
Hello and welcome to this tutorial dedicated to cryptocurrency storage portfolios. Also called wallet, they act as bank accounts, they have a balance and record transactions. Each cryptocurrency has its own wallet, it is not possible to send a currency on a wallet that does not correspond to it. If this happens, the funds will be lost. For example, you should not send Ether to a Bitcoin wallet.
💡 Some tokens can be managed on a single portfolio. This is the case of ERC20 tokens, which can all be stored on a single Ethereum portfolio (like MyEtherWallet for example).
Each wallet is different and has its own characteristics, but it is difficult to make a "global" tutorial as each portfolio has its own characteristics. We will see in this tutorial what is a wallet and the different types of wallet that exist. You can find at the end of our page different tutorials to create a specific wallet.
How does a wallet (wallet of cryptocurrencies) work?
What are the different types of wallets?
Tips for securing your crypto-currencies
Our tutorials for each wallet
How does a wallet (wallet of cryptocurrencies) work?
On a blockchain network, the different transactions are recorded in blocks created at regular intervals (each block contains a certain number of transactions). Reading all of these blocks, you can determine the balance of each account, as in a classic account book. One tends to say that one stores his crypto-currencies on a wallet, but one simply adds a line in a big accounting book. Crypto-currencies never leave the blockchain, they are just assigned to different portfolios depending on the transactions made. Thus, it is possible to send crypto-currencies on a portfolio that has not yet been generated or that is not connected to the Internet.
A portfolio is composed of at least two elements:
The public address is like your name, it is an identifier that you can communicate so that we send you crypto-currencies. It also allows you to view your balance in cryptocurrencies.
The private key is like your password, anyone with this key can move the funds in the wallet.
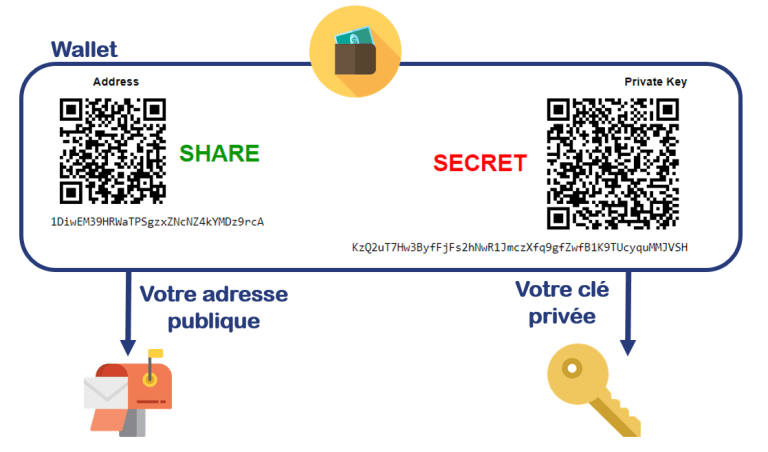
The image above is an example of a Bitcoin wallet (BTC). Most wallets have this format public address / private key, but it may happen that some portfolios add other elements of identifications.
⚠ Beware, there are many scams on the Internet that involve asking you to entrust your private keys. Know that you should never provide your private key to anyone and under any circumstances. Anyone, site or software claiming the opposite lies to you, without any exception and seeks only to appropriate your money. If you ever give your private key, your wallet will be included and your funds will be likely to be moved (and it may not be possible to recover them).
What are the different types of wallets?
Three types of wallets can be considered:
Online Wallet
Desktop Wallet
Cold Wallet
In the rest of this guide, we will review these 3 wallets and see the advantages and disadvantages for each of them.
What is an Online Wallet?
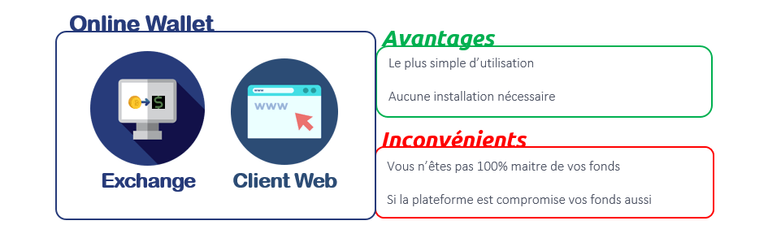
Online Wallets are the easiest to use. They are accessible everywhere and all the time, the management of your crypto-currencies is made by a trusted third party. It can be an exchange like Binance or a specialized platform like Blockchain.info for example.
The exchange offers the advantage of allowing a great reactivity with regard to the purchase / sale of crypto-currencies. Indeed, if your tokens or crypto-currencies are located on an outside wallet (which would not be an exchange), you will first have to transfer your funds on an exchange before being able to resell them. You will not be able to sell quickly and impulsively, and you may lose time transferring your funds.
An Online Wallet is represented by a platform that stores your crypto-currencies, so you are not the actual owner of your funds. You will not have private keys and you will be dependent on the site that owns your money. If it were to close or to be hacked, you could not do much because the universe of cryptocurrencies still lacks regulations and laws on this subject. For this reason, it is strongly recommended to spread your funds across multiple platforms and media to limit risk.
In addition, there are other drawbacks to the use of the exchanges, the transfer fees are often very high to withdraw funds and must respect the withdrawal limits (a maximum amount per day). Some platforms may even block all withdrawals until you have submitted your personal information (Know Your Customer procedure), which may raise confidentiality issues.
These platforms are therefore better advised for short-term operations and for small amounts.
What is a Desktop Wallet?
The Desktop Wallet allows you to store your private key in a device belonging to you. The wallet then makes it possible to interact with the corresponding blockchain. This system does not require the provision of personal information, so you most of the time have full control over the charges for transfers. Here you are the owner of your crypto-currencies.
These wallets have some disadvantages. First, the media on which your private key is stored remains vulnerable to computer attacks. Thus, if your computer is hacked your private key can be stolen by the hacker.
These portfolios require precautions of use. For example, in case of fork of a cryptocurrency, if you do not update your wallet, you can end up sending the bad crypto-currencies on the bad blockchain.
We must also distinguish between "heavy" wallets and "light" wallets. The first (heavy) require download the entire blockchain, it can weigh several gigabytes but has the advantage of allowing to check the integrity of the entire blockchain. The second (light) are usually present on mobile, they are based on only part of the blockchain to check its integrity. There is a risk of sending funds to the wrong blocks.
We advise you to promote the use of Desktop Wallet that are open source and recognized by the community. These criteria make it possible to know if the software is reliable and if it respects the confidentiality of its users (no data hijacking or other).
What is a Cold Wallet?
A Cold Wallet is a wallet that is not connected to the Internet. This gives it the highest level of security for a wallet, since what is not connected to the Internet can not, by definition, be hacked. There are two types of Cold Wallet, paper paper and hardware wallets, these two types of wallets are fundamentally different and are not used for the same purposes.
Paper Wallet
The paper wallet can be generated offline. You then note your public key and your private key on a medium that you put in the shelter. This wallet can then receive the corresponding currency without being connected to the Internet. This is the safest way to keep your crypto-currencies. That said, this type of portfolio also has the major disadvantage of not being able to be used to perform outgoing transfers. To be able to do this, you must import your private key in a wallet (desktop, mobile or web client). And by doing this, you make your private key vulnerable to computer attacks, since it is now filled in software connected to the Internet, so we lose all the security interest.
Thus, to overcome this problem, it would be necessary to recreate a paper wallet with each transfer. Which could quickly prove extremely restrictive.
Click here to see the diagram for creating a paper portfolio
Hardware Wallet
Hardware wallets are devices on which different private keys are encrypted (at least one by supported cryptocurrency), they are regularly compared to digital safes. The most famous hardware wallets are the Ledger Nano S and TREZOR portfolios.
Unlike the paper wallet, these allow transactions to be made regularly and securely. It is even possible to use a hardware wallet on a computer infected with malware without it being compromised. In addition, your crypto-currencies are not stored on the hardware wallet but on a seed phrase (mnemonic sentence) that you will be asked to note. Thus, even if your digital safe is broken, lost or stolen, you have the possibility to find your funds. For this, you will need to import your seed phrase on another device.
The major disadvantage of the hardware wallet is that it requires to spend a certain amount of money (about 100 € for a Ledger Nano S) unlike all other formats of wallets. Also note that not all cryptocurrencies are supported by these hardware portfolios.
The hardware wallet is thus the most secure format for users who make regular transfers.
Below you will find an image summarizing what we have just seen about the different types of portfolios.
Tips for securing your crypto-currencies
In this chapter, you will find tips that will help you to secure your investment in cryptocurrency.
A single email for exchanges
Open a new unique e-mail account for exchanges. Indeed, if you use an e-mai address
informative blog bro..
So much information, but it's good you're able to explain complex issues on a way which is understandable for Rookies too.
Excelente información @easymoney5
Shalom...