Hi investors,
Today we're exploring the curious case of the 51% attacks on Ethereum Classic and its implications for the security of the Bitcoin network.
Let's dive in!

Ethereum Classic.
The month of August was a rough one for Ethereum Classic (ETC).
The self-styled "immutable" network suffered no less than three 51% attacks between August 1 and August 29.
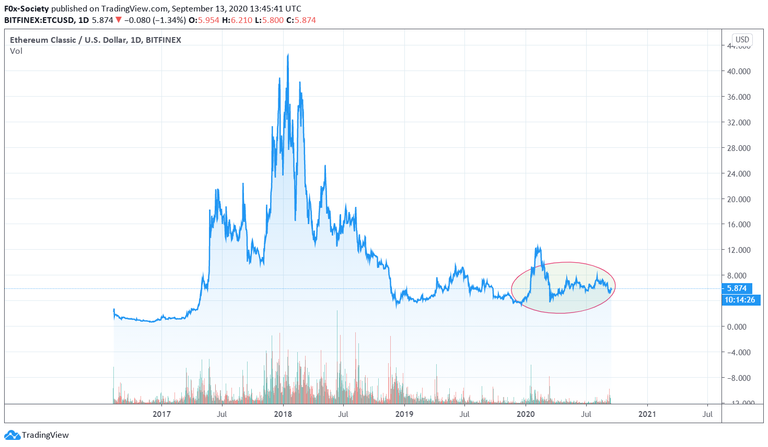
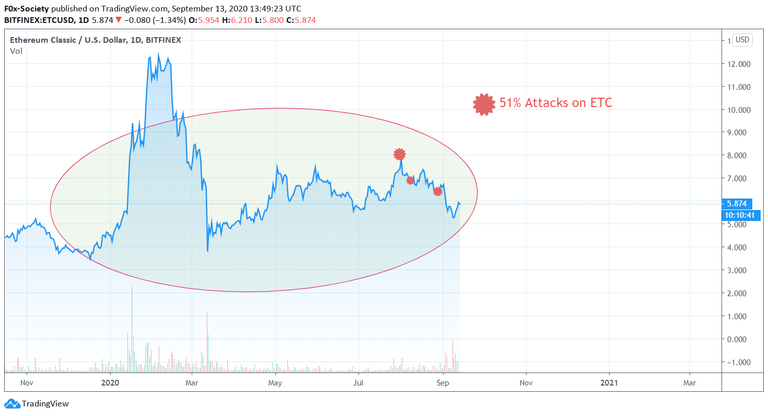
The first attack happened between July 31 and August 1.
According to the website Bitquery.io:
Ethereum Classic experienced a huge ‘51% attack’. One miner generated a series of more than 3500 blocks, as a huge fork from block 10904146 till 10907740. He mined these blocks for many hours and broadcasted them afterward to other miners. As this sequence of the block had more weight than the chain, built by all other miners, they had to accept these blocks, effectively replacing the blockchain history with the attacker’s one.
After successfully re-writing the transaction history of the chain, the attacker proceeded to double spend the coins:
Using a stolen Coinbase account, the attacker [was able to] double-spent 807,260 ETC ($5.6 million) during this attack. The attacker also got 13K ETC as a block mining reward.
This first attack also impacted users of the chain and "honest" miners as none of the transactions nor block mined during the time of the attack was eventually recorded on the "new" chain.
On August 8, the same attacker struck again. This time, using the money from the first attack.
The attacker first tried to double-spend 465,444 ETC (approx $3.3 M). However, they were only able to successfully double-spent 238,306 ETC ($1.68 M) through Bitfinex and another crypto service. In addition, the attacker also got 14.2K ETC as a block reward.
The last and biggest attack happened on August 29. This time no less than 7000 blocks (equivalent to two days of mining and twice the size of the first and second attack) were reorganized.
Since numerous exchanges had taken measures to avoid further attack after the first one (by dramatically raising the number of confirmations required to deposit coins), it's not clear if these coins were successfully double-spent after the chain was reorganized.
How were the attackers able to pull this off?
In POW chains, malicious reorganizations of the history of the blockchain are possible if an actor acquires 51% or more of the hash-power.
In Ethereum Classic, the hash power used to mine ETC can be rented from cloud mining services like NiceHash.
This "liquid" market for hash-power consists of distributed network of privately owned GPU machines optimized to mine the Ethash algorithm which is used on both Ethereum and Ethereum Classic.
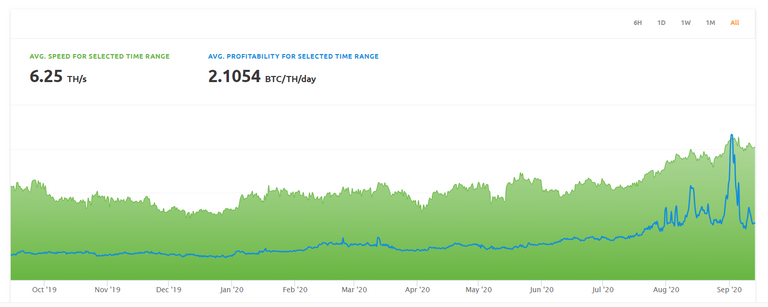
You can clearly see spikes in the price of hashing power as the attacker(s) bid up the market to carry the attacks:
The result of the attack was a slow 28% drop in price from the day of the first attack.
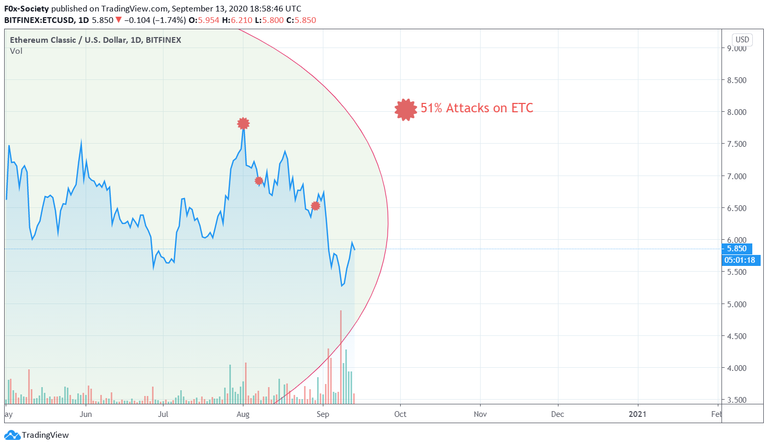
Worse, the health of the network was gravely affected. The transaction count on ETC has more than halved since August 1 and the total hash-power has plummeted to its lowest levels since May 2017.
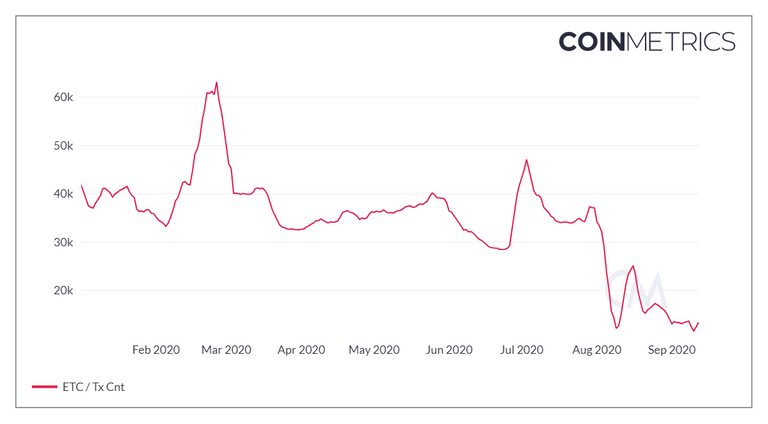
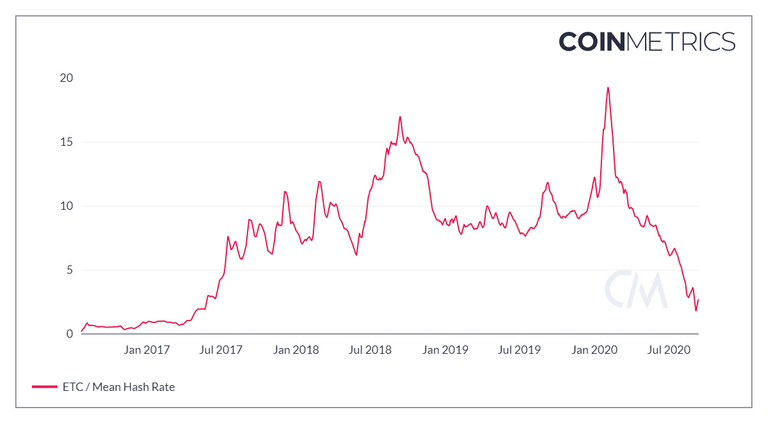
ETC looks like a dying project to me, but one that's inexplicably up almost 15% YtD and still worth over $600 million USD.
How did the chain's security become so weak?
The problem is that ETC shares its hashing algorithm (Ethash) with its much bigger cousin ETH.
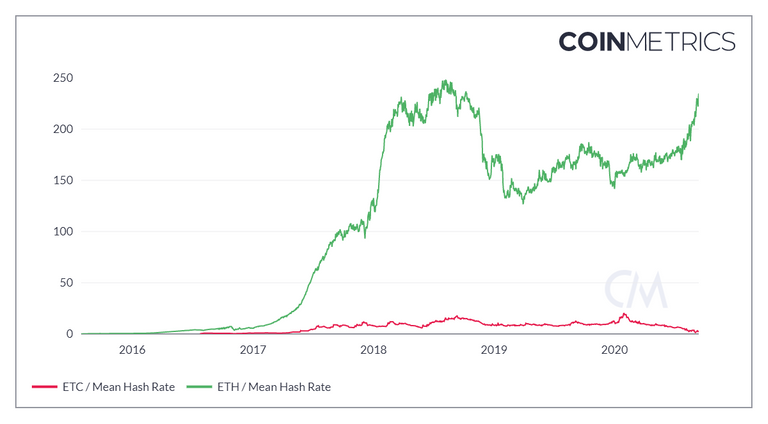
For a POW chain, not being the dominant coin in your hashing "family" is a severe security risk but not an automatic death sentence.
In the Ethash family, miners are GPUs. Due to its lack of specialization, GPU hashing power is highly liquid and can easily be hired on NiceHash to mine or attack Ethash coins.
A rational, non-ideological Ethhash miner would thus only mine on ETC if the ROI of mining ETC is superior to the opportunity cost of not mining ETH.
But what happens when you can make an even bigger margin attacking the ETC network instead?.
According to the website crypto51.app, the current cost of "mining" an attack on ETC is $3,748 USD per hour.

Compare that with the costs of attacking ETH (or even Bitcoin):
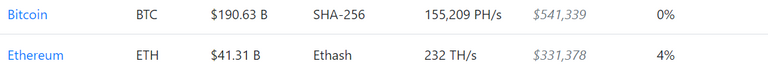
Basically if:
Cost of Attacking the ETC network < Opportunity cost of not mining on ETH
Then:
Ethash miners have an incentive to attack ETC
During the first attack for instance, the attacker was able to double-spent 807,260 ETC ($5.6 million USD) while only spending 17.5 BTC ($192K USD) to acquire the hash power for the attack on Nicehash.
Of course the total cost of attacking the ETC chain is not a sole function of the price of renting the hashing power. An attacker would also need to factor in the cost of the coin's value potentially depreciating after the attack. Furthermore, if the attacker also wanted to double spent on an exchange, the total cost would also include the cost of thwarting KYC safeguards.
Unlike double-spending attacks, simple "reorg" attacks are very difficult to originate (because they can happen completely on-chain) and can destroy the credibility of the attacked chain as a store of value and trustless settlement layer.
Moreover, if (like in the case of ETC) reorgs don't affect the price too negatively, it also creates an incentive for attackers to keep attacking the chain until they squeeze out the last drop of profit from these attacks and the cost for attacking the chain becomes higher than the cost of mining it.
How does all of this concern Bitcoin?
Bitcoin.
Bitcoin's mining algorithm is SHA-256.
SHA-256 is also used by all the subsequent forks of BTC like BCH, Bitcoin Diamond and (god forbid) BSV.
From the point of view of a SHA-256 miner, there is no difference between these chains as they all share the same mining algorithm.
As a result, miners are constantly performing a difficulty arbitrage. Their hashing power is pointed towards the chain(s) that can generate the highest amount of profit at any given time, irrespective of ideological considerations.
BTC is the dominant coin in the SHA-256 category because it has the highest ROI, not because the miners are ideologically aligned with the project (although some might be).
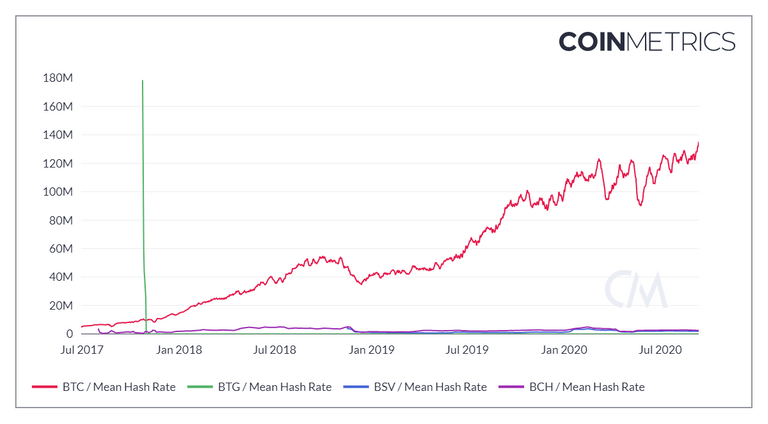
As long as BTC is the preferred coin in its mining category, the chain will be safe.
What about the other SHA-256 chains then? Are these automatically doomed?
Turns out the answer is no.
SHA-256 miners don't have an inventive to attack BCH and BSV chains because that would achieve nothing but reduce the total addressable market for SHA-256 mining.
SHA-256 miners thus have an economic incentive to keep these chains alive as long as:
Profit from mining these chains > Profit from attacking these chains
This means that owning 51% of the hash-power on a network is not in itself a sufficient incentive to attack that network. Even weak networks are protected by layers of economic incentives that can justify keeping them alive just to extract profit from mining their coins.
The real danger actually comes from 51% attacks that are ideologically motivated.
How would such attack happen on the Bitcoin network?
It's important to understand that the security of the Bitcoin network is a function of total SHA-256 hashing-power not being too liquid.
As the network difficulty on BTC increases, older generation ASIC miners are replaced by newer machines. The older miners are first allocated to mine BCH and BSV. As the difficulty on these networks increase as well, some of the oldest ASIC miners become unprofitable and go offline.
Slowly but surely a liquid market for SHA-256 ASICs builds offline.
The main question is whether this liquid hash-power can one day be hired to mount a 51% attack aiming at re-organizing the Bitcoin ledger.
As of now, it's almost certain that the answer is no.
However, nothing guarantees that the balance of power in hashing-power between active ASICs and liquid ASICs will not invert in the future.
Unless you assume that the next generation of miners will always be a full order of magnitude more powerful than the previous generation of machines, there might be a point in the future where all this "retired" hashing-power eventually becomes equivalent in power or more powerful than the active hashing-power.
If this happens and this "retired" hashing-power is commoditized on a platform like Nicehash then Bitcoin might start suffering reorgs and double spends attacks aiming at destroying trust in the safety of the network.
Who would mount such attacks?
To me, it's very unlikely that a professional SHA-256 miner would. Miners have no incentive to attack the BTC network because it would destroy the ROI of the capital they've committed to mine the chain (typically equivalent to a year of mining profit in machines and electricity).
However, one can imagine a future where a huge liquid market for SHA-256 exists and is used by a state actor to mount a "sabotage" 51% attack against the Bitcoin network. Such attack would be motivated by the threat Bitcoin poses against states monopoly on money creation.
The key takeaway here is that there still a lot we don't know about the security guarantees of POW. A lot of questions are yet to be answered.
Weirdly, it's possible that the existence of numerous Bitcoin forks actually protects the network by slowing down the formation of a dominant liquid market for SHA-256 hash-power. By providing opportunities for honestly mining smaller coins with a lower difficulty, BTC forks delay the retirement of older SHA-256 miners and prevent their use for nefarious purposes.
To me, this also suggests that the attack on ETC might have been ideologically rather than economically motivated. Since ETC actually widens the total addressable market of GPU mining, one has to conclude that the 3 attacks were not economically rationals.
One is left with many questions.
Will a powerful liquid market for SHA-256 mining ever form?
Will the decline of Bitcoin's block subsidy be enough to keep enough hashing-power around to protect the network?
Only time will tell.
Worth your time:
- A model for Bitcoin’s security and the declining block subsidy by Hasu, James Prestwich, and Brandon Curtis
See you next weekend for more market insights.
Until then,
🦊
Wow 😳! What an article ! This is a great read @f0x-society ! I just Reblogged it.
It makes me speechless to we that $ETC is still up YTD. I do not get it AT ALL !
Your article deserves to be future on CoinDesk as I kept reading about these attacks but never had I read a such detailed chronology and analysis !
Good job 👏!
PS: you should put leofinance as a tag as you would earn nice tokens and will attract some great financial/investment/crypto oriented people.
I am on vacations for a few days but I have a project to talk to you about very soon 😉 !
Thanks man, appreciate the kind words and I am happy you enjoyed the read.
Ha, can't wait to hear about the project, you know where to find me :D
NoI was just reading how the surge in DeFi is causing blockchain security concerns. This article explains why in brilliant fashion. Hadn't even begun to consider the hash power of all those retires miners. Crazy good foresight. Voted, reblogged, shabang.
Thanks mate, happy you enjoyed the article :)
I agree. The three attacks demonstrate a complete lack of interest, i.e., lack of community, lack of people interested in investing in it. And once you get uncontrolled attacks, confidence goes down the drain in a hurry. It's in a death spiral, and there's no recovery IMO.
Agreed, what's the point of a public blockchain you can't trust to securely settle value?
ETC is a zombie chain
Interesting write up too technical to assimilate for me though.
Posted Using LeoFinance
You're underestimating yourself mate ;)
Lol, sounds like a compliment.
It IS a compliment haha
Thanks bro 😄