1. Tools and Techniques for Cognitive Security

Tools and Techniques for Cognitive Security
by SJ Terp & Roger Johnstone
CanSecWest, March 18th 2020
2. Who are These people?

SJ Terp, Pablo Breuer, Grant Dobbe, grugq, Roger Johnston, CogSec Collab Community
3. CogSec Collab: Roots

Credibility Coalition - m!s!nfosec
- Industry
- Academia
- Media
- Community
- Infosec
4. CogSec Collab: 2020 Mission

- bring together information security researchers, data scientists and other subject-matter experts.
- to create and improve resources
- for the defense of the cognitive domain
5. CogSec Collab: 2020 Milestones

- Milestone 1: April 2020
- AM!TT Counters; Who, What, How
- AM!TT Playbook PoC
- Milestone 2: July 2020
- AM!TT Playbook; Public, Social Media, ISPs, Government
- Tooling; Threat Intelligence
- Milestone 3: October 2020
- AM!TT Playbook; refine
- Tooling
- Data Sets
6. COGSEC COLLAB: END USERS

Who uses this stuff anyway?
7. RESPONSE ACTORS
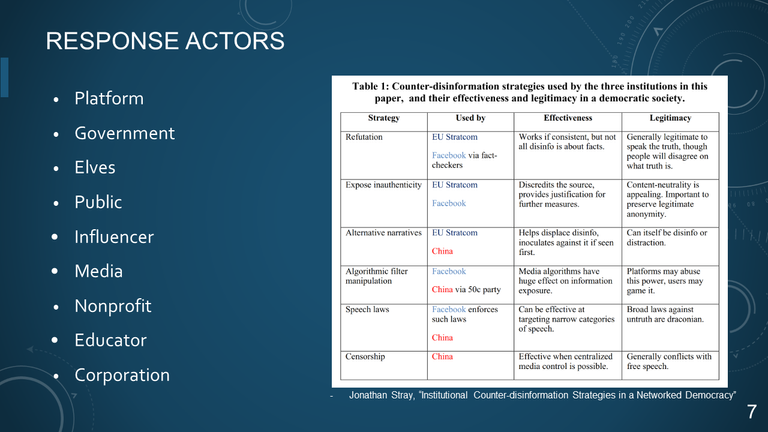
- Platform
- Government
- Elves
- Public
- Influencer
- Media
- Nonprofit
- Educator
- Corporation
8. Elf Communities and Playbooks

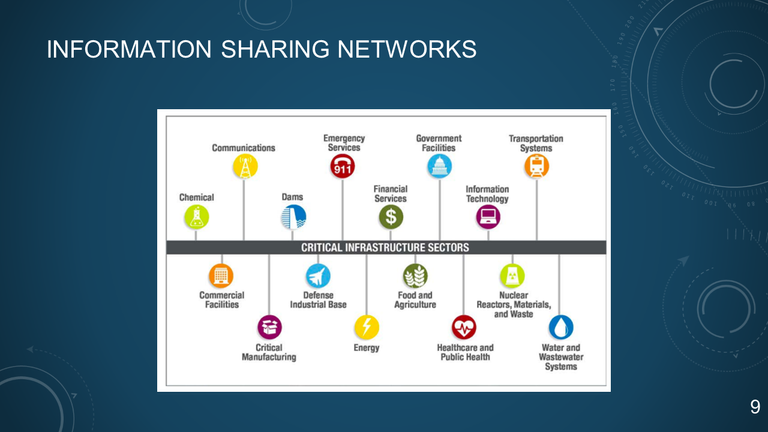
9. INFORMATION SHARING NETWORKS
10. DISINFORMATION LANDSCAPE

The Only defense against the world is a thorough knowledge of it.
-- John Locke
11. DISINFORMATION

deliberate promotion... of false, misleading or mis-attributed information
focus on creation, propagation, consumption of misinformation online
We are especially interested in misinformation designed to change beliefs in a large number of people
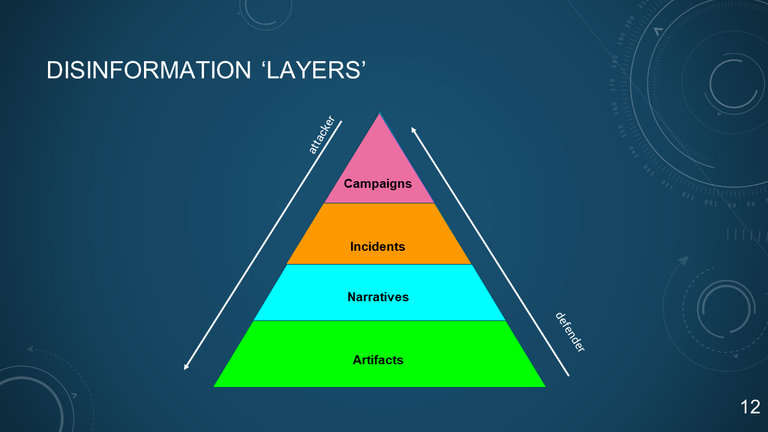
12. DISINFORMATION 'LAYERS'
13. NATIONAL INSTRUMENTS OF INFLUENCE

Resources available in pursuit of national objectives...
Diplomatic, Informational, Military, Economic
...and how to influence other nation-states.
14. BUSINESS INSTRUMENTS OF INFLUENCE
Resources available in pursuit of corporate objectives...
Business Deals & Strategic Partnerships, PR and Advertising, Mergers and Acquisitions, R&D and Capital Investments
15. DESCRIBING DISINFORMATION

AM!TT and other models of WTF is happening
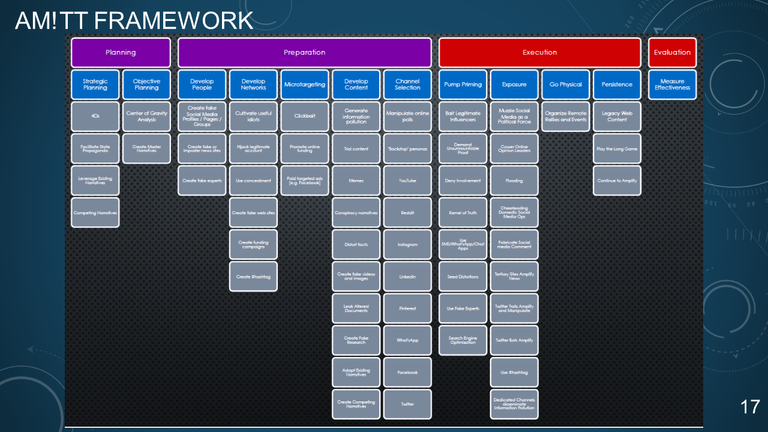
16. AM!TT FRAMEWORK

Adversarial Misinformation and Influence Tactics and Techniques = (AM!TT)
- Credibility Coalition Misinfosec Working Group
- AM!TT is a framework for understanding organized communication attacks
17. AM!TT FRAMEWORK
18. AM!TT - T0010
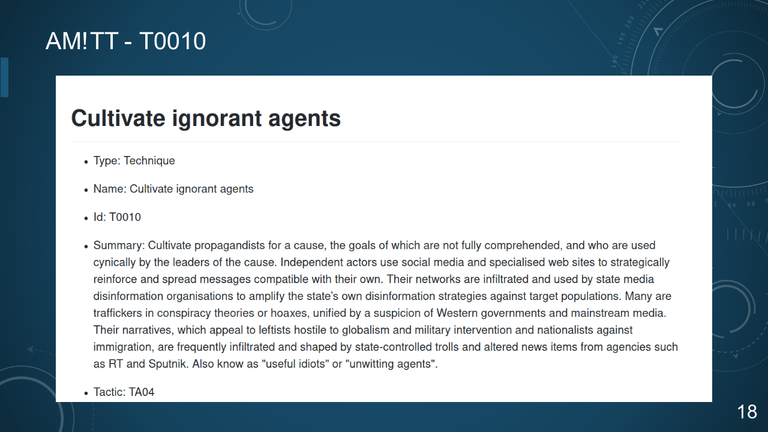
19. AM!TT - T0010

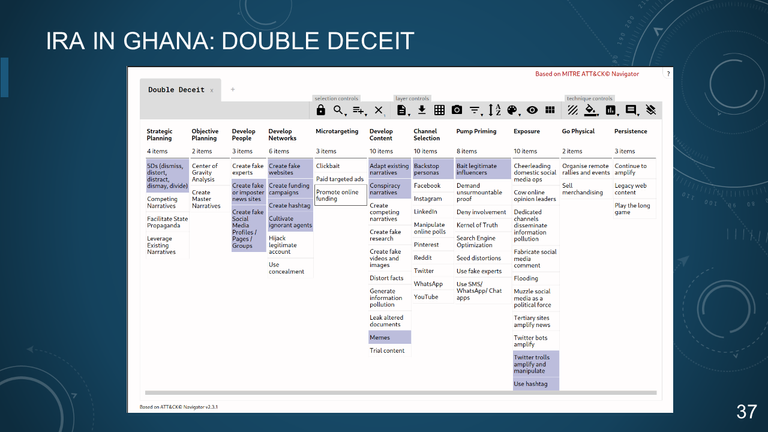
IRA IN GHANA: DOUBLE DECEIT
Cultivate Ignorant Agents
- "EBLA" NGO local staff
- Attempt to co-opt US influencers
20. DISINFORMATION COUNTERMEASURES

Moving from admiring the problem to action
21. MITIGATIONS AND COUNTERMEASURES

Countermeasures are that form of military science that, by the employment of devices and/or techniques, is designed to impair the operational effectives of enemy activity. Countermeasures can be active or passive and can be deployed preemptively or reactively.
-- JP 3-13.1, Information Operations - Joint Chiefs of Staff
22. FINDING COUNTERMEASURES

- Existing
- Tactic-based
- Technique-based
- Doctrine-based
23. EXISTING COUNTERS

24. TACTIC-BASED: COURSES OF ACTION MATRIX
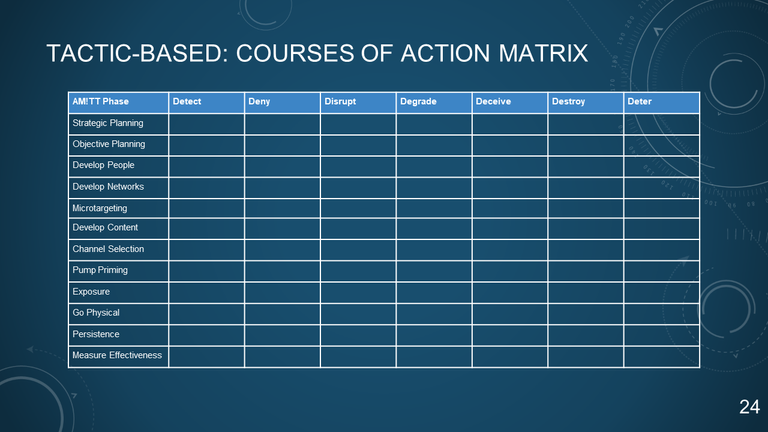
| AM!TT Phase | Detect | Deny | Disrupt | Degrade | Deceive | Destroy | Deter |
| --------------------- | ------ | ---- | ------- | ------- | ------- | ------- | ----- |
| Strategic Planning | | | | | | | |
| Objective Planning | | | | | | | |
| Develop People | | | | | | | |
| Develop Networks | | | | | | | |
| Microtargeting | | | | | | | |
| Develop Content | | | | | | | |
| Channel Selection | | | | | | | |
| Pump Priming | | | | | | | |
| Exposure | | | | | | | |
| Go Physical | | | | | | | |
| Persistence | | | | | | | |
| Measure Effectiveness | | | | | | | |
25. EFFECTS
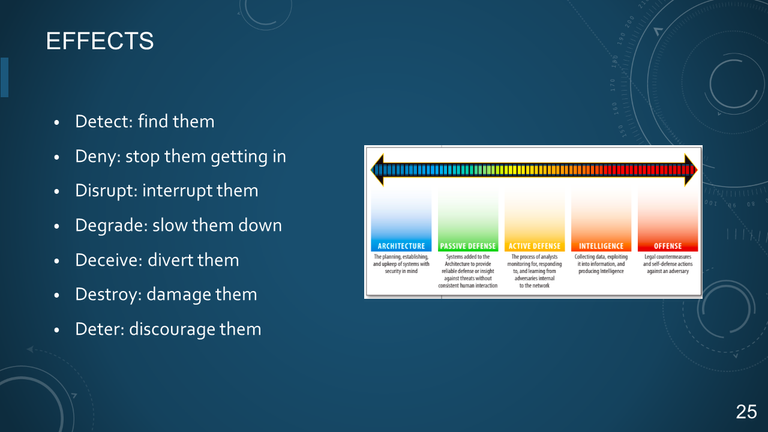
- Detect: find them
- Deny: stop them getting in
- Disrupt: interrupt them
- Degrade: slow them down
- Deceive: divert them
- Destroy: damage them
- Deter: discourage them
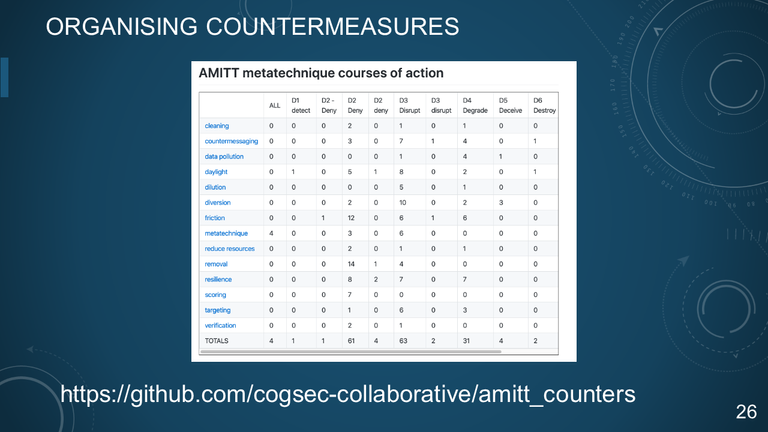
26. ORGANISING COUNTERMEASURES
27. DOCTRINE-BASED COUNTERMEASURES
"A disinformation campaign is made up of resources and infrastructure and operates over time, with them as a universal scarcity."
-- Grugq
28. CRITICAL ELEMENTS

- Resources
- Infrastructure
- Execution
- Time
29. DOCTRINE-BASED COUNTERMEASURES
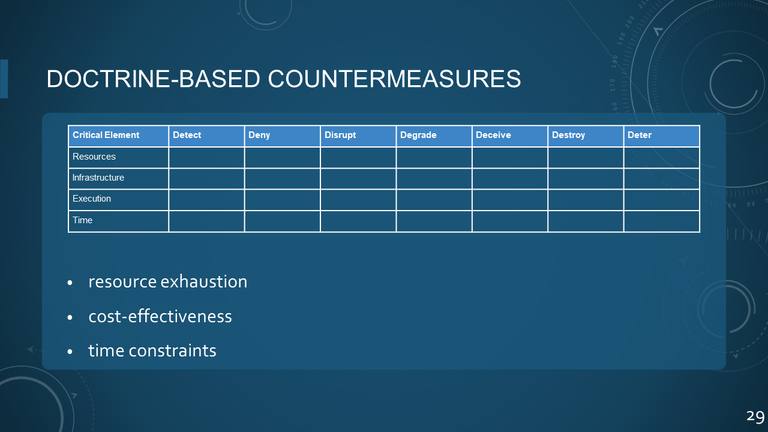
| Critical Element | Detect | Deny | Disrupt | Degrade | Deceive | Destroy | Deter | |
|---|---|---|---|---|---|---|---|---|
| Resources | ||||||||
| Infrastructure | ||||||||
| Execution | ||||||||
| Time |
- resource exhaustion
- cost-effectiveness
- time constraints
30. DOCTRINE-BASED COUNTERMEASURES
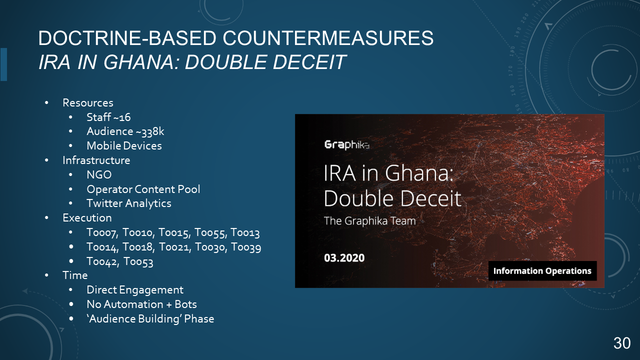
IRA IN GHANA: DOUBLE DECEIT
- Resources
- Staff ~16
- Audience ~338k
- Mobile D
evices
- Infrastructure
- NGO
- Operator Content Pool
- Twitter Analytics
- Execution
- T0007, T0010, T0015, T0055, T0013
- T0014, T0018, T0021, T0030, T0039
- T0042, T0053
- Time
- Direct Engagement
- No Automation + Bots
- 'Audience Building' Phase
31. PLAYBOOKS

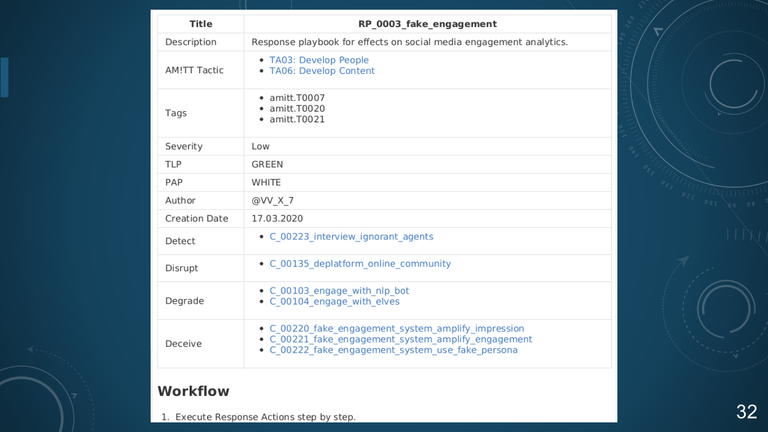
32. RP_0003_fake_engagement
33. THREAT INTELLIGENCE TOOLS AND TECHNIQUES

things we borrowed from infosec
34. OASIS STIX™ 2
- AM!TT needed a standard for data exchange
- Relationships + Rich language
- Extensible
- Intelligence Sharing (ISACs & ISAOs)
- Integration with community tooling
- AM!TT is now available as a STIX 2.0 bundle
35. STIX AMITT
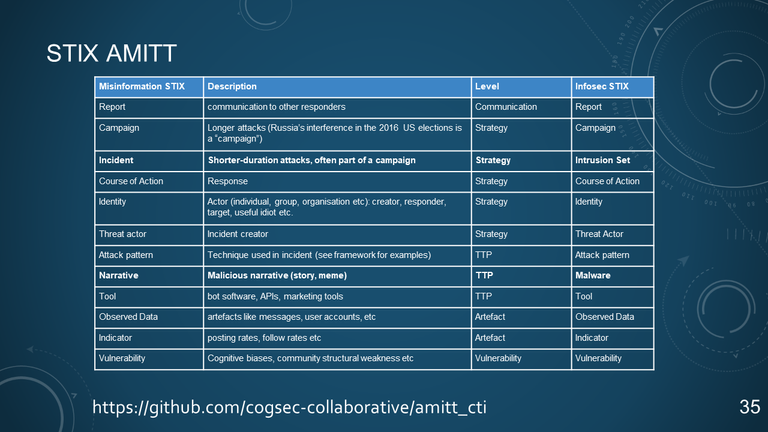
| Misinformation STIX | Description | Level | Infosec STIX |
|---|---|---|---|
| Report | communication to other responders | Communication | Report |
| Campaign | Longer attacks (Russia's interference in the 2016 US elections is a "campaign") | Strategy | Campaign |
| Incident | Shorter-duration attacks, often part of a campaign | Strategy | Intrusion Set |
| Course of Action | Response | Strategy | Course of Action |
| Identity | Actor (individual, group, organisation etc): creator, responder, target, useful idiot etc. | Strategy | Identity |
| Threat actor | Incident creator | Strategy | Threat Actor |
| Attack pattern | Technique used in incident (see framework for examples) | TTP | Attack patter |
| Narrative | Malicious narrative (story, meme) | TTP | Malware |
| Tool | bot software, APIs, marketing tools | TTP | Tool |
| Observed Data | artefacts like messages, user accounts, etc | Artefact | Observed Data |
| Indicator | posting rates, follow rates, etc | Artefact | Indicator |
| Vulnerability | Cognitive biases, community structural weakness etc | Vulnerability | Vulnerability |
https://github.com/cogsec-collaborative/amitt_cti
36. AM!TT + MITRE ATT&CK® Navigator
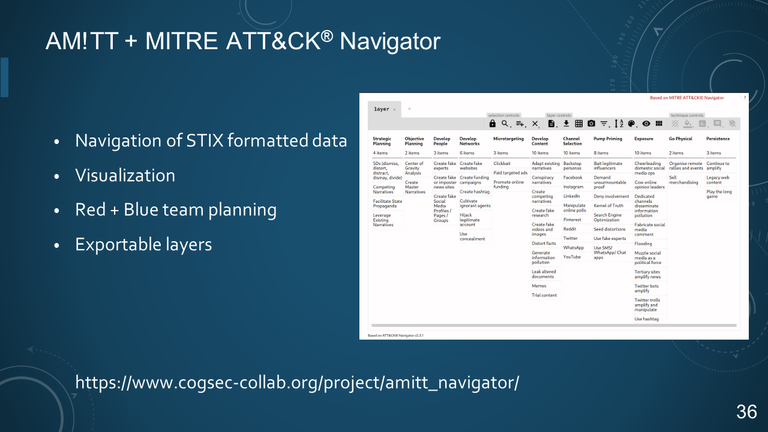
- Navigation of STIX formatted data
- Visualization
- Red + Blue team planning
- Exportable layers
https://www.cogsec-collab.org/project/amitt_navigator/
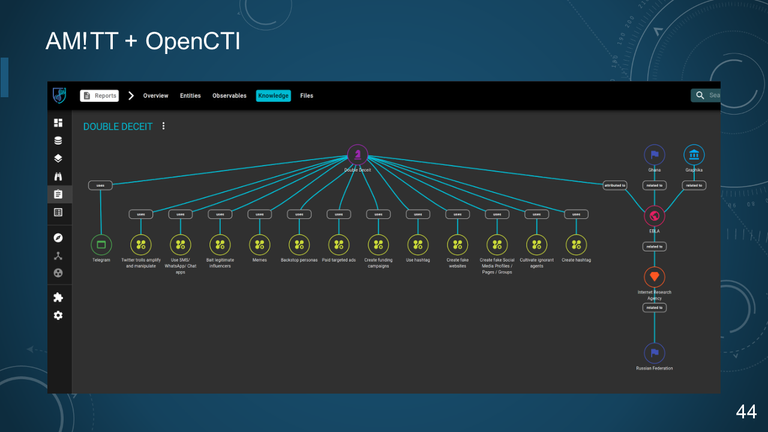
37. IRA IN GHANA: DOUBLE DECEIT
38. MISP - Open Source Threat Intelligence Platform

- Store and share structured data
- Enrichment + Automation
- Open + Extensible
- ISAO + ISAC + Elves
39. AM!TT + MISP
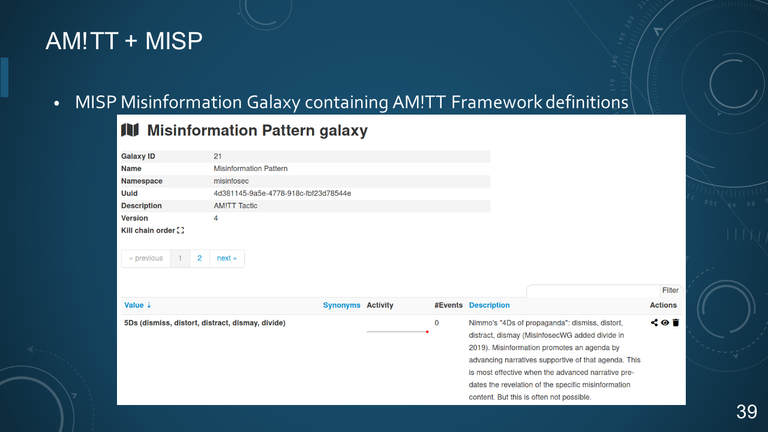
- MISP Misinformation Galaxy containing AM!TT Framework definitions
40. AM!TT + MISP
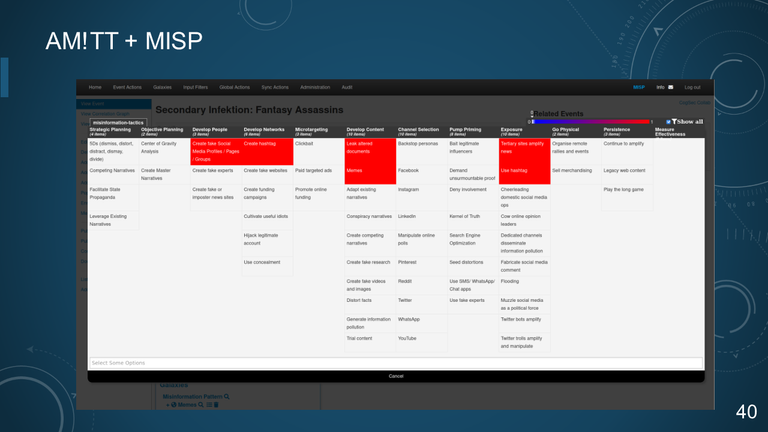
41. AM!TT + MISP
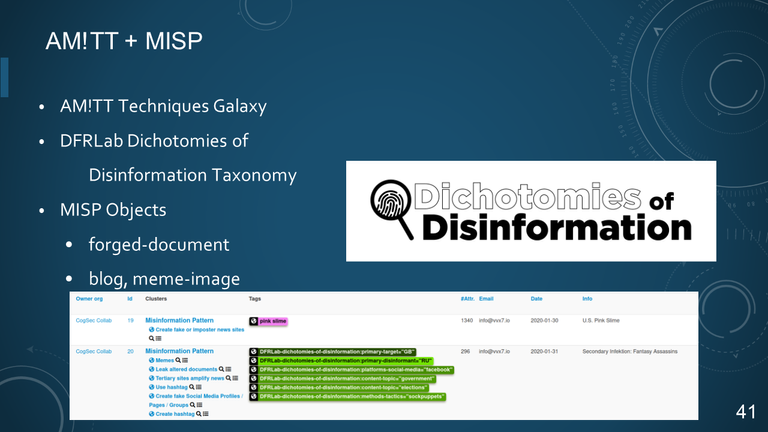
- AM!TT Techniques Galaxy
- DFRLab Dichotomies of Disinformation Taxonomy
- MISP Objects
- forged-document
- blog, meme-image
42. AM!TT + MISP
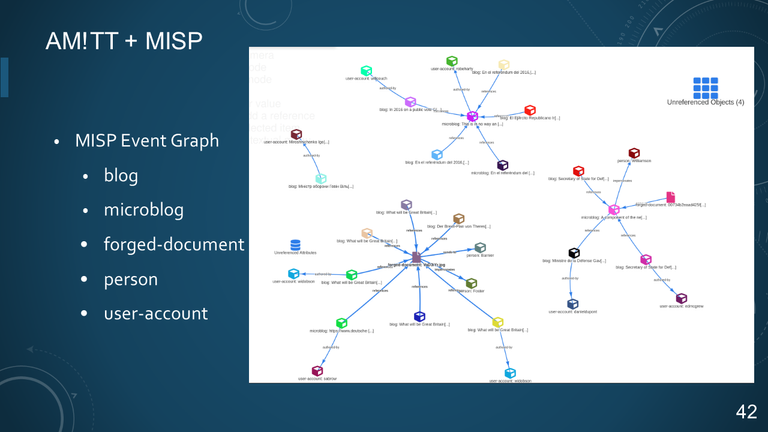
- MISP Event Graph
- blog
- microblog
- forged-document
- person
- user-account
43. OpenCTI - OPEN THREAT INTELLIGENCE PLATFORM

- STIX 2.0
- Knowledge Graph
- Report based
- MISP integration
44. AM!TT + OpenCTI

45. NEXT: AM!TT + Atomic Threat Coverage

- Done: AM!TT Techniques
- Next: AM!TT Counters
- Playbooks are assembled from sets of counters
- Markdown, Confluence, API, ...
https://github.com/atc-project/atomic-threat-coverage
46. COMMUNITY TOOLS AND TECHNIQUES

things we borrowed from data science
47. CogSec Collaborative - AM!TT m!s!nfosec
Join the Elves
CogSec Collaborative helps communities counter disinformation.
48. THANK YOU

CogSec Collab
https://www.cogsec-collab.org
@bodaceacat
@VV_X_7
Fascinating and inspirational examination and consideration of how to free our minds and prevent Machiavellian manipulation of humanity, avoid the malevolent hazards inherent to Space Age technology, and enable absolute freedom prophesied millennia ago, or suffer the twisted hellscapes madmen willing to commit any atrocity intend.
Thanks!
Thanks 2 u too!
Congratulations @aagabriel! You have completed the following achievement on the Hive blockchain And have been rewarded with New badge(s)
Your next target is to reach 37000 upvotes.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOP