
Knowledge is power and throughout history knowledge has been acquired, transferred, protected, destroyed, misunderstood, but most importantly, used by every human and civilization in this planet. Discovering knowledge is innovative and a synonymous of economic growth and social development. It requires effort, time and resources to acquire meaningful discoveries thus, is a highly valuable process. It becomes an advantage. This is the main reason why humans try to protect (own) knowledge, information and value. So transferring information securely has always been a priority for various reasons.
Multiple interesting methods have been used to protect valuable information in ancient and medieval times but to have a better understanding of the different cryptographic methods that have been used in the past, we need to have a basic understanding of cryptographic concepts.
Basic Concepts
Plain Text
The plain text is simply the readable text of a message. This text is then encrypted into a cipher text to protect it and ensure its integrity so no one alters, misuse, tampers or intercepts the original message.
Cipher Text
The cipher text is the substitution of a plain text. Is basically the unreadable encrypted text. You need to decrypt the text to reveal the actual information being sent.
Cipher
A process to mathematically or mechanically substitute and obfuscate plain text with a cipher text. One just needs to know the algorithm, which is basically the sequence of steps or instructions to follow to encrypt and decrypt a message.
Mono-Alphabetic Ciphers
This type of cipher is the most basic of them all. It uses a single alphabet and transposes its letters to a fixed or arbitrary shift. These days they really don't represent a challenge to decrypt so they are even decrypted nowadays as a pastime in cryptograms.
Poly-Alphabetic Ciphers
Similar to the Mono-Alphabetic cipher with the addition of using more than one alphabet in the encryption process. There's also keywords used to signal where the alphabet is changed.
Code
A code is a little bit more complex than a cipher. A cipher is a straight substitution of letters, but a code is a substitution of meaning. Words are still the same words but context is what actually changes what they mean. This requires a code book sorting out the different meaning phrases or words can have. Because of how tedious and impractical it is to transport and maintain code books, this method of cryptography has been discarded nowadays.
Cryptanalysis
Is the art and science of discovering and decrypting plain text without possessing the encryption key or cipher algorithm. The most frequently used cryptanalysis method is the frequency analysis.
Next, we'll review the most influential analog ciphers used throughout history.
Assyrian Intaglio – 1500 BC

Engraved stones have been used as jewelry for quite some time. This technique is an ancient tradition that goes back to early asian empires like the Assyrian. Engraving means “carving in intaglio” which is when the design is cut into the flat background of a stone. In this example, the main purpose wasn't really to hide any information but to prove ownership of the gem. This design or intaglio was the proof of the authenticity of the art. This could be compared to today's digital signatures.
Atbash – 500 BC
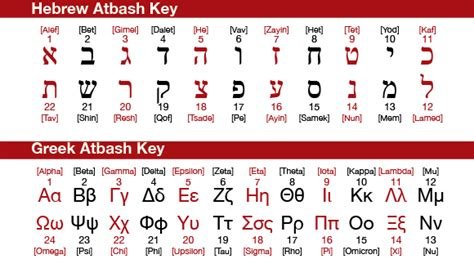
A mono-alphabetic cipher that was used to encrypt the Hebrew alphabet. It can also be modified to be used with any other writing system. It basically consists in taking the letters of the alphabet and mapping it inversely. This means the first letter would become the last letter, the second letter, the second to last and so on.
Scytale - 487 BC

A scytale is a mono-alphabetic symmetrical cipher. The sender uses a cylinder with a strip of leather wrapped around it where you could write messages in a left to right fashion. The receiver needs to use a cylinder of the same diameter to wrap the leather and then be able to read (decrypt) the message. This was convenient because the leather strip could be transported and hidden easily. Greeks are known to used this device specially in military campaigns to communicate. More than hiding the message, the hypothesis is that the scytale was used for authenticating messages.
Steganography – 440 BC
Whereas cryptography is the practice of protecting the contents of a message, steganography is focused in completely hiding that there is a message being sent to begin with. Ancient stenography camouflaged the message in a very creative way. Greeks, for example, shaved the head of their servants, marked or tattooed the message on their heads, then let the hair grow back before sending them to deliver the message. This also authenticated the message by proving that it wasn't altered in any way.
Modern steganography is able to hide files, images, videos or messages by altering the media in a digitally way. Digital steganography is a a highly complex process. Thanks to technology there's countless ways to hide information within information.
Julius Caesar's shift cipher – 44 BC
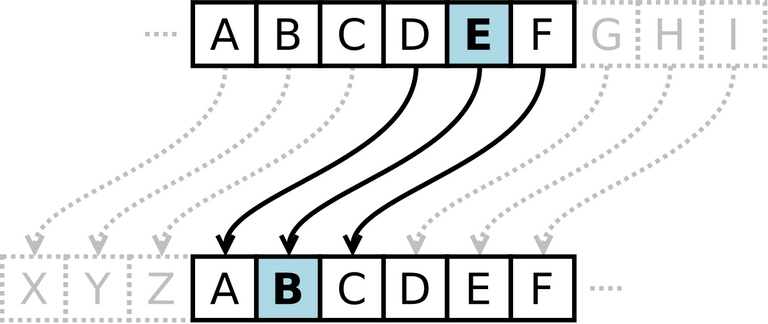
This cipher consisted in shifting the letters of the alphabet to a fixed amount. (for example, the 4th letter becomes the 1st, the 5th the 2nd and so on). This cipher is similar to the Atbash even though to a certain extent, less strong. This wasn't really a problem considering that at the time, few people were able to read so this was a good enough method to communicate official statements in government and military communications. Later on, this cipher was easily cracked using frequency analysis.
The Alberti Cipher Disk - 1466

This cipher disk is the first example of a poly-alphabetic cipher, that mixed alphabets. It consists in two disks a fixed (Stabilis) and movable (Mobilis) disk. The circumference of each is divided in 24 equal cells. The fixed disk has an uppercase alphabet meant for plaintext and the movable disk has a lowercase mixed alphabet for the ciphertext with the lowercase ciphered g matching the uppercase plaintext A. The fixed disk also had 4 numbers that were part of a codebook that contained 336 phrases with assigned numerical values.
So if an uppercase A was inserted in the ciphertext then the ciphertext g would match the plaintext A.
If an uppercase T was insterted in the ciphertext, then the ciphertext g would match the plaintext T.
This type of cipher wasn't cracked until the 1800's.
Vigenère Cipher - 1553

Another poly-alphabetic cipher that allowed the use of many alphabets. This cipher takes multiple Caesar's ciphers in different sequences. The tabula recta is the square table containing the alphabet written out 26 times in different rows, each one shifted cyclically to the left. At different points, the cipher uses different alphabets of one of the rows. The use of different rows depends on a keyword.
Lets visualize an example.
Plaintext: UPVOTETHISPOST
keyword: JUNGLEJUNGLEJU
Ciphertext: DJIUEACBVYASBN
Because JUNGLE is the keyword we know we'll use 6 rows from the table. Our plaintext letter is the column header so all we would need to do is find the matching letter in the grid based on the J alphabet for the letter U, in this case D.
Pigpen Cipher – 1700's
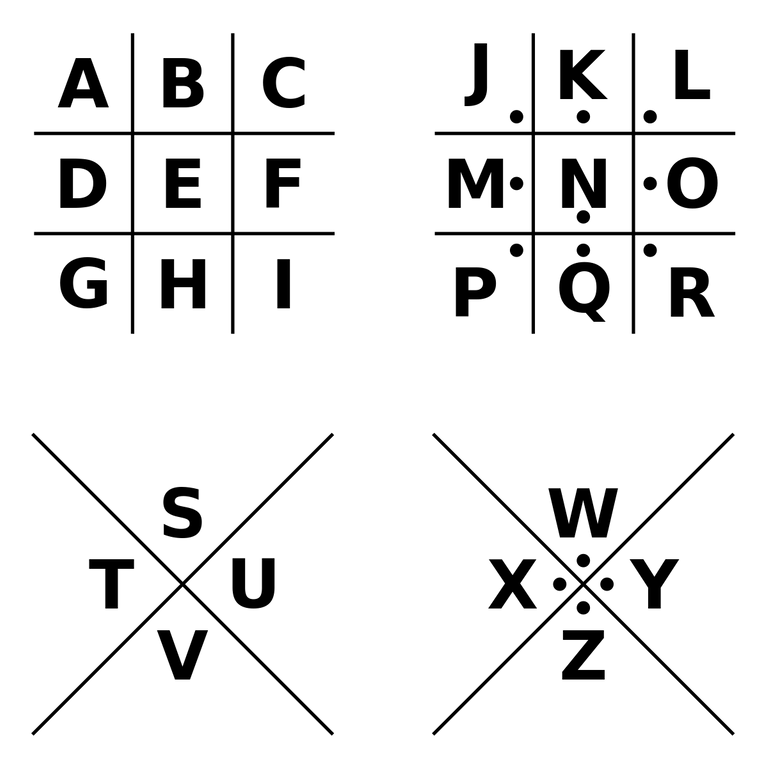
This is a symmetrical mono-alphabetic substitution cipher. Here, we substitute letters with symbols. Due to the simplicity of the system, many variants were used to make it seem more complex but it always followed a similar structure. It is said that this cipher is of ancient origins dating back to Hebrew rabbis but the most famous usage comes from the Freemasons as well as the Rosicrucians.
Playfair Cipher – 1854
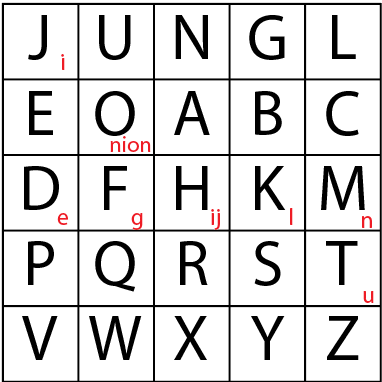
A symmetrical substitution cipher that combines 26 bi-grams (2 letters) instead of 26 letters (monograms). This method is created by constructing a 5x5 grid of letters. Then you need to create a short phrase to begin the grid and fill the rest of the grid with the missing letters of the alphabet. To accommodate a 5x5 grid (25 letters), the letters I and J are used interchangeably. Then you “simply” follow 4 rules to encrypt a message.
if both letters are the same, use an X after the first letter.
if the letters appear on the same row of your table, replace them with the letters to their immediate right respectively.
If the letter appear on the same column of your table, replace them with the letters immediately below respectively.
If the letters are not on the same row or column, replace them with the letters on the same row respectively but at the other pair of corners of the rectangle defined by the original pair.
As you can see in the previous image, I used the words JUNGLE ONION as my phrase. Then I filled the rest of the letters of the alphabet. So here's an example.
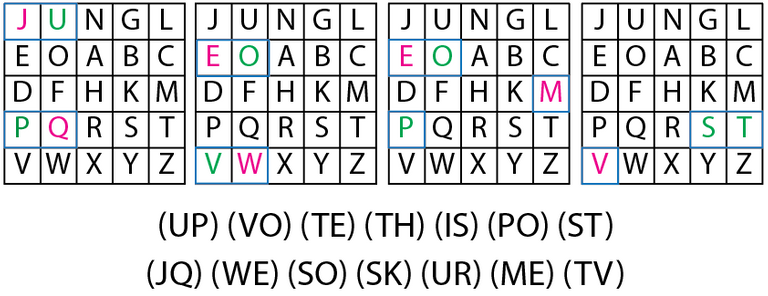
You can see that by following the 4 rules you can easily encrypt whatever you want and easily decrypt it as well. I didn't do all the pairs but I hope you get the idea.
One Time Pad – 1882
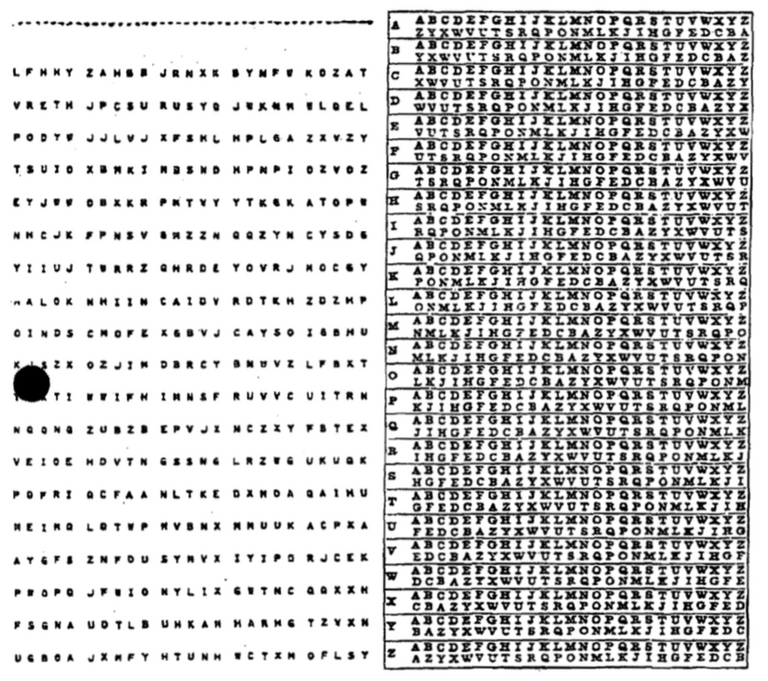
The one time pad technique is pretty much uncrackable, as it requires the use of a one-time pre-shared secret key the same size or longer than the message being sent. This secret key is what is called the one time pad. Each character or letter of the plaintext is encrypted by combining it with the corresponding character or letter from the pad. As long as the secret key is kept completely secret then there's no way this cipher can be cracked. Nations have used this type of cipher in critical diplomatic and military communications. However, the problem of storing and distributing the key or pad is impractical.
The enigma machine – 1914

A german poly-alphabetic stream cipher machine that consisted of a keyboard, a light panel and adjustable rotors. To use it, senders would have to move the rotors in a certain position, then type a message on the keyboard (the plaintext). A corresponding letter would illuminate on the light pad for every typed letter (the cipher). The receiver would need to know the exact position of the rotors to decipher the message. In this step, the typed letters would be the cipher and the illuminated letters the plaintext.
The germans then enhanced the machine by adding a plugboard that would make the machine uncrackable. Through various efforts from different parties, the enigma machine was then able to be cracked, and it is generally accepted that the cracking Enigma shortened the outcome of World War II significantly.
As a parenthesis before moving on to the next section, I would like to at least mention something I find interesting. In my opinion, language itself is a type of symmetrical cypher already. But the most intriguing cypher is perhaps religious symbols. They are not as objective as numbers or steps of a mathematically based cipher. They are not a code because we could simply have a code book to decipher the meaning of symbols or representations in paintings and scriptures. The purpose of religious symbols is to portray a divine truth that goes beyond the ability to express it with language. I think that decrypting that information which is conveyed in religious symbols is the most challenging cryptanalysis that can be done.
Modern Cryptography
With the advent of computer technology, modern cryptography has evolved significantly from methods previously described. We live in an information age, everything is data that can be packed in ones and zeros to transfer. We interact in so many ways that modern life is hyperconnected through emails, videos, messenger apps, social media, blogs, images, e-books, audio files, statistics, behavioral data, personal identifiable information, anonymous data, etc. The amount of knowledge and information has dramatically increased. This couldn't be possible without computers communicating to each other.
A great deal of our daily activities are internet based and thus communicated using computer languages and encrypted using different algorithms. Computers are great at handling encrypted information. Processing power increases exponentially and consistently so new ciphers need to be developed and updated while old ones become obsolete.
For modern cryptography, is good to understand the basics of the following concepts.
Symmetric/Asymmetric Keys
A key, simply put, encrypts and decrypts information. So, symmetric keys are the ones that can be used for both encrypting and decrypting information. Asymmetric keys are used for only one task, either encrypt and decrypt such as in the case of public key cryptography.
Public key cryptography
Public key cryptography is the core functionality of most blockchains and cryptocurrencies. Wallets rely on a public key and a private key (asymmetric keys). Anyone can encrypt a message using the receiver's public key, as in the case of a cryptocurrency transaction. But only the receiver's private key can be used to decrypt information, such as in the case of a withdrawal request.
The RSA and the AES are two algorithms that are still considered safe to this day.
Hash
A hash is an algorithm that maps data of any size and compresses it to a bit string of a fixed size. It takes the data as input and outputs a fingerprint of that message. Once that data is fingerprinted, that hash serves as a validation and authentication mechanism without needing to read the original data.
Properties of a hash
- Deterministic - the same message will always produce the same hash.
- Quick to compute.
- It isn't possible to reverse it. (To find a message with its hash)
- It isn't possible to produce the same hash for two different messages.
- A small change in the message should significantly change the hash.
Hashes are the core of modern cryptography, used to store passwords, render computer graphics, validate SSL certificates and validate transactions in a blockchain.
Secure Hash Algorithm (SHA) Family Hash Ciphers – 1993
SHA is a family of cryptographic hash algorithms. It is a mathematical algorithms that maps data (plaintext) of arbitrary size to a bit string of a fixed size (the hash).
The original SHA cipher is now designated as the SHA-0 and obsolete by current cryptographic standards. SHA-1 is also currently obsolete. The SHA-2 and SHA-3 are the only ones still in use today. The SHA-2 comes in two flavors. SHA-256 for 32-byte words and SHA-512 that uses 64-byte words thus producing 526 and 512 bit hash values respectively.
Bitcoin relies on the SHA-256 hashing algorithm for the validation of transactions within each produced block in its blockchain. Certain blockchains have also decided to validate their transactions using the SHA-3 algorithm also know as Keccak by coins like SmartCash for example.
Mining algorithms
We can also include other hashing algorithms like the SHA but that are used exclusively for mining cryptocurrencies. Most cryptocurrency algorithms intend to be more distributed and decentralized so everyone can join the network and start mining. However, overtime, Application-Specific Integrated Circuit (ASIC) equipment has been developed to solve different algorithms more efficiently and so inevitable making the whole mining process more centralized.
Dagger Hashimoto
Ethereum and any Ethereum based coin (Ethereum Classic, Ubiq, Callisto)
Elliptic Curve Digital Signature Algorithm (ECDSA)
Used by Bitcoin and other cryptocurrencies like Ripple. It's an algorithm that ensures that funds are only spent by the rightful owners. It also adds an extra layer of protection as it requires a signature besides a private and public key. The signature is then used to verify the hash from the public key matches the private key, without needing to know the private key itself.
CryptoNight
Design specifically to anonymize monetary transactions on privacy focused blockchains like Bytecoin and Monero. The CryptoNote is a protocol is used as a layer for CryptoNight coins to maximize the level of anonymity. Here the protocol implements ring signatures which allows you to sign transactions as a group not an individual. The signature indicates a transaction was signed by a group member, but each group member is indistinguishable from each other.
Blake2b
This is an algorithm used for data storage preservation systems like Siacoin.
Scrypt
Initially designed to protect UNIX-like OS backups, this algorithm is widely use by certain cryptocurrencies like Litecoin. Is a peculiar algorithm because it artificially complicates the options the computer have to solve a hash by introducing noise through time.
X11
Another cryptographic algorithm introduced by the main developer of Dash in 2014, back then known as Darkcoin. It initially meant to make ASIC mining more complicated but overtime, ASICs were developed for this algorithm.
Equihash
A hashing algorithm mainly used by Zcash and other Equihash based coins.
Conclusion
Technological advancements have come a long way in many directions of study and is not a different case in computer technology. Computational power increases every time and thus the need for stronger encryption and hashing techniques arises. The next big challenge for cryptography are quantum computers.
As of now, computers work in a linear fashion. Information is reproduced in bits that can be 1's and 0's. But in quantum computers, because of the concept of superposition, bits can exists both as 1's and 0's at the same time meaning uncharted territories for current mathematical equations and algorithms. Quantum computers will not only change computer technology but life as a whole once they reach a point of mass usage. The question is, how much does cryptography needs to advance to remain quantum resistant?
Congratulations @jungleonion! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
You can view your badges on your board and compare to others on the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @hivebuzz:
Vote for us as a witness to get one more badge and upvotes from us with more power!