After getting some sleep and thinking on the issue a bit more, it's pretty easy to see what happened here. There was no hack.
Here's what happened:
The Koreans used @anonsteem to create an account.
Why they would do this is anyone's guess.
Perhaps they need to brush up on their English.
@anonsteem is run by @someguy123
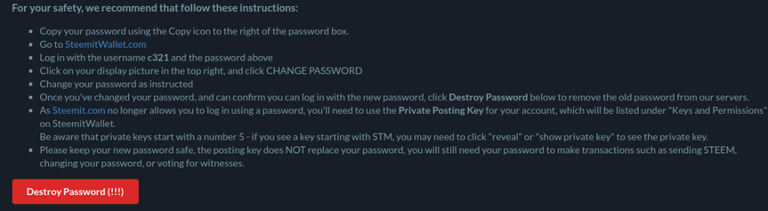
I got into multiple arguments yesterday as to why @someguy123 would never store private keys of the accounts he creates on his node, yet his own service admits transparently that this is exactly what he does.
click Destroy Password below to remove the old password from our servers.
It is truly more fascinating to me that people here at Hive would be so blind to the obvious fact that a website used to create a Graphene account can store that account's password on their servers. This is why everyone should be worried that Steemit Inc themselves was doing the same thing secretly. It might not even be known to Justin Sun or even Ned.
The only way to keep your account 100% secure is to generate the public/private key pairs for your account on an offline device that never has access to the Internet ever again. This is exactly why I am trying to do this with my Raspberry Pi Zero.
https://peakd.com/hextech/@edicted/the-day-of-milestones
Now a lot of people are telling me to keep my mouth shut and to stop blowing up @someguy123's spot. They also make the claim that the Koreans were very flagrant with the private keys for account @community321 and it was probably an inside job betrayer.
No.
Steem witnesses literally tried to steal from Hive witnesses and they gave a Hive witness the private keys. It's not hard to do the math here. The password to @community321's account was changed 10 minutes before the hardfork. That's quite a gambit for an inside job. You know who it wouldn't be risky for? An outside "Robbin Hood" "attacker" that no one was expecting in the first place; Someone who actually knows how hard forks work and was paying attention quite carefully.
@anonsteem and @someguy123 have said nothing in response to this going down, despite receiving multiple threats and accusations.
Why is he saying nothing?
Well, like I said, people are refusing to believe that it even went down this way. It doesn't look good for a witness when they admit, "Oh yeah, @anonsteem, I can pretty much steal or recover anyone's account for at least the first month." That is exactly what is happening. It details it directly on his own web page, but somehow no one believes it.
In fact, a few people have said to me this can't be the case because they contacted @someguy123 and tried to recover their old account, but they were told the only way to do it was by having an old master key no older than 30 days (traditional recovery). If what I'm saying is true then @someguy123 actually does have the power to recover or access those accounts, he simply chooses not too because it is too much work (and liability) and @anonsteem isn't exactly a very profitable venture. That's certainly what I would do I'm sure.
Why would you say anything?
You wouldn't. Whatever you say can and will be used against you in the court of law. It would be fucking stupid to say anything. No one can prove shit. Admitting to a potential crime that undermines your own service is a foolhardy endeavor indeed.
Nothing illegal even happened!
Hey, I'm on @someguy123's side, and I think I'll vote him for witness now just as a symbol of my support (only voting 4 witnesses right now due to vote centralization). What he did was the opposite of an illegal act, but you never know what the bullshit courts of America are going to decide. Also, lawyers are expensive; #fuckthatnoise.
If you tell a cop that you don't like icecream, they are going to find evidence that you do like icecream and now they've established you're a liar so therefore you also did this other illegal act.
NEVER SAY ANYTHING!!!! EVER!!!!1111
You aren't going to trick a professional expert of someone whose job it is to get you in trouble. Don't be an idiot. A stalemate is the smartest play when it comes to interrogation; never go for the win. Tie goes to the defendant. Innocent until proven guilty. Any half-competent lawyer will tell you the same.
Personally, if I was being interrogated by police, I'd go on some long diatribe about why cops are the bad guys and how the prison industrial complex is a completely broken system with shit recidivism rates in a for-profit industry that makes the world a worse place; not a better one. Would this be the smartest move? Probably not; the smartest move is to STFU. However, it would better establish my motive for not giving police any useful information of any kind no matter what the topic was.
Circumstantial "evidence"
It is also very clear to me from yesterday that @r0nd0n taking credit for the act was a fun little deflection. The way he spoke and the fact that account @community321 referenced him in real time signals to me that there is a secret Discord of people who are chuckling about all this, and @r0nd0n is in that Discord. He didn't do it, but he 100% knows who did. Even his own language is like "all will be revealed soon!" "Time will tell!" No need for that...
It's very obvious what happened here.
The most obvious answer is the answer. I called it the second I read it in @communitiy321's transaction log that the account was created using @anonsteem.
No such statement has been made; probably for the best.
Conclusion
We should all work to protect @someguy123 from any potential bullshit litigation. Casting reasonable doubt is a great start. Steem witnesses had no idea what they were doing and the account was compromised from multiple angles. No one can prove anything. Let's just leave it where it lies.
However, on that note, when @bittrex inevitably sends back the money to @community123 what we do from there is another matter entirely. Luckily I'm not involved in any of that decision making, and I don't envy the entities that are.
P. S.
@someguy123, what's the status on the Steem witnesses being able to recover account @community321? You are the recovery account... surely you are diligently identifying the rightful owners and helping them... LOL.
Babytown Frolics.
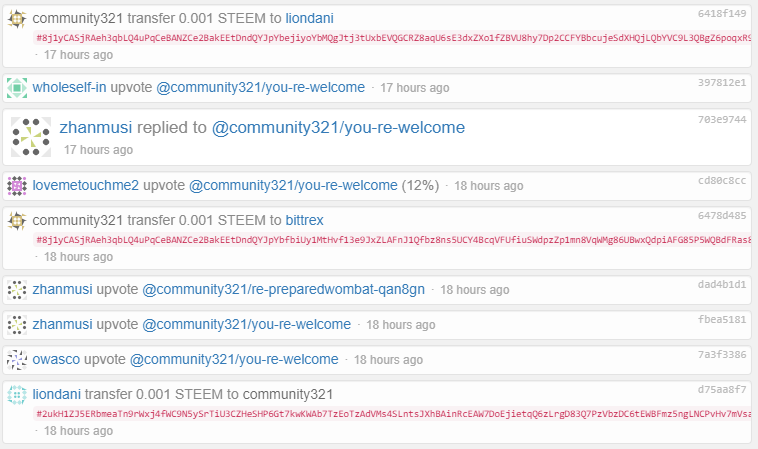
Wow look at that encrypted messages are being sent to the exchanges.
Let's keep playing this dangerous game. #exciting
I've documented the account recovery procedure - @anonsteem / @beeanon really can't recover an account once the keys are deleted. We don't have database backups, and "Destroy Password" irreversibly deletes the password from the database.
https://peakd.com/steem/@someguy123/how-the-steem-account-recovery-works-and-why-your-trustee-can-t-steal-your-account
If someone didn't delete their password from the site, and they were hacked within the first 30 days of getting their account, then their original password (which they didn't delete) could be used for recovery, if they can prove they created the account in some way https://beeanon.com/recovery
After 30 days of changing their password, their original password cannot be used to recover the account - as recovery requires the owner key to be one which was valid within the past 30 days.
Wow I like your style.
Great answer.
Keep up the good work.
So Justin Tron said that he, nor steemit inc worked on the fork.
The people who did work on the fork had to make an account using an anon method.
Steemit didn't do it and HIVE didn't do it, then who wrote teh fork?
A third party.
So, some random guy wrote a fork and then Mr. Tron's servers... errr sock puppets all voted for it. (boy are they trusting) and then the sheep hit the rotating air moving device.
"If you don't own the keys, it isn't yours."
If it does go back to Community321, wouldn't the move be for it to be returned to the rightful owners pre-fork - after they send an encrypted memo with a bittrex account attached?
Pretty sure Bittrex can't keep their money, and @community321 can't keep the money, and it doesn't matter it was stolen by witnesses via a HF as to whose money it actually is.
Reckon the law specifies folks whose rightful property is stolen get it back if it's recovered, which this is. Returning it to the rightful owners is the only lawful move.
Interestingly, if it's returned while the HF that stole it is still in operation, it will get stolen again and sent to @community321 again.
Do you think that would be a separate crime? If @community321 sends it back to the owners quickly and often, the thieves might rack up quite a quantity of charges until they roll back the HF.
LOL
If it goes back there, I would say that it would have to be transferred out to other accounts not HF affected.
:D
It wasn't my keys that got leaked, it was @community321. Totally different beast.
Funny how that typo wasn't pointed out till now.
I'm the only one that notices. I am community123.
"The only way to keep your account 100% secure is to generate the public/private key pairs for your account on an offline device that never has access to the Internet ever again."
That has to change if the general public are ever to get involved. Very very few people have the technical or financial ability to properly secure their funds in that way. My hope is things move toward more people being able to get involved, not less.
Anyway, do you think the hackers still have full control of community321? If so, when the funds are returned by bittrex (which it seems like will be the case), then what? Send them back to bittrex? I mean, if that was the smart move yesterday, maybe it's still the smart move today? Being sarcastic, of course..... IMO it wasn't a smart move to send to bittrex as that has only delayed justice and possibly risked things going wrong.
is not to have one.
That would not completely secure his account. It's more secure, but his airgapped system isn't proof from physical access, and nothing can ever completely eliminate risk.
Okay, but who invited logic into this discussion :P
Heheh, but yeah, technically there's no such thing as completely safe when it comes to crypto (and probably everything else when it gets right down to it).
Nothing, no one, and no place is safe, and that's how to think about them.
The general public doesn't need an unhackable account. The general public lives paycheck to paycheck. They work for the blockchain and the blockchain pays them money, which they liquidate into another account.
Also, this process can be centralized and all these complex systems can be delegated to a node that manages the security for multiple people. Accounts will be as secure as they need to be.
What do you think these are?
Posted Using LeoFinance
Probably messages to the exchanges proving the intention of the user that controls the account.
Pretty cool turnaround and another proof why communities matter because anyone can do a great gesture for the others. And now all those great people have migrated on HIVE to build something wonderful. Keep up the good work!
Ocam's razor, even though the HF was planned in "secret" it was leaked before it was made public = inside job (someone with knowledge made sure that it was no longer a secret). Probaby the same person had access to the keys.
Posted Using LeoFinance
Indeed the code did leak.
There was dissent in the ranks, and they pushed the HF anyway.
That's pretty amazing stuff. You are a clever dude to be able to figure all of that out :)
Hive is being pumped again, and we'll see where the dump puts HIVE. I'm not complaining-- we can all use the extra value.
It's too late for me to upvote this post, so please accept this slice of !PIZZA instead.
Posted Using LeoFinance Beta
PIZZA Holders sent $PIZZA tips in this post's comments:
@magnacarta(6/10) tipped @edicted (x1)
Learn more at https://hive.pizza.