With the increasing use of the Internet in all walks of life, this use remains a valuable opportunity for anyone who wants to access personal data and information and threaten our safety on the Internet. Piracy Despite the great efforts of security companies and institutions to fight it, it remains and will remain the biggest concern for all in the world of Internet .

We find that hackers have many tactics and methods to obtain data and information, so we have to know some piracy techniques that are commonly used to get your personal information in an unauthorized way, and this is what we will read in the following lines
# Denial of service attacks DoS\DDoS

One of the most common tactics used by hackers to hijack information and data is usually directed to specific sites or multiple sites for the purpose of blocking the service and making them unavailable to the visiting user. This means that when a "DoS attack" is received, traffic is consumed. Site interruption from work and appearance for ordinary visitors.
Such attacks and tactics are a global language for a number of hackers directing their efforts by using a huge number of hacked computers around the world to one goal. The most common attacks of this kind were the same as the previous year for Dyn DNS, resulting in half of the Internet crippled, The attacks were adopted by a group called New World Hackers. The same group was the one who attacked the BBC News site and briefly stopped the site.
Keylogger method

A common tactic and tactic for hackers is to know what you are pressing on your keyboard, whether your PC or laptop, or even your mobile smartphone. In fact, it is an extension of your online behavior. The hacker relies primarily on planting this program or virus on user behavior by installing Anonymous programs, or using known transport modes without scanning them in a control program, or clicking links without verifying their real address.
Once in the victim's machine, you record all our finger strokes on the keyboard, allowing hackers to know all your passwords for different accounts and email. The risk in this tactic is that it does not destroy the hardware or destroy the files, or anything that will catch your attention. On the contrary, it works in silence and quiet so that the victim does not feel anything abnormal or familiar.
It also highlights the mode of placing a tool in the input devices such as: The keyboard is between the computer interface and the CPU, which enables the recording of characters that are pressed on the keyboard, and this method is always found in public Internet cafes.
Waterhole method
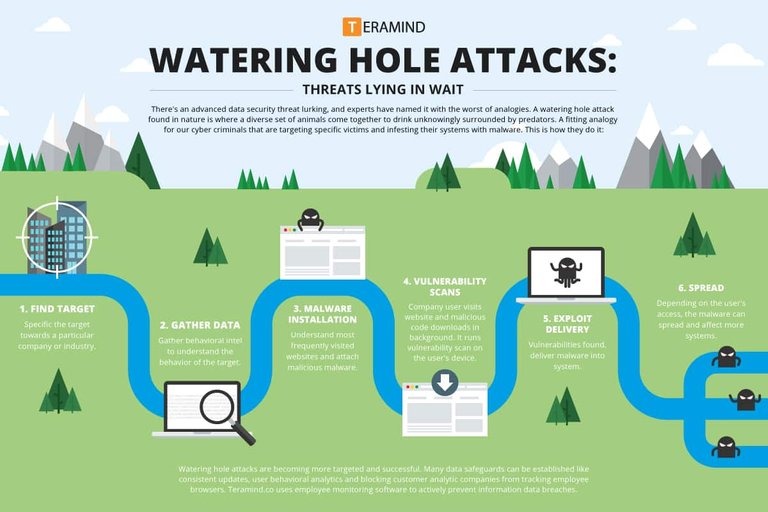
It is a fairly complex and new technique, but if successful, it can cause severe damage that can not be quickly recovered. It is a common attack on computers by gathering information about the victim, whether it is a site, individual, organization, or government agency. , And then encapsulate the most visited sites by injecting the site with a JavaScript or HTML program, which converts the visitor to a malicious site that was previously set up, after which the attacker installs the malicious software on the victim's device (Trojans, Turgens, etc.) During which the attacker can control and control the system fully, usually Discovering this type of method is very difficult and comes in late stages.
Tactic Tapping or Passive Attacks
Unlike other attacks that are active in nature, using an attack that would affect the user and steal his data, the hacker monitors in this method computer systems and networks to obtain confidential information.
The motive behind eavesdropping is not to harm the system or the site, but to get some sensitive information or knowledge of certain information, these types of intrusions can target e-mail, instant messaging services, phone calls, Internet browsing, and other communication methods Tactics are often government agencies that listen to their opponents, or hackers driven by a certain political, economic or moral trend to achieve a goal.
Virus tactics, trojans, worms ... etc

Viruses, Trojans, Worms, etc. are popular methods for hackers and hackers to get information, which is malicious software installed on the victim's device in one of the common ways through which data and information are sent from the victim's device to the hacker.
These methods can also encrypt your files, display fraudulent ads, or transfer or publish traffic from your site on all computers connected to your network.
"stealing cookies" method
Your browser's cookies keep our personal data such as: your browsing history, user name, and passwords for different sites we visit regularly. Hackers can access, control, and change the values in your browsing history to serve a specific purpose.
Another method followed by hackers with cookies, known as the SideJacking hacking session, is where the victim is in line with the attacker on the same site. The victim's connection to the site is not severed, and after the user logs in, both the attacker and the user share access to Site Without knowing that someone else is on the same account, once the user session is done, the attacker can access the site using the victim's session, and do what he wants without having to have a password or username.
"Bait and switch" method
This tactic can be seen as a form of commercial fraud, but the hackers took it as a way to steal data. The hacker buys ad space on multiple sites or sites, and later, when the user clicks on the ad, he is directed to a malicious page.
In this way, the hacker has a valuable opportunity to install malicious software in the victim's devices. The danger is that the ads and download links displayed are always attractive and eye-catching, so the number who click on this ad will be significant over time Or delete it after the end of its purpose.
Phishing method

Of the oldest tactics and methods that hackers and hackers still resort to, despite the articles, studies and books that talk about this technology, but it is still steadfast and continuous in being one of the most successful methods, and the most efficient in the theft of data and information.
The solution is always not to click on random links in social networking sites or applications, or emails, update antivirus and operating systems periodically and regularly, and install security plugins in different browsers to prevent disaster before it occurs.
The tactic of creating a fake contact point
From the easiest methods and tactics, hackers can use the software and applications deployed to create a fake wireless access point, once you get a virtual network connection, hackers can access your data.
It's one of the easiest methods, you can create a fake network and call it an attractive name such as: "Free Wifi", and waiting impatiently to enter it, and begins to steal your data and information easily. The best solution is to encrypt connections using trusted VPN programs ...
------------ ----------- ------------ ------------ ------------ ------------
I spent a fow hours writing in this, I hope that this post you like it, I'm sorry about the grammatical errors

Thanks for the update, I have leant from you, but can their be a way to stop these hackers