The CYBR Ecosystem is holistic; math from component to the full. Via a portal that delivers current safeguards, countermeasures and risk intellect linked with Blindspot, it is entirely proprietary, an active cyber stability engine unit that determines and disrupts bad movie superstar and involved illicit info record activity. It essentially recognizes anything that needs to impact the privacy, sincerity, and availableness of crypto great deal ventures.
CYBR Environment
Identifies and disrupts bettering dangers to blockchain-based positions. CYBR Detects advanced and polymorphic problems that look for to circumvent diagnosis by existing precautions and countermeasures. This platform ensures secure orders with getting small address. Near synchronous supplies of information: surfacing threats, most recent techniques, phishing sites, negative celebrities and extra. Two years of improvement with current merchandise earnings. It can be used to Computerized and scalable. In the society of cyber secureness, connected problems and significant alternatives happen to be frequently detailed in what usually is generally known to as the “hazard brains pyramid of soreness” as revealed: The start steps-initial to a practical cyber secureness choice features four centerpieces: Holistic: features go over in totality, Countermeasures and shields provide you with you with active cover, On time risk id. A quick passageway from information to actionable brains. The Blindspot request and CYBR Web site give the controlled potential to meet these requirements.
Structure And the Two Ingredients of CYBR
The CYBR architecture generally involves two (2) key components: 1. Worldwide Web Site 2. BlindSpot. The CYBR Internet Internet web pages function as the CYBR Network End-user Program (UI) for the Environment solution. It gives an all-natural response that ensures the cyber consistency of brilliant arrangement linked discounts and its risk to safety brains work exceptionally well to bring to the texture of the blockchain. There are countless features and capacities involved with the CYBR Community-wide web Site. At a substantial level, they incorporate 1. Threat Intelligence 2. Verification 3. Token Sending/Finding Efficiency 4. Downloads 5. Support Internet site. These will come to be currently broken down into subset capabilities, which involve: 1. Risks a. New Threat Advisories b. Search Threat Intelligence Databases c. Threat Minds Baby bottles i. CYBR ii. Partner Wine bottles 2. Confirmation 3. Verify Reflection Address 4. Verify Net page 5. Send/Acquire a. CYBR Finances Information c. Send Bridesmaid to get together. 6. Download BlindSpot a. Glass glass windows c. OSX c. LINUX g. IOS age group. Google android os 7. Guide a. FAQ c. Know-how Lower part c. Receive in touch with Us.
CYBR Wallet and details
The CYBR Web site also offers a proprietary CYBR Billfold, which incorporates a Token Name Assistance (“TNS”). The extraordinary TNS feature curbs and minimizes standard general population takes up to prevalent labels. This equipment users the potential to mail a wedding get together to consider vetted people and entities without the matter of sending to inaccurate or phony specifics. The wallet likewise features a cosmetic identification and biometric (fingerprint) capabilities, which enables smart contract orders (post/receive) to appear without the need to enter the individual vital or the incorporation of a mask (e.g., Metamask). Personally take a moment to happen to be NEVER sacrificed when taken out in this design. Hackers exhibit and work with a variety of gear and approaches to gain and maintain gain access to crypto and related engaged units. The just about all distinctive and robust approach is certainly advanced constant perils. As specific out previously, APTs work with vulnerabilities in devices that typical cyber consistency alternatives will get ill-equipped to bundle with. Hackers can today definitely camouflage their equipment by changing known to malware signatures into unique data files. Without related to names, this polymorphic malware invasion a push in practically all current info data file diagnosis devices, giving businesses available to exploitation. Traditional signature-based products easily cannot come to be affordable; They happen to be forecasted to obtain directly just about 25 percent successful in heading up against with APTs.
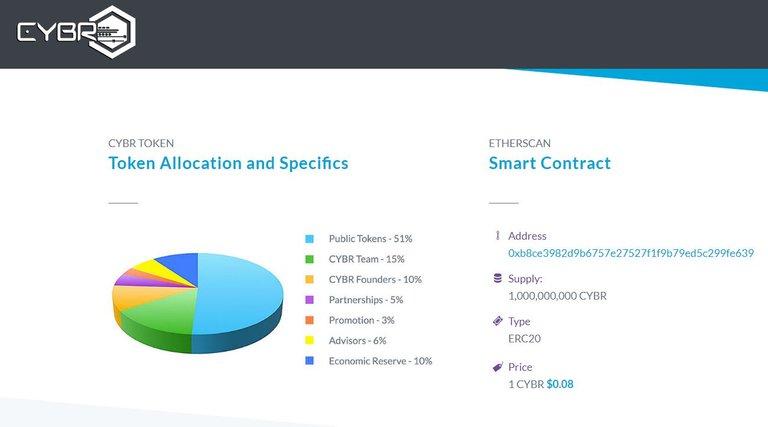
| ICO NAME | CYBR |
|---|---|
| Website | https://cybrtoken.io/ |
| WP | https://cybrtoken.io/wp-content/uploads/2018/09/cybr-whitepaper.pdf |
| https://twitter.com/CYBR_Official | |
| https://www.facebook.com/CYBRToken/ | |
| Telegram | https://t.me/CYBRnetwork |
| youtube | https://www.youtube.com/CYBRToken |
| https://www.reddit.com/user/CYBRToken | |
| Bitcointalk ID | Sidney47 |
| Bitcointalk profile link | https://bitcointalk.org/index.php?action=profile;u=2046268 |
| ETH wallet address | 0x3FB7e71838Ec7A687F5FDC3F7e6019ACB8Edb6B5 |