

I'm looking into an issue for which 2 legit domains are falsely being flagged as phishing:
The issue with hivedebit was brought to my attention by @eddiespino on behalf of @starkerz. While investigating, I saw a similar problem with v4v.app. And here we are.
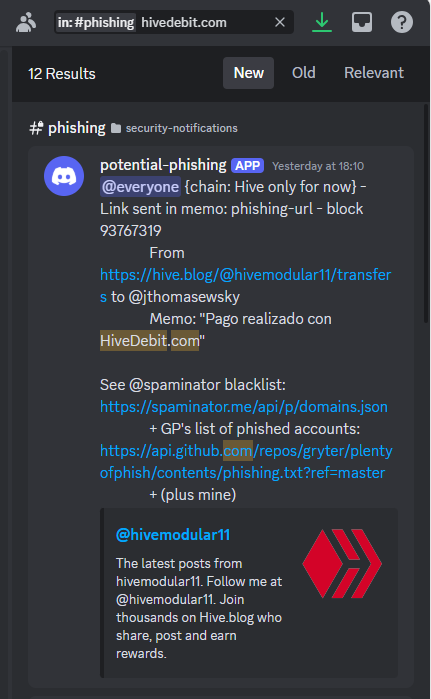
HIVEDEBIT.COM
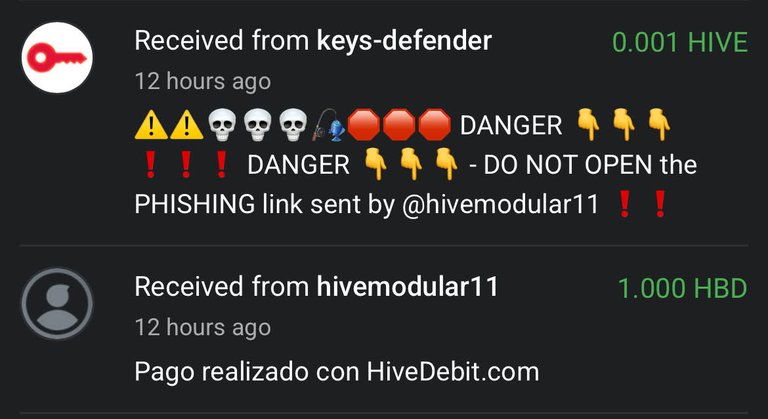
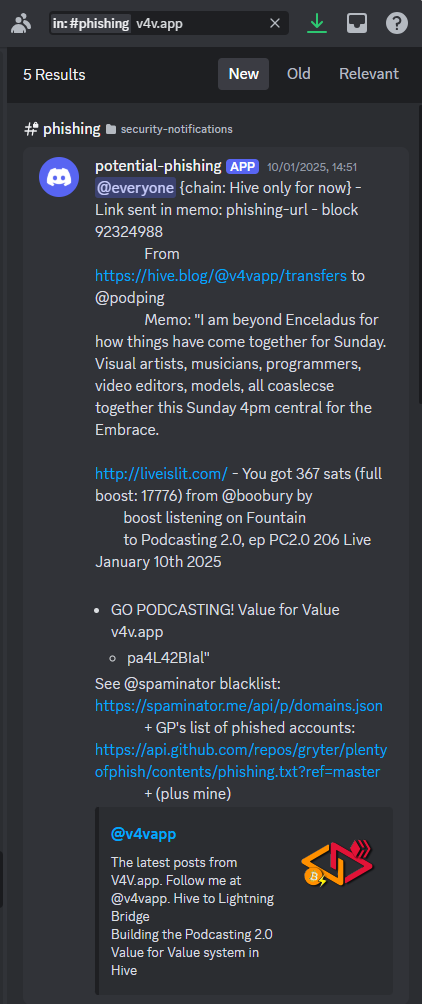
V4V.APP
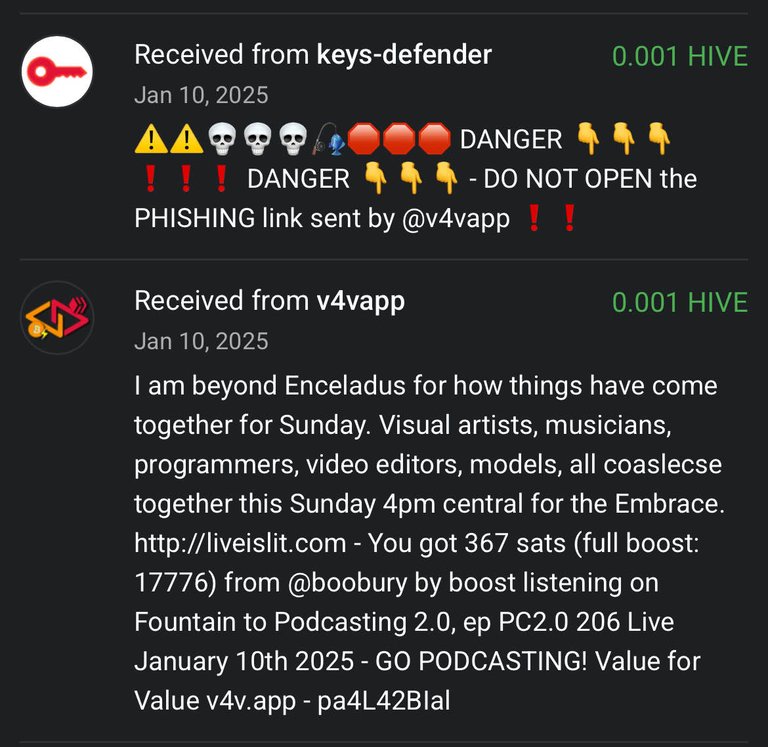
MORE CONTEXT
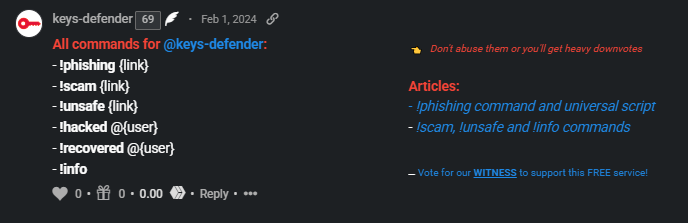
These are the bot public commands currently supported:
Who can blacklist a user or domain with the commands above:
- Top-40 witnesses
- 3 different users with reputation over 50 reporting the same user/domain
- (Myself)
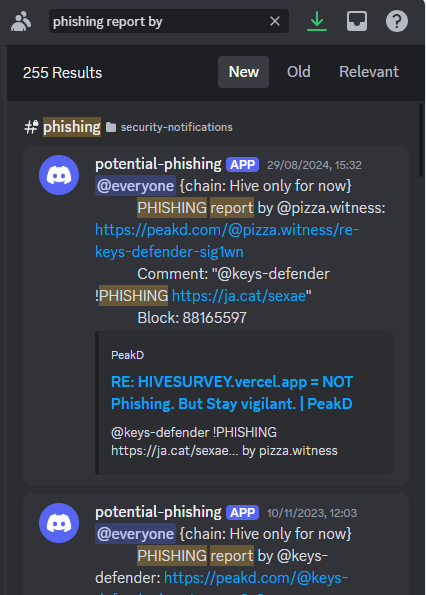
Every time someone reports anything with the commands above, it also triggers a notification in this project's Discord.
I searched in my Discord history and there are no reports for these 2 domains.
I only see notifications of these 2 domains (wrongly) marked as phishing:
- Did someone maliciously use the on-chain command and quickly delete their comment to prevent my automated reply to go out? [ it can easily be verified, and it would not stop the Discord notification ]
- Did the notifications in Discord fail for some reason, and I should dig into the code to find a bug? [ it always worked though - PS. I just did a test and this seems fine ]
The only other explanation is that these domains were added for some reason (by mistake or legit reasons) in other blacklists that this bot consumes:
1. @spaminator's blacklists:
- https://spaminator.me/api/p/domains.json
- https://api.github.com/repos/gryter/plentyofphish/contents/phishingurls.txt?ref=master
@logic @guiltyparties any clue?
2. My own lists stored on Hive: https://peakd.com/@keys-defender/phishing-db
( These lists are periodically migrated to my own database as required )
But only I have access to the latter. And these 2 flagged domains are not (and never were) there.
If the issue is not identified shortly, I'll add those domains to a whitelist to prevent more automated memos from going out incorrectly.
UPDATE 1
The issue seems to not be there anymore for v4v.app. It's still there for hivedebit.com so it should be easy for me to to find out where it's coming from.

UPDATE 2
It looks like it was just an innocent bug 🐛 - HiveDebit.com partially matched with another blacklisted domain.
For v4v.app instead, it's not currently being flagged as phishing but I would like to understand why it was. Waiting for some answers from the maintainers of the blacklists this bot consumes.
My thinking is that v4v might have been temporarily marked as compromised during the recent hack.
Appreciate the work I do? (that never received any sort of funding) VOTE for my witness
Can you show me anything about where @v4vapp was used to write a comment? DM me a link to a block or something. I can't find it.
No, I never said that @v4vapp executed one of my commands. If anything someone else could have maliciously reported it. But I'm more inclined to think someone else did something by mistake, so I'm trying to figure it out (logs and queries on blockchain data)
When was that attack/breach on @v4vapp? Maybe that has created some sort of malfunction and falsely flagged it, @keys-defender
The attacker could have reported themselves (v4v.app) if they had access to the Hive account, but I believe that was never the case.
Ah, okay. A command is required then. That part went over my head 😅
Articles:
- !phishing command and universal script
- !scam, !unsafe and !info commands
_ Vote for our WITNESS to support this FREE service!
- !phishing {link}
- !scam {link}
- !unsafe {link}
- !hacked @{user}
- !recovered @{user}
- !info
Neither of these were done via on-chain command.
It might be a good time to modify your code to include how it got there when added.
I thought the Discord notification would be enough. It always worked (and still does - just tried).
I also checked the bot logs and confirmed that it was not added via an on-chain command
Discord usually works but it isn't 100% reliable (fairly close though). It's probably something you want to have in your DB though as Discord may not always be the way you want to interact with the data.