A few days ago, the user @gaottantacinque brought a cross site scripting bug to my attention. This one, which was found there, was already fixed by the site operator @penguinpablo. But I did a little more research and found another XSS vulnerability on the site. The stored XSS vulnerability I found is at least as dangerous as the one fixed before.
With the vulnerability I found, the operator simply has to use the same method of outputting code that he has already fixed before, just in a different location. Other parameters - HTML data that can be stored in the block chain in the profile should not be rendered in a frontend to protect the security of the user.
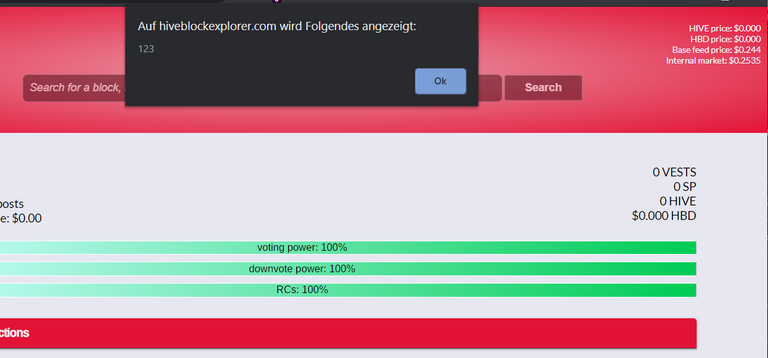
I have already sent a message to the developer and pointed out where the vulnerability is on the page.
The same problem exists on the page for the Steem Blockchain. So the older tool Steemblockexplorer.
Unfortunately this is not the first critical vulnerability I have found in applications around Hive / Steem. In the past I have found many such vulnerabilities and have reported them to the developers of the project. And here is my request to you project developers: Please check your frontends for XSS! Since in most cases money is involved, such critical and easy to solve security holes do not belong here.
Thanks
~louis
I just fixed this issue.
All URLs on both steemblockexplorer.com and hiveblockexplorer.com should now be safe.
Awesome. Thanks for the fix!
@penguinpablo Your comment cointains a link that is on my blacklist ❗ ❗ ❗ ❗
Readers, do NOT click on any link on this comment above.
Link: "hiveblockexplorer.com*" => DO NOT CLICK
More info: https://hive.blog/hive/@gaottantacinque/hiveblockexplorer-com-is-vulnerable-to-stored-xss https://hive.blog/hive/@keys-defender/new-feature-phishing-detection-and-auto-reply
Comment 10% downvoted to make it less visible. This message is self-voted to be more visible.
@keys-defender
@penguinpablo Your comment cointains a link that is on my blacklist ❗ ❗ ❗ ❗
Readers, do NOT click on any link on this comment above.
Link: "hiveblockexplorer.com*" => DO NOT CLICK
More info: https://hive.blog/hive/@gaottantacinque/hiveblockexplorer-com-is-vulnerable-to-stored-xss https://hive.blog/hive/@keys-defender/new-feature-phishing-detection-and-auto-reply
Comment 10% downvoted to make it less visible. This message is self-voted to be more visible.
@keys-defender
😪
I assumed the same sanitation fix was applied to all fields.
Apparently not and this is even on the user landing page, probably as dangerous as the one under "/transactions" as a link to the user page could still be shared as proof of payment (even though slightly more suspicious).
Maybe @penguinpablo hotfixed the one I reported and was going to fix the other issues in a following release. #shipit
Adding the compromised domain back into @keys-defender's blacklist to warn users via auto-replies..
!blacklist https://hiveblockexplorer.com*
!blacklist https://steemblockexplorer.com*