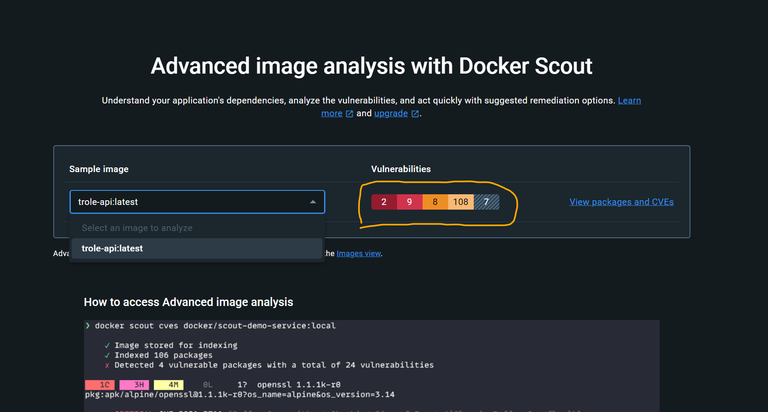
Next week, the SpeakNetwork Community plans to continue testing the local Storage-Node software during our TestNet-Sprint. In preparation for this event, I have conducted a thorough analysis of the Docker container using Docker-Scout, and I am sharing the results in this article. This analysis aims to provide guidance and assistance to the developers, urging them to review the package carefully and address some of the identified security vulnerabilities before we proceed with further testing.
I understand that addressing these issues may require significant effort, but I believe it is essential for ensuring the security and reliability of the software. The SpeakNetwork Community is ready and willing to assist by testing newer packages and providing direct feedback across various systems. Our collective goal is to improve the software's robustness and security, creating a more reliable platform for all users.
This article outlines the vulnerabilities found, categorized by severity, and offers recommendations for updating or changing the base image to mitigate these risks. I encourage the developers to prioritize these security fixes, as it will significantly enhance the testing process and overall software quality. We are committed to supporting the developers in this endeavor, ensuring that our testing environment is as secure and stable as possible.
Docker Container Analysis with Docker-Scout
The following presents the analysis results of a Docker container using Docker-Scout to help the software author address potential vulnerabilities.
Overview
| Analyzed Image | |
|---|---|
| Target | local://trole-api:latest |
| Digest | 17558460b011 |
| Platform | linux/amd64 |
| Vulnerabilities | 2C 9H 8M 108L 7? |
| Size | 530 MB |
| Packages | 1087 |
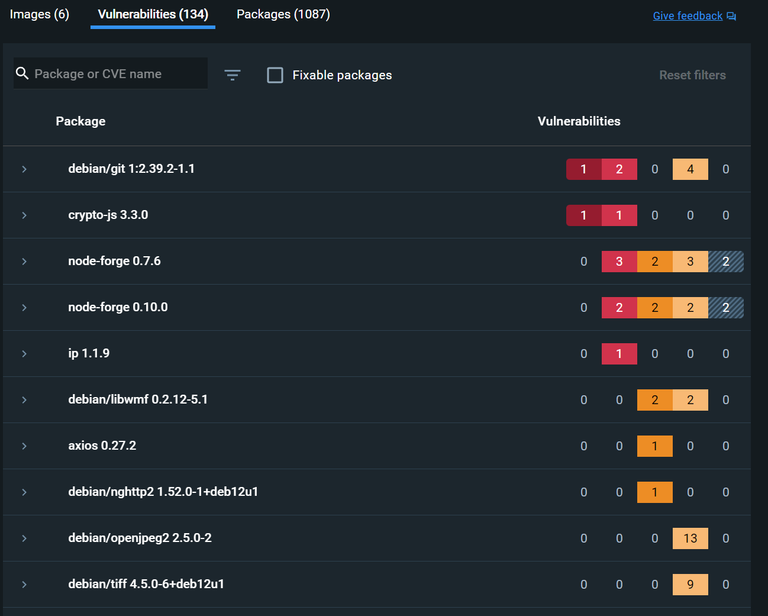
Packages and Vulnerabilities
1. git 1:2.39.2-1.1
- CRITICAL:
- CVE-2024-32002 - Not fixed
- HIGH:
- CVE-2024-32004 - Not fixed
- CVE-2024-32465 - Not fixed
- LOW:
- CVE-2024-32021 - Not fixed
- CVE-2024-32020 - Not fixed
- CVE-2022-24975 - Not fixed
- CVE-2018-1000021 - Not fixed
2. crypto-js 3.3.0
- CRITICAL:
- CVE-2023-46233 - Fixed in 4.2.0
- HIGH:
- GMS-2020-4 - Fixed in 3.2.1, 4.0.0
3. node-forge 0.7.6
- HIGH:
- CVE-2020-7720 - Fixed in 0.10.0
- CVE-2022-24772 - Fixed in 1.3.0
- CVE-2022-24771 - Fixed in 1.3.0
- MEDIUM:
- CVE-2022-0122 - Fixed in 1.0.0
- CVE-2022-24773 - Fixed in 1.3.0
- LOW:
- GHSA-wxgw-qj99-44c2 - Fixed in 0.10.0
- GHSA-gf8q-jrpm-jvxq - Fixed in 1.0.0
- GHSA-5rrq-pxf6-6jx5 - Fixed in 1.0.0
- UNSPECIFIED:
- GMS-2022-67 - Fixed in 1.0.0
- GMS-2022-66 - Fixed in 1.0.0
4. node-forge 0.10.0
- HIGH:
- CVE-2022-24772 - Fixed in 1.3.0
- CVE-2022-24771 - Fixed in 1.3.0
- MEDIUM:
- CVE-2022-0122 - Fixed in 1.0.0
- CVE-2022-24773 - Fixed in 1.3.0
- LOW:
- GHSA-gf8q-jrpm-jvxq - Fixed in 1.0.0
- GHSA-5rrq-pxf6-6jx5 - Fixed in 1.0.0
- UNSPECIFIED:
- GMS-2022-67 - Fixed in 1.0.0
- GMS-2022-66 - Fixed in 1.0.0
5. ip 1.1.9
- HIGH:
- CVE-2024-29415 - Not fixed
6. libwmf 0.2.12-5.1
- MEDIUM:
- CVE-2009-3546 - Not fixed
- CVE-2007-3996 - Not fixed
- LOW:
- CVE-2007-3477 - Not fixed
- CVE-2007-3476 - Not fixed
7. nghttp2 1.52.0-1+deb12u1
- MEDIUM:
- CVE-2024-28182 - Not fixed
8. axios 0.27.2
- MEDIUM:
- CVE-2023-45857 - Fixed in 1.6.0
9. openjpeg2 2.5.0-2
- LOW:
- CVE-2018-20846 - Not fixed
- CVE-2018-16376 - Not fixed
- CVE-2018-16375 - Not fixed
- CVE-2017-17479 - Not fixed
- CVE-2016-9581 - Not fixed
- CVE-2016-9580 - Not fixed
- CVE-2016-9117 - Not fixed
- CVE-2016-9116 - Not fixed
- CVE-2016-9115 - Not fixed
- CVE-2016-9114 - Not fixed
- CVE-2016-9113 - Not fixed
- CVE-2016-10506 - Not fixed
- CVE-2016-10505 - Not fixed
10. tiff 4.5.0-6+deb12u1
- LOW:
- CVE-2023-6228 - Not fixed
- CVE-2023-3164 - Not fixed
- CVE-2023-1916 - Not fixed
- CVE-2022-1210 - Not fixed
- CVE-2018-10126 - Not fixed
- CVE-2017-9117 - Not fixed
- CVE-2017-5563 - Not fixed
- CVE-2017-17973 - Not fixed
- CVE-2017-16232 - Not fixed
11. openssh 1:9.2p1-2+deb12u2
- LOW:
- CVE-2023-51767 - Not fixed
- CVE-2020-15778 - Not fixed
- CVE-2020-14145 - Not fixed
- CVE-2019-6110 - Not fixed
- CVE-2018-15919 - Not fixed
- CVE-2016-20012 - Not fixed
- CVE-2008-3234 - Not fixed
- CVE-2007-2768 - Not fixed
- CVE-2007-2243 - Not fixed
12. imagemagick 8:6.9.11.60+dfsg-1.6+deb12u1
- LOW:
- CVE-2023-34152 - Not fixed
- CVE-2021-20311 - Not fixed
- CVE-2018-15607 - Not fixed
- CVE-2017-7275 - Not fixed
- CVE-2017-11755 - Not fixed
- CVE-2017-11754 - Not fixed
- CVE-2016-8678 - Not fixed
- CVE-2008-3134 - Not fixed
- CVE-2005-0406 - Not fixed
13. glibc 2.36-9+deb12u7
- LOW:
- CVE-2019-9192 - Not fixed
- CVE-2019-1010025 - Not fixed
- CVE-2019-1010024 - Not fixed
- CVE-2019-1010023 - Not fixed
- CVE-2019-1010022 - Not fixed
- CVE-2018-20796 - Not fixed
- CVE-2010-4756 - Not fixed
14. binutils 2.40-2
- LOW:
- CVE-2023-1972 - Not fixed
- CVE-2021-32256 - Not fixed
- CVE-2018-9996 - Not fixed
- CVE-2018-20712 - Not fixed
- CVE-2018-20673 - Not fixed
- CVE-2018-18483 - Not fixed
- CVE-2017-13716 - Not fixed
15. patch 2.7.6-7
- LOW:
- CVE-2021-45261 - Not fixed
- CVE-2018-6952 - Not fixed
- CVE-2018-6951 - Not fixed
- CVE-2010-4651 - Not fixed
16. openldap 2.5.13+dfsg-5
- LOW:
- CVE-2020-15719 - Not fixed
- CVE-2017-17740 - Not fixed
- CVE-2017-14159 - Not fixed
- CVE-2015-3276 - Not fixed
17. systemd 252.22-1~deb12u1
- LOW:
- CVE-2023-31439 - Not fixed
- CVE-2023-31438 - Not fixed
- CVE-2023-31437 - Not fixed
- CVE-2013-4392 - Not fixed
18. m4 1.4.19-3
- LOW:
- CVE-2008-1688 - Not fixed
- CVE-2008-1687 - Not fixed
19. shadow 1:4.13+dfsg1-1
- LOW:
- CVE-2019-19882 - Not fixed
- CVE-2007-5686 - Not fixed
20. perl 5.36.0-7+deb12u1
- LOW:
- CVE-2023-31486 - Not fixed
- CVE-2011-4116 - Not fixed
21. expat 2.5.0-1
- LOW:
- CVE-2024-28757 - Not fixed
- CVE-2023-52426 - Not fixed
22. util-linux 2.38.1-5+deb12u1
- LOW:
- CVE-2022-0563 - Not fixed
23. gnutls28 3.7.9-2+deb12u2
- LOW:
- CVE-2011-3389 - Not fixed
24. gnupg2 2.2.40-1.1
- LOW:
- CVE-2022-3219 - Not fixed
25. libxml2 2.9.14+dfsg-1.3~deb12u1
- LOW:
- CVE-2024-34459 - Not fixed
26. apt 2.6.1
- LOW:
- CVE-2011-3374 - Not fixed
27. libxslt 1.1.35-1
- LOW:
- CVE-2015-9019 - Not fixed
28. libgcrypt20 1.10.1-3
- LOW:
- CVE-2018-6829 - Not fixed
29. sqlite3 3.40.1-2
- LOW:
- CVE-2021-45346 - Not fixed
30. libpng1.6 1.6.39-2
- LOW:
- CVE-2021-4214 - Not fixed
31. curl 7.88.1-10+deb12u5
- LOW:
- CVE-2024-2379 - Not fixed
32. coreutils 9.1-1
- LOW:
- CVE-2017-18018 - Not fixed
33. gcc-12 12.2.0-14
- LOW:
- CVE-2022-27943 - Not fixed
34. libheif 1.15.1-1
- LOW:
- CVE-2024-25269 - Not fixed
35. tar 1.34+dfsg-1.2+deb12u1
- LOW:
- CVE-2005-2541 - Not fixed
36. krb5 1.20.1-2+deb12u1
- LOW:
- CVE-2018-5709 - Not fixed
37. glib2.0 2.74.6-2+deb12u2
- LOW:
- CVE-2012-0039 - Not fixed
38. jbigkit 2.1-6.1
- LOW:
- CVE-2017-9937 - Not fixed
39. unzip 6.0-28
- LOW:
- CVE-2021-4217 - Not fixed
40. openexr 3.1.5-5
- LOW:
- CVE-2017-14988 - Not fixed
41. openssl 3.0.11-1~deb12u2
- LOW:
- CVE-2010-0928 - Not fixed
42. elfutils 0.188-2.1
- LOW:
- CVE-2024-25260 - Not fixed
43. pixman 0.42.2-1
- LOW:
- CVE-2023-37769 - Not fixed
44. jansson 2.14-2
- LOW:
- CVE-2020-36325 - Not fixed
45. libyaml 0.2.5-1
- UNSPECIFIED:
- CVE-2024-35329 - Not fixed
- CVE-2024-3205 - Not fixed
46. aom 3.6.0-1
- UNSPECIFIED:
- CVE-2024-5171 - Not fixed
Summary of Findings
- 134 vulnerabilities found in 46 packages:
- 2 Critical
- 9 High
- 8 Medium
- 108 Low
- 7 Unspecified
Conclusion
The analysis reveals multiple critical and high vulnerabilities in the Docker container. It is recommended to update the affected packages or find alternative solutions to ensure the container's security.
For detailed information, refer to the provided CVE and GMS links.
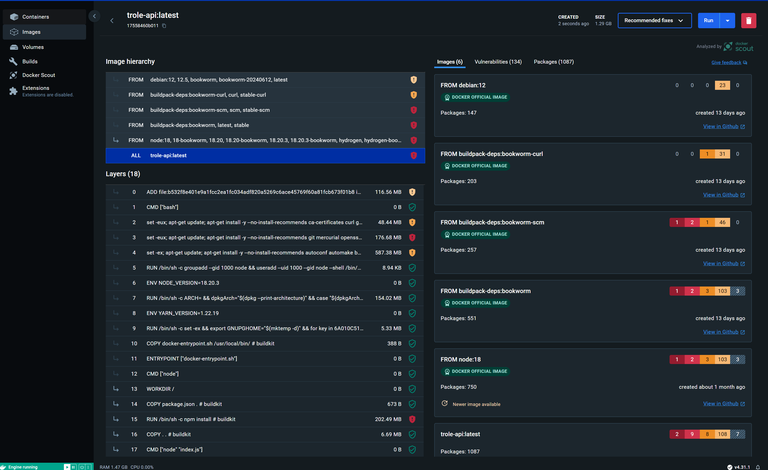
Recommended fixes
Base Image Information
Base image: node:18
| Name | Digest | Vulnerabilities | Pushed | Size | Packages | Runtime |
|---|---|---|---|---|---|---|
| 18 | sha256:7176e37dd29986e14c923bb38f2331f767e167c944915448091039d66dfd1029 | 1C, 2H, 3M, 103L, 3? | 1 month ago | 396 MB | 747 | 18 |
The base image is also available under the supported tag(s): 18-bookworm, 18.20, 18.20-bookworm, 18.20.3, 18.20.3-bookworm, hydrogen, hydrogen-bookworm. To display recommendations for a different tag, re-run the command using the --tag flag.
Refresh Base Image
Rebuild the image using a newer base image version. Updating this may result in breaking changes.
Current Status: This image version is up to date.
Change Base Image
The list displays new recommended tags in descending order, where the top results are rated as most suitable.
| Tag | Benefits | Pushed | Vulnerabilities |
|---|---|---|---|
| 22-slim | - Image is smaller by 305 MB - Image contains 425 fewer packages - Major runtime version update - Tag was pushed more recently - Image introduces no new vulnerability but removes 86 - Tag is using slim variant | 2 weeks ago | 0C, 0H, 0M, 23L |
| 20-slim | - Image is smaller by 309 MB - Image contains 423 fewer packages - Major runtime version update - Tag was pushed more recently - Image introduces no new vulnerability but removes 86 - Tag is using slim variant | 1 day ago | 0C, 0H, 0M, 23L |
| 22 | - Image contains 2 fewer packages - Major runtime version update - Tag was pushed more recently - Image has similar size - Tag is latest - Image has same number of vulnerabilities | 2 weeks ago | 1C, 2H, 3M, 103L, 3? |
| 18-slim | - Image is smaller by 312 MB - Image contains 423 fewer packages - Image introduces no new vulnerability but removes 86 - Tag is using slim variant - 18-slim was pulled 33K times last month | 1 month ago | 0C, 0H, 0M, 23L |
| 20 | - Major runtime version update - Tag was pushed more recently - Image has similar size - Image has same number of vulnerabilities - Image contains equal number of packages | 1 day ago | 1C, 2H, 3M, 103L, 3? |
Image details:
- 22-slim: Size: 76 MB, Runtime: 22
- 20-slim: Size: 71 MB, Runtime: 20.15.0
- 22: Size: 402 MB, Runtime: 22
- 18-slim: Size: 69 MB, Runtime: 18
- 20: Size: 398 MB, Runtime: 20.15.0
I hope this help, if u need further details, hit me up or install docker-desktop with the docker-scout integration to analyse docker-containers.
Thanks and Greetings.
Congratulations @louis88! You have completed the following achievement on the Hive blockchain And have been rewarded with New badge(s)
Your next target is to reach 190000 upvotes.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPCheck out our last posts: