Speed, Security, Scalability and Sustainability.

In todays blockchain system we can’t find as unique as Temtum, though some blockchain offers a higher node calculation, lighter storage consumption and secure at the same time. All blockchains are secure, it just varies with features they could offer and for the users/miners if they would be able to keep the network secure with it’s current feature. It is who would last in the long run.
Introducing Temtum
Temtum is a new, lightweight, peer-to-peer cryptocurrency where anyone can support the Temporal Blockchain network, creating a new world of financial freedom away from centralized institutions.
The whole thing here called “Temporal Blockchain network” and anyone can participate in the network to support the project regardless of their device. An active internet connection is the only requirement.
Temtum is here for;
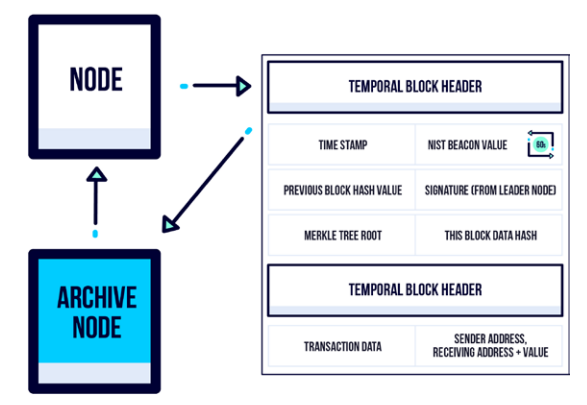
Scalability: The Temporal Blockchain eliminates the need to store the entire chain history on all nodes by locally archiving data, while preventing competition in node selection.
Speed: The speed of the temtum network is limited only by the hardware and bandwidth of network participants.
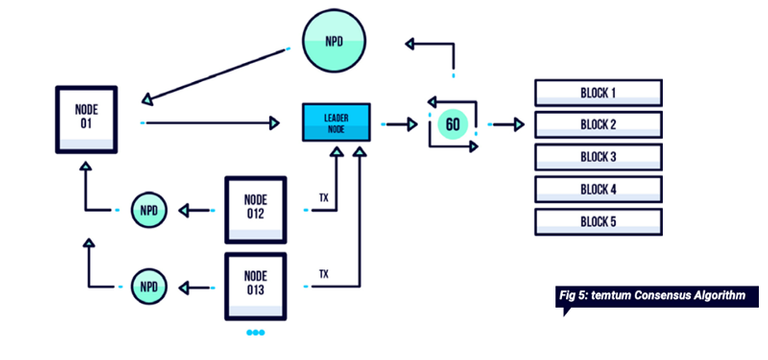
Resources: temtum’s Consensus Algorithm, constructed around leader nodes and our innovative Node Participation Document, removes the need for mining and wasteful, inefficient and restrictive Consensus mechanisms such as proof-of-work.
Security: Temporal is a quantum-secure blockchain network that uses a photon source for genuine random number generation alongside next-generation hashing algorithms.
The speed of the Temporal network is unrivaled by any existing blockchain technology, with 120k TPS achieved in our lab environment and theoretically unlimited, directly influenced by the scale of the network.
Temporal allows for short term data storage on nodes, while keeping the integrity of the blockchain and its full history. With our consensus algorithm, transactions are no longer required to be sent to every node, instead sent directly to the leader node. Therefore, no wasted resources spent in the needless duplication of messages.
This reduction in storage and processing power makes participation in the network from low-resourced devices possible, whilst using less energy than existing blockchain technology.
Their consensus algorithm removes the requirement for mining, eliminating the need for highly wasteful and restrictive consensus mechanisms such as Proof of Work.
Proof of work currently requires trillions upon trillions of pointless energy intensive computational calculations in order to confirm transactions.
With our unique consensus algorithm we reduce this to a single calculation which each node can independently calculate and arrive at the same result.
Real World Applications
The original cryptocurrency, Bitcoin, does have a use case and serves a recognized function as a non-fiat alternative currency that aims to provide an electronic payment system based on cryptographic proof rather than trust, which means that any two parties can transact with one another without needing a trusted third-party. But the flaws inherent in the Bitcoin system mean that it has limited application as a medium of exchange.
We want to allow all users to fully participate in the temtum network regardless of the resources they are able to contribute. The temtum network has been designed from the ground up to run at full capacity on low-powered devices such as smartphones or IoT devices. The only prerequisite to network participation access to an active internet connection or an SMS connection.
Blockchain Research
We’ve spent the past 5 years researching Blockchain and boast the only Blockchain PhD as part of our founding team. This research led to the development of the superior Temporal Blockchain, compared below to what is currently considered the leading technology in the industry.
Technology Roadmap
To demonstrate the technical capabilities of the temtum network — and how few resources a node is required to have in order to participate in the blockchain — we deployed custom code on the head unit (HU) of a BMW i8 as part of a mobility focused project. This allowed the car to function as a fully working node, capable of confirming transactions as the car was driven. The loading of the code into the car did not have any impact on its functionality and was able to run in the background.
Even though the computing power in the i8 is significantly less than traditional computers, it consistently demonstrated the ability to confirm 500 TPS. We believe this is a world-first where a car has been able to act as a full node without the requirement of additional hardware.
Further developments of the mobility project have focused on two main areas:
- The creation of a mesh network using cars as nodes, facilitating node-to-node communication; and
- How this can be integrated into the wider temtum network.
Two test cars, a BMW 220i, and the showcase BMW i8 have been used during testing. As in the previous development cycle, we did not add any additional hardware and only the software on the iDrive systems were modified. We discovered that the BMW 220i, while a significantly less advanced in terms of digital systems than the i8, was still able to fully participate and achieve the same level of performance as a full node (able to store the Temporal Blockchain and confirm transactions when required) as the flagship i8.
After demonstrating that an entry-level BMW is fully capable of participating in the temtum network as a node, we also achieved a mesh network between cars. This allowed the BMW 220i to have its own mobile network connection disabled, leaving it without internet access and instead receive data directly from the i8.
Receiving data from the i8 to the 220i directly, where Temporal and all transactions are also using cryptography, would not present an attack vector. The ability to communicate with vehicles that do not have an active internet connection increases the opportunity for older cars to participate in the network, while removing any mobile data charges and reducing costs for network participation.
Sideloading our application into the existing entertainment system of the older model BMW showed no performance degradation to the driver. Testing is under way to apply this theory to more car brands, including a 2018 Renault Megane, which will allow for direct cross-platform (i.e. from brand A to brand B) communication.
More than half-a-million BMW vehicles were registered in the UK from January 2014 to January 2017, with each vehicle more than capable of participating in and supporting the temtum network. With network scale increasing attack costs, participation via existing mobility infrastructure could ultimately secure temtum beyond levels seen with existing networks, without the need for expensive energy consumption.
Although the environmental impact of fuel-powered vehicles is of some concern, making use of technology that’s already in use and reducing the burden of such networks as Bitcoin on international energy resources is a positive move before more sustainable vehicles begin participating in the temtum network.
The Team
Dr Douglas Meakin — President
Douglas is an experienced technical executive with many years working within engineering, product development, quality systems and processes and operations in leading-edge technology industries. He is a proven business and operations leader and agent of change in a global context, having transitioned large organisations globally whilst managing huge increases in scope, complexity and business volumes. He is committed to effective and motivational leadership of teams and development of human potential. Most recently Douglas was the corporate vice president of global supplier management at Lam Research Corporation, a leading supplier of semiconductor processing equipment, based in Silicon Valley, California. Doug is CEO of temtum and sits on the board of directors.
Richard Dennis — Chief Development Officer
Richard is the founder of Dragon, and a globally acknowledged, prolific and prodigious cybersecurity and cryptography expert. He is also internationally recognised as one of the world’s leading cybersecurity lecturers with a specialism in secure networks, blockchain and encryption. He has a significant body of published research, cited 100’s of times within Blockchain, and presentations on next-generation solutions across a wide range of subjects, including Bitcoin wallet vulnerability, an analysis into the scalability of Bitcoin and Ethereum, and a formal analysis of the Temporal block.
Ginger Saltos — Chief Technology Officer
Ginger has an MSc in Security IT, MSc in Forensics IT and has worked extensively as a telematics engineer. She has five years of experience across public and private companies in security auditing in Ecuador and she has advised the Ecuadorian government about security on systems, policy and procedures. She is currently a professor at ESPOL, teaching programming, databases, security IT and Forensics IT. Open-Sec Ethical Hacker Certificate OP3N-53C 37H1C4L H4CK3R (OSEH). She is also a PhD candidate on the topic of ‘Analysing Malware using Phylogenetics.’ Her key specialisms are artificial intelligence and internet security.
Dr Gareth Owenson — Chief Information Security Officer
Gareth holds a PhD in Computer Science and a BSc in Internet Technology and is a specialist in internet security, cryptography and distributed systems. He has conducted research in large distributed systems with a particular interest in cryptographic applications such as darknets and digital forensics, including developing automated analysis techniques to rapidly reverse engineer advanced malware to determine its functionality and develop countermeasures. He has authored many publications in journals and conferences and regularly serves as a referee for Elsevier, IEEE and CHINACOM. He has conducted a large study into the use of darknets; he is widely recognised as an expert in this field and frequently speaks on this topic. He has also advised the UK and US governments on darknets and internet filtering policy.
David Hodkinson — Chief Financial Officer
David is the co-founder and CEO of Harvex, a specialist firm working with clients in the cryptocurrency, blockchain and online gaming sector. He has worked with multiple high-value ICO’s, advising on international structuring, banking and tax. As a qualified accountant, he has overseen the financial affairs of a wide range of cryptocurrency companies. Alongside this, he has been involved in the strategic launch of multiple online gaming companies and the integration of cryptocurrency with these platforms.
Cyntia Aguirre — Chief Software Architect
Cyntia is a Master of Science in Software Engineering with a strong background in software development and IT architecture. She has four years’ experience both developing as a full stack developer and designing and implementing software as an IT architect for the financial industry (Banco del Austro S.A.). She also holds a PMP accreditation (Project Manager Professional) certified by the Project Management Institute USA.
CONCLUSION
I could see this project shows a lot of potential in terms of long term growth in terms of it’s technological features which allows a new blockchain to scale for future benefits. More and more people are adapting the use of blockchain and cryptocurrencies, as time goes, the security and instantaneous transactions is a priority, so does Temtum.
To know more of Temtum kindly visit these links below :
Website : https://temtum.com/
Whitepaper : https://temtum.com/downloads/temtum-whitepaper.pdf
Telegram : https://t.me/temtumcommunity
Twitter : https://twitter.com/wearetemtum
Facebook : https://www.facebook.com/wearetemtum
Discord : https://discord.gg/hs3v4g4
Reddit : https://www.reddit.com/r/temtum
Medium : https://medium.com/temtum
Linkedin : https://www.linkedin.com/company/temtum/
Youtube : https://www.youtube.com/channel/UCxEJq-piVp83Cm3yAOtQgkg
Github : https://github.com/temtum
Source
Plagiarism is the copying & pasting of others work without giving credit to the original author or artist. Plagiarized posts are considered spam.
Spam is discouraged by the community, and may result in action from the cheetah bot.
More information and tips on sharing content.
If you believe this comment is in error, please contact us in #disputes on Discord
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://temtum.com/