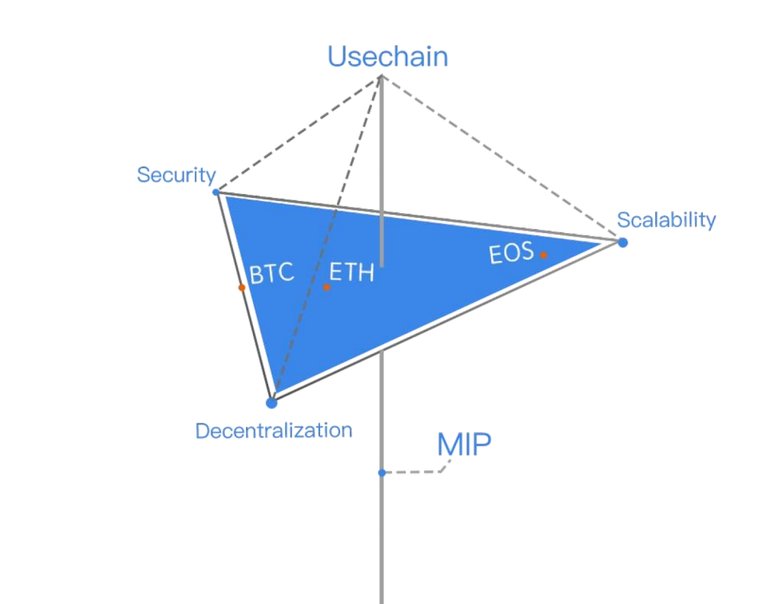
Rather than focus on anonymity on blockchain network, usechain will make use of an identity chain, which is a new system of blockchain based on identification of real users. Addresses in the identity chain will have a verified one-on-one relationship with real users and can be traced back to real people. As a result, the identity chain will positively benefit activities on social media, commercial promotions etc. Another benefit of the identity chain is that since it is based on verification and identification of real users, whenever evil is done by a malicious miner, such transaction will be easier to track down. Apart from verifying their identity, the usechain identity chain also confers protection on users’ privacy.
The identity chain as proposed by usechain is divided into 2 parts:
- The base level chain
- The upper level application
The base level chain focuses on blockchain existing challenges such as slow transaction speed (as seen in bitcoin, ethereum, etc.), wastage of computational resource, low network. To solve these challenges, the usechain proposed identity chain would make amendment to existing features of blockchain technology such as:
• Consensus Mechanism
• Network Sharding
• Block virtual machine
• Light clients
a) Consensus Mechanism: As against the Proof of Work (POW) and proof of stake (POS) algorithm utilized by majority of existing blockchain, usechain will make use of Randomized Proof of Work (RPOW) and Randomized Proof of Stake (RPOS). The use of RPOW and RPOS reduces the centralized effect of hashing power by POW, resisting attacks initiated by 51%, hash power, thus security of the blockchain network will be enhanced. Also, the POW as used by bitcoin requires a lot of computational energy and power without necessarily producing much desired result, hence wastage of resources. With the introduction of the usechain RPOW, there is a reduction in concentration of computing power used by miners, hence reduction in resource wastage while also ensuring that the speed of block transaction is faster.
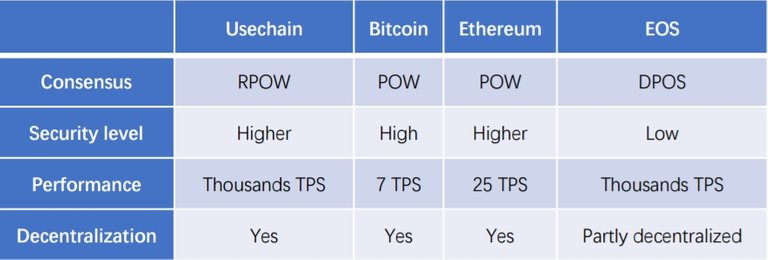
b) Network Sharding: This is an on-chain solution that divides the network into shards. It separates large database into smaller, faster and more easily manageable parts called data shards. Sharding is an on-chain solution that gives linear scalability i.e the more nodes you have, the higher the throughput (the rate at which transactions are processed). Lots of blockchain platform currently have a very low throughput.. However, as the entire network processing is dependent and controlled solely by a few super nodes (nodes in the shards), with an increased volume of transactions, the super nodes get exhausted, thus affecting their speed and subsequently leading to network congestion. With the intervention of identity chain however, each shard will have a corresponding node to process transactions. These nodes collect and package transaction over a period of time in a block, after which it submit to the upper layer for processing. With the user authentication feature of identity chain and ability of identity mirror chain to divide the network into more fragments, there will be an improvement in the network security, as well as an enhancement in the overall processing performance of the network

c) Block Virtual machine: The most commonly used virtual machine in majority of the existing smart contract is the Ethereum virtual machine (EVM). This is the algorithm that powers and run the ethereum platform, often called the operating system of the technology and responsible for running thousands of computing equipment across the world. The EVN helps maintain a decentralized network, ensuring that network is self-regulatory. Its distinct performance ensures consistent uptime, fast transactions as well as high fault tolerance of the network. However, EVM is no longer compatible with present technologies as some downsides are still observed. Existing smart contracts with EVM have low execution efficiency and it requires the use of large quantity of gas when using it to deploy codes and run smart contracts, as a result, writing of codes is difficult as well as expensive. To solve these challenges of EVM, usechain introduces its own virtual machine known as Usechain Identity Virtual Machine (IVM). The EVM will be used in the early stage of usechain project development; however, the later stage of the project will use the IVM. The use of IVM will tackle the shortcomings of the EVM and foster the creation of a high performance smart contract.

d) Light Clients: the light client in bitcoin can download only the header of each block which contains transaction blocks, hash value, time stamp, the difficulty of mining, transaction blocks, random numbers and the root hash value of the Merkel tree. This light client only has the information of a light block header i.e. it has the ability to prove that a transaction occurred, but it is unable to provide the information on the current state such as digital asset balance etc. However, in contrast to the use of light clients nodes, usechain will make use of Merkel - Patricia tree data structure to store transaction information, receipt status, thus, blockchain header would contain the root data of three Merkle trees
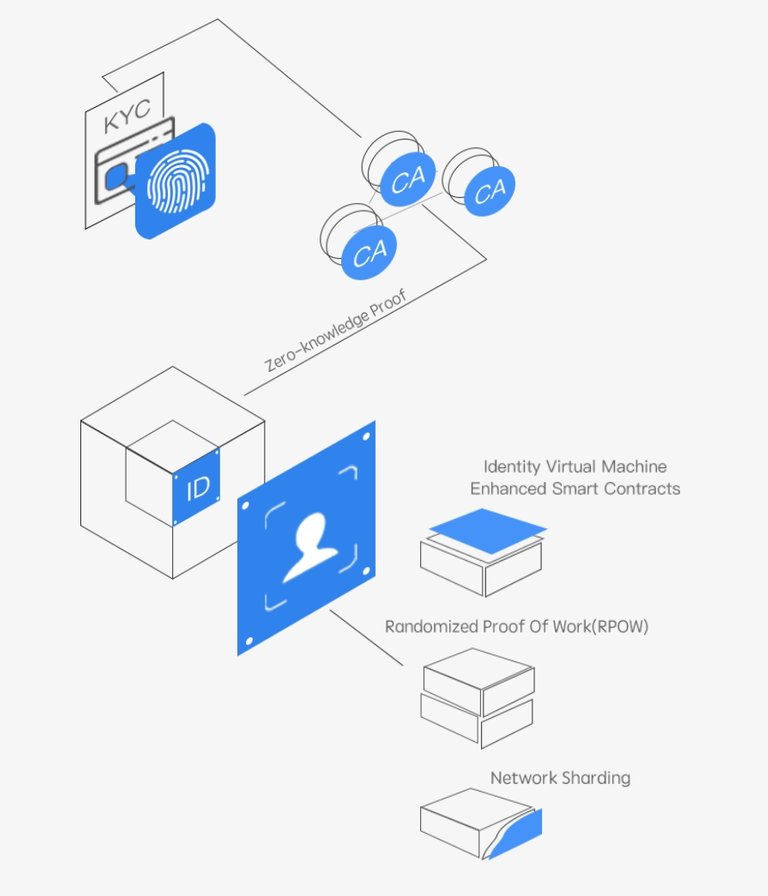
Summarily, with the above mentioned solutions which incorporates the merits of currently existing blockchain into identity chain solutions to build a high performance blockchain system; USECHAIN, it is believed that commercial organizations will be able to harness blockchain technologies into the transformation of their businesses and its benefits will be incorporated into the daily life activities of the general public.
For more information about Usechain, kindly visit:
https://www.usechain.net/ for more information;
Whitepaper: https://www.usechain.net/usechain_en.pdf
Twitter: https://twitter.com/usechain
Facebook: https://www.facebook.com/UsechainFoundation/
Telegram: https://t.me/usechaingroup
Medium: https://medium.com/@usechain/
Author's details:
Username: Crypto4ruby
Bitcointalk profile link: https://bitcointalk.org/index.php?action=profile;u=1788350
Coins mentioned in post: