 Image source
Image source
Blockchain is a public ledger of transaction that stores data and information. This deals with blocks and every block is verified by validators to ensure the smooth running of information in a transparent way. Despite the transparent nature of some blockchains (bitcoin), there is still some important information that is not revealed. You cannot find the name of those that transact, but other information remain public, of which is not bad at all
However, wouldn't it be cool if third parties cannot trace the information of the transaction between two people? Well, I think it's a great one because that would signify more security and scalability. This is where the Mimblewimble gets its feet into the blockchain
What is Mimblewimble protocol
I watched harry potter some years ago, and heard the word MIMBLEWIMBLE when it was used. It's a course used to tie the tongue, so they call it the tongue tying curse. It was just a movie so I never thought of anything else other than, "hey, just catch fun and keep watching". But when I heard about the Mimblewimble protocol, it rang a bell. So this was coined from the movie? Fantastic
But how does this correlate? Well, the tongue tying curse keeps the victim silent and not able to reflect/expose somethings to others, so I think that's why the MIMBLEWIMBLE word was used
So because the mimblewimble protocol aims to be security conscious, packed with maximum anonymity, and scalability, the word mimblewimble was the best to use. That's not bad if you ask me
- The private transaction through the security framework is one of the best features the mimblewimble protocol has that I so much love. The bitcoin blockchain has a fantastic security level, and of course, it's cool. However, the mimblewimble has a cryptographic way of making transactions private in such a way that you can't actually see who is transacting with who let alone the person involved and other information.
- Transactions can be verified without knowing a single thing about what transpired between the parties, and without storing any data in question, and this enables a more private blockchain.
Tom Elvis Jedusor's aims and objectives of creating the mimblewimble side chain to bitcoin was to improve privacy, scalability and fungibility. I perceived the reason for this protocol was to close the bitcoin blockchain's loop holes
Why?
To ensure security on the blockchain, a lot of space is utilized. And as we all know, security is the most important thing when it comes to securing funds. So, in other to have maximum security, some informations that isn't needed are also stored on the blockchain and these activities takes much space which affects the blockchain scalability, speed, and so on
So that's why the mimblewimble protocol was initiated to trash the problem in the bitcoin network as a side chain blockchain
How the Mimblewimble blockchain protocol work
First, let me explain the technical aspect.
We all know that every blockchain deals with information/data, and blocks are created to verify every data sent into the system. So when data is sent into the mimblewimble blockchain, these are the things that happens
There is something called the CUT THROUGH in the mimblewimble protocol. It works as a compressor to compress every block with redundant information to a smaller size by removing the ones that are not important, and this process doesn't affect the security of the blockchain in any way
The conjoin cryptographic function is another fantastic way that deals with the elimination of third parties in every transaction. Transactions are capped as one and this makes it difficult to know which transaction is for Mr. A or B. Only the parties involved in the transaction can see the details, but no other person can understand how things went between the two parties. That's what the conjoin cryptographic function does on the mimblewimble protocol
My design
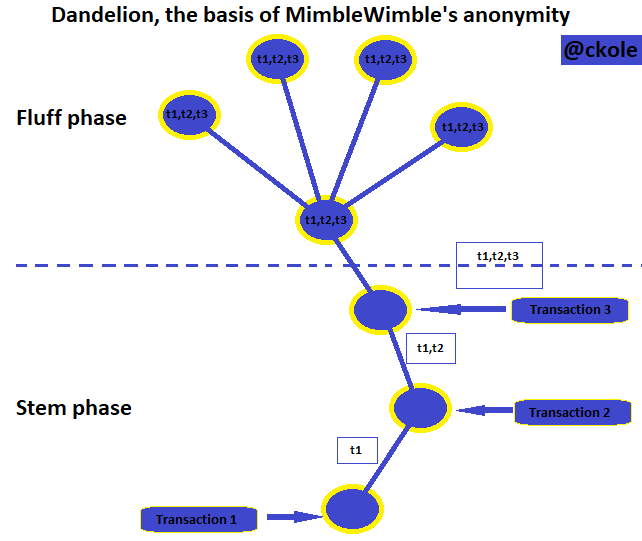
The dandelion is also a very important feature of mimblewimble. It works to make the origin of a transaction anonymous, all in the name of providing privacy. This is done by selecting nodes at random (A very unique mathematical implementation) where data is sent, and these nodes cannot trace or guess the origin of the information. I call it the confusion strategy, but it's called the ROOT PHASE
The next step is the FLUFF PHASE, where the data is sent to a transmitter, and from there to all mimblewimble nodes. But there's a process called TRANSACTION COMPENSATION that occurs in-between. This enables the blockchain to mix input and output in case the data's origin was traced, there would be no way to know the exact data/information it carries because confusion has been injected into the system. (Bravo!)
Permit me to use an example to explain how it works in the real world and not in the technical way
Shadrach, and Meshach sent $5 each to Abednego
Abednego is having $10 in his wallet (Note that two people already transacted with Abednego)
Abednego now transacts with Nebuchadnezzar by sending the $10 to him.
Now, Abednego would have the transaction details of Shedrack, Meshach, and Nebuchadnezzar, because he directly transacted with them
Shedrack will only have the transaction details he made with Abednego, likewise Meshach
Nebuchadnezzar that received the $10 would never know where the money came from. He can never understand that it was Shedrach and Meshach that sent $5 each to Abednego. The only details he can have is the transaction he made with Abednego
Every other information attached to the transaction has been discarded by the mimblewimble protocol thus enabling total privacy where the third parties cann] neither see nor have a glimpse of what transpired between two people
Confidential Transactions (CTs)

Confidential transaction was developed by Creg Maxwell, and this is all about confidentiality. In CT's, the numbers of transactions occurring on the MWP, is always encrypted in such a way that only the people transacting can see the amount that is being transacted, and the outsiders can only verify the correctness of the transaction, but cannot see what happened inside the transaction
CT's is just a mathematical mechanism that allow only the parties involve to see what's happening in the transaction, however, the third parties are able to validate that the transaction is according to the consensus
So in a simple way, a confidential transaction is a protocol that hides the amount and the address of the Bitcoin sent to another person
How does CT's work
Let's assume Shedrack is having 10BTC in his wallets and wants to send 5 to Meshack. These are the steps
The first thing is to get Meshacks bitcoin address. After that, Meshack (the person sending 5btc) would use the address to create a blinding key, and hash both together. Hash in cryptography means generating another value in other to meet the encrypted demand, which makes it impossible for anyone to crack
|
The hashing creates a confidential address, and this is used to send 5bt to Meshack. Because Meshacks bitcoin address was used to create a blinding key, he would be able to see the transactions and receive the 5 bitcoin sent by Shedrack. In this wise, only the two parties can see the entire transactions because the blinding key created would make the transactions invisible to others on the public ledger
More technical part of CT's
As explained above, there are some things happening internally to make Shedrack and Meshack's transaction smooth
- It uses the ScriptPUBkey to verify the ownership of the address (This is done mathematically to ensure that the amount of BTC to be sent is real or spendable)
- Binding key is created
- Then a Pederson commitment
Pedersen commitment uses a public group (G) of large order q in which the discrete logarithm is hard, and two random public generators g and h. Random secret r is chosen in Zq, the message m is from any subset of that. The commitment is C(m,r)=gm⋅hr
***This was put together from section 3 of the Non-Interactive and Information-Theoretic Secure Verifiable Secret Sharing, in proceedings of Crypto 1991
What happens at this end is that the pederson commitment makes sure that the total input is equal to the total output. If there's any change in value, the transaction would be broken
- Lastly, the ecdh nonce is used to relate the encrypted information to the recipient in a way he can decipher it.
The confidential transaction is a very important protocol used for maximum privacy. Only the people involved in the transaction can have access to the details, except the blinding key is shared to a third part
|
How Mimblewimble Protocol can be utilized on the Bitcoin Network to enable anonymity of transactions and improve scalability.
Bitcoin is pseudonymous, but its privacy level is questionable. This low privacy makes it less scalable.
How? |
When transactions are carried out on the bitcoin blockchain, all the information/details of the transactions are recorded and made public. This process takes a lot of space which makes the bitcoin blockchain size enormous. So we can deduce from this that the issues with the bitcoin blockchain is privacy and scalability
So how I think Mimblewimble protocol can be utilized on the bitcoin blockchain to achieve anonymity and scalability is simple
Since the aim and objectives of coming up with the Mimblewimble protocol is to eliminate these mess, then the integration of Mimblewimble with the bitcoin blockchain is the solution
Mimblewimble can be implemented as a sidechain, or soft fork into bitcoin as an extension block. And as explained, there are some implementations in the mimblewimble protocols that enhance scalability, anonymity, and fungibility
The Coinjoin protocol can help to increase the bitcoin privacy. It's not everyone that loves to disclose what they do with their money, with the coinjoin protocol, there is uttermost privacy for every users. [You can check this documentation on GitHub to see more about coinjoin](https://github.com/nopara73/ZeroLink/)
The word coinjoin if split means joining coins. Different senders using the blockchain would participate with their coin, and the server coordinating these input would verify all these coins after they might have signed the transactions. In this wise, their address is mixed and there is no possible way for anyone to know who owns a particular transaction, meaning every transaction on the blockchain cannot be traced to anyone. Also
You can use the [wasabi wallet](https://wasabiwallet.io/) built with the coinjoin protocol for bitcoin anonymity to secure your transactions by disabling third party from viewing your transaction details
The Confidential transactions is also an important part that can be used for bitcoin anonymity. The encryption of information to and fro the network makes it difficult for others to know what's happening in every transactions carried out on the blockchain. By and large, I think using the Mimblewimble strategy of the coinjoin, CT's and other protocols can help improve the Bitcoin anonymity and scalability
There's certainly nothing with advantages without its other side. Let's look at the pros and cons of the mimblewimble protocol
The mimblewimble pros
Scalability: Because of the decentralized nature of blockchain, it's meant to quickly process any transaction regardless of the volume and the number of users using the network at the same time or at interval. So the independence between the speed and the number of participants is what determines the scalability of a blockchain. The Mimblewimble protocol was able to manage this to a high level and this makes it more unique than the bitcoin network.
Fungibility:Mimblewimble offers the atmosphere where currencies can be exchanged or spent without anyone knowing the total of what you have in your wallet. The anonymity helps in this regard because the address of the recipients would not be displayed, so this helps to keep the transactions untraceable. Also, it's a crytptocurrency property that does not distinguish between units and value. They are always considered as equal.
- Anonymity: The public addresses of the users are not registered on the blockchain, so no one can know or understand who's making transactions, which means the origin of the transaction cannot be traced. - Redundancy: The mimblewimble protocol only keep the essential part of the transactions and remove the other parts that are not needed for other people to see. This is one huge difference between the bitcoin blockchain and the mimblewimble protocol.
The mimblewimble cons
Attack: The 51% blockchain attack is still prominent. The mimblewimble protocol can still be attacked because every blockchain is still facing that problem. Though the Mimblewimble protocol is scalable enough and the anonymity is great, we cannot still confirm that it's 100%secured, however, the anonymity of transaction it offers still helps to reduce hacking as transactions cannot be traced
Conclusion
Tom Elvis Jedusor (A character in Harry potter) came up with the mimblewimble protocol. Sure, it was like a play, but later turns out to be what many projects are embracing. The bitcoin network was improved with the mimblewimble protocol because of its scalability and privacy. There is always a way forward in every situation and conditions. The mimblewimble protocol happens to be the way forward that helped the bitcoin network to improve it's privacy and scalability
Thanks for reading
This is ckole the laughing gas
One love
Posted Using InLeo Alpha


