
Blockchain technology per se has advanced a lot with the issue of information security involved in financial transactions or simple communication between network points.
With each new phase of WEB3 and with the arrival of new protocols, privacy, security and transactional speed have been improved, there is still room and need for further improvements - proof of this is the persistence of the blockchain trilemma.
Cryptographic algorithms for authentication, signing and development of layer 2 protocols for scalability continue to address these issues, but in a decentralized environment, the disruptive purpose of cryptographic protocols demands better information privacy to ensure users' freedom and anonymity.
Thus, while blockchain technology provides great advantages such as transparency, immutability and decentralization, it lacks the ideal level of privacy for some transactions. The combination of zero-knowledge proofs (ZKPs) therefore emerges as a mechanism to provide users with a powerful combination of immutability and security.
Let's understand better how this mechanism works.
WHAT ARE KNOWLEDGE TESTS?
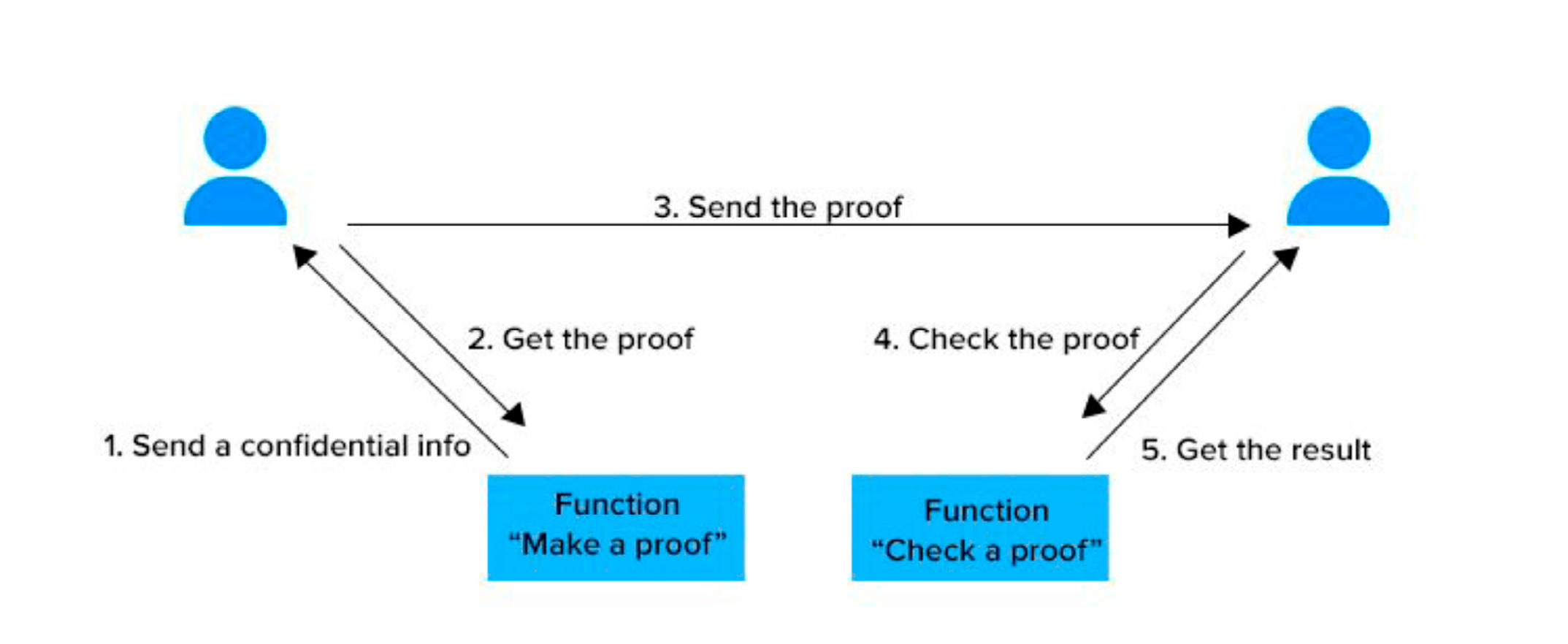
They are what allow one individual to prove to another that an argument is true, without having to provide any other information that goes beyond the validity of the argument itself.
The parties involved are the prover and the verifier, and the argument they keep secret is the witness. The main purpose of these tests is to verify the validity of the information contained by the parties revealing as little information as possible.
Zero-knowledge proofs can be quickly verified and take up much less space than standard Bitcoin transactions, for example, and can be divided into two formats: zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) and zk -STARKs (Zero-Knowledge Succinct Transparent Argument of Knowledge).
HOW IT WORKS
The perception of the lack of privacy of some protocols led developers to work focused on building a mechanism for real information privacy, without even the need for information exchange between the parties involved in a transaction.
Thus, the Zero-Knowledge Proof was created, a cryptographic scheme proposed in 1980 by Silvio Micali, Shafi Goldwasser and Charles Rackoff. This mechanism works as a form of cryptographic validation that precedes the execution of transactions.
In this method, one party (Provider) tries to prove to the other (Verifier) that it has the information expected to complete the transaction.
Here, disclosure of sensitive information between the parties involved in the transactional process, such as keys or codes, is not required. The algorithm establishes “proofs” of knowledge that, if fulfilled, create trust between the parties that both know/hold the information (complementary or similar) necessary to effect the transaction.
Confused? Let's look at a practical example of how this proof-of-knowledge concept works.
THE CAVE AND THE ZERO KNOWLEDGE PROOF
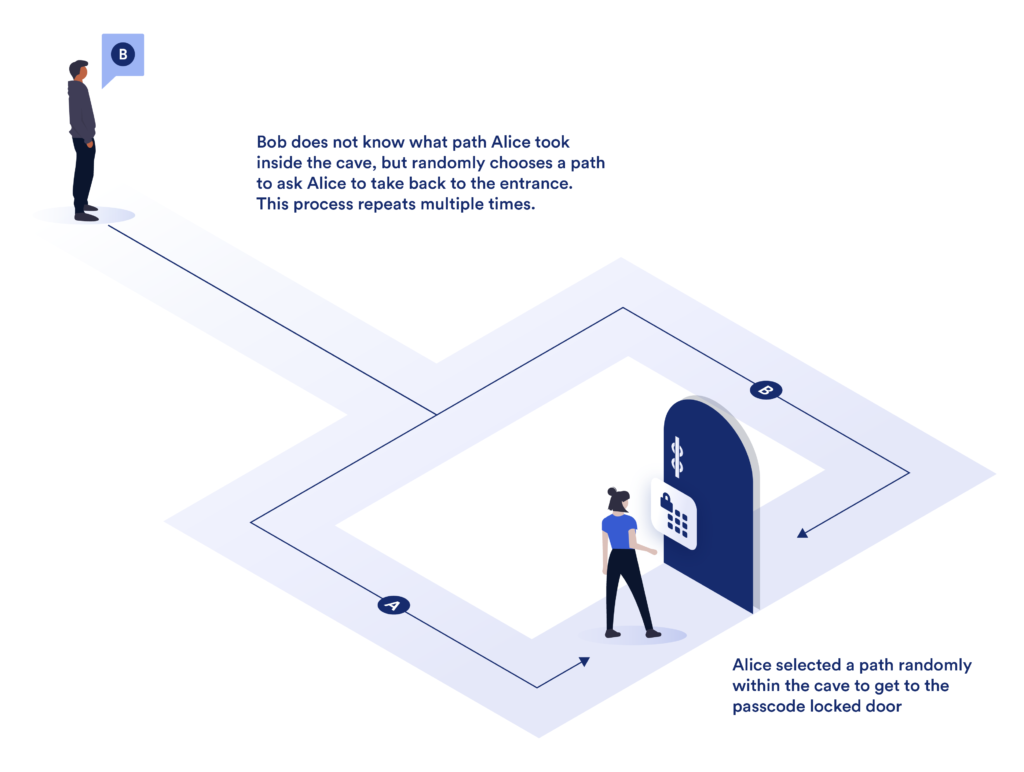
To understand more intuitively how zero knowledge proof works, we will use the famous cave case. A cave has only a single entrance, but it unfolds into two paths (path A and B) that connect so that, if traveled, they lead back to the cave entrance.
Dividing the route, there is a common door locked to the password.
Bob is responsible for installing and configuring the password for the door that divides the cave paths and wants to verify that Alice actually knows the password for the door as she claims.
Alice (provider) wants to prove to Bob (validator) that she knows the door lock password, but without revealing what the password is to him. To do so, Bob stays outside the cave and Alice chooses one of the two forked paths, returning some time later to the cave entrance by the opposite way to which she entered.
Therefore, the fact that Alice has completed the journey back to the entrance proves that she knows the password to the door, since only then could she have unlocked it and completed the journey.
Thus, she performed a zero-knowledge proof process.
She has demonstrated that she has the knowledge to complete the task without needing to tell Bob the password.
Once this process is complete, Bob's degree of confidence that Alice certainly has knowledge of the door password is high, even though she has not disclosed the password code.
You may ask, “Could she also prove that she knew the password by telling Bob the code”. Yes, but in this case, if Bob was bluffing and didn't actually know the password, from that moment on he would also have that knowledge. And this is what the zero-knowledge proof seeks to avoid.
The computational principle of the ZKP system works similarly in cryptography. It creates trust between the parties in a transaction, ensuring the fulfillment of “parameters” that validate the knowledge between them to verify the honesty of the parties when validating a transaction without either of them knowing, in fact, the content of the information held by the other. .
ZKP PROPERTIES

Integrity: The verifier can only be “convinced” that the provider is honest and has the correct information if the knowledge validation tests are completed.
Solidity: if the provider cannot prove that it has the correct information to complete the transaction, the validator does not validate it.
Zero knowledge: the validator will only validate information that is proven to be true and valid from the proof of zero knowledge.
Although their properties are immutable, ZKP protocols can be divided into interactive and non-interactive.
INTERACTIVE ZKP: HOW DOES IT WORK?
The zero-knowledge interactive system basically demands that the interaction between validator and provider be done synchronously (“live”) to confirm transactions.
The main problems presented by this model are:
Limited transferability – To prove that you have a “knowledge-solution” more than once to more than one verifier, the entire process needs to be repeated by the provider.
Not scalable – Interactive ZKPs require both the verifier and the tester to be online at the same time, which makes the whole process more complex and difficult to operationalize.
NON-INTERACTIVE ZKP: HOW DOES IT WORK?
Created in 1986 to solve the problems of the interactive model, the non-interactive Zero Knowledge Proof does not require an interactive process, that is, it does not demand synchronous action between the parties as a factor that makes the transaction validation impossible.
Here, a hash function is chosen to randomly define the cryptographic challenge to be solved by the prover based on the knowledge/information he holds.
This process is made possible by the Fiat-Shamir heuristic methodology - a technique that, by obtaining an interactive proof of knowledge, creates a digital signature that can publicly verify a fact without the tester having to be online all the time.
WHAT ARE ZK-SNARKS?
Cryptographic proof-of-knowledge engine for transaction validation based on Zero Knowledge Proof.
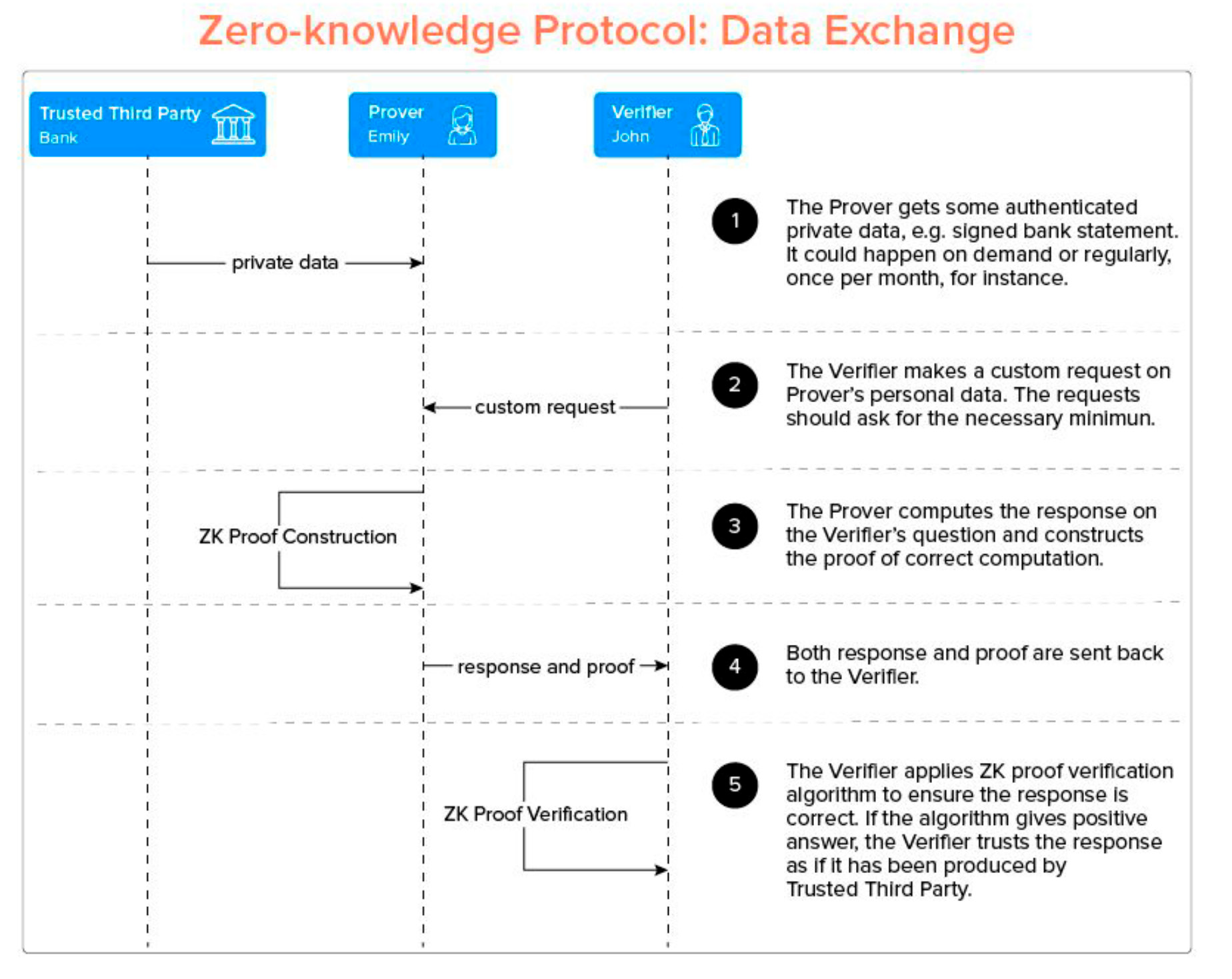
Zero-Knowledge Succinct Non-Interactive Argument of Knowledge is a non-interactive ZKP based technology and is the cryptographic proof engine that uses a secret key to validate the zero knowledge proof transaction process used in the Zcash protocol and also in the payment system. based on JP Morgan Chase Bank's blockchain.
This mechanism works in the Key Generation process (establishing a parameter to generate a pair of keys, public and private, used to prove and verify transaction information).
The structure of this mechanism is based on an initial structure that depends on trust (initial trusted setup) on a set of public parameters, which only if validated build zero knowledge proofs.
In this model, the dishonest prover has a very low chance of success when trying to defraud the system, and the speed with which transactions are processed here paves the way for zk-SNARK technology to be used as both a privacy and a scalability solution.
The basic properties of this proof of knowledge model are: it is interactive, follows the ZKP soundness principle and requires a “trusted witness”/third party to be involved in the validation process.
ZK-SNARKS OPERATION
WHAT ARE ZK-STARKS?
Zero-Knowledge Succinct Transparent Argument of Knowledge is an alternative cryptographic proof of knowledge mechanism to zk-SNARKs that is considered to be faster and cheaper.
Based on encryption techniques that do not depend on an initial trust setup, this proof of zero knowledge model is based on collision-resistant hash functions and increases the operational dynamics of transaction processing, further reducing processing time.
Finally, here, the increase in computational demand due to the increase in network operations does not imply an increase in the number of communications between providers and validators, as in zk-ZNARKs, it is also one of the great differentials of this proof-of-knowledge model. and that strengthens the cost-benefit and speed pillars of the model.
APPLICABILITY PROOF OF ZERO KNOWLEDGE MECHANISM IN BLOCKCHAIN
The potential of the Zero Knowledge Proof mechanism is already clear: a significant enhancement in the security and privacy of information in blockchain networks, but in what practical ways can this mechanism be incorporated into the operationalization of Web3 protocols (whether smart contract protocols, layer 2, layer 1, Dapps etc.)?
Some of the practical applicability cases in which the mechanism is
very useful are:
• Confidential/Private Open Blockchain Transactions - In these cases, the transaction data is encrypted and a kind of “proof” of the transaction is published in the open blockchain ledger to prove that the transaction was honestly and correctly validated based on no zero knowledge proof.
• Sharing of complex documentation - the trend of using identification documents, such as ID or any registration numbers in digital form to validate or sign transactions or operations, has increased. In such cases, ZKPs, which have the potential to encrypt data in chunks, allow users to control certain blocks to be accessed and the visibility of information contained only in those chunks, allowing access for some users while restricting others (who do not comply with the proof of zero knowledge).
ADVANTAGES AND DISADVANTAGES OF THE ZKP MECHANISM
BENEFITS
- Simplicity - Does not require complex encryption methods.
- Privacy - Increases users' privacy by circumventing the need to exchange personal information on public blockchains.
- Security - Strengthens information security.
- Scalability - Increases blockchain throughput and scalability with fast and responsive transactional processing to be implemented in different types of interaction.
DISADVANTAGES
- Limited - These protocols are based on mathematical equations and numerical answers, requiring translation to any other method of exposing data.
- Computational power - About 2,000 calculations are performed per ZKP transaction, demanding time and energy to solve.
- Vulnerability - This algorithm is not immune to potential vulnerability against advanced technologies such as quantum computing.
ZCASH AS A ZERO-KNOWLEDGE PROOF PROTOCOL
Zero knowledge mechanisms have been used by blockchains such as Zcash to allow users to create transactions while preserving the privacy of information such as monetary value, sender and recipient addresses.
Considering the privacy demanded by cryptocurrency investors - who don't want to see their transaction histories completely public and open to anyone - Zcash, an open source and permissionless blockchain platform that offers transparent and protected transactions, adopted ZKP as a mechanism for complementary authentication.
The protocol offers the possibility for transactions to be governed by a t-addr (transparent electronic address), just like bitcoin transactions, or through zero-knowledge proof zk-SNARKs, where transactions are controlled by a z-addr. (private email address).
Zcash was the first case of application of ZKP in cryptocurrency projects.
The evolution of the cryptographic ecosystem over the last decade
undeniably, it was accentuated as a result of technological advances and the explosion of the cryptoactive and Web3 segment.
With privacy, transparency and security as drivers of this new era, the process of processing, managing and handling data faced obstacles such as the blockchain trilemma, which did not make it impossible, but led to the emergence and development of new processing and information sharing.
In this sense, the proof of zero knowledge mechanism emerges as a solution to a problem already seen across the crypto world: the lack of complete information privacy.
And, although it is still evolving and needs further dissemination, it is worth considering the Zero Knowledge-Proof mechanism as a promising resource in complementing blockchain technology.
Posted Using LeoFinance Beta
The rewards earned on this comment will go directly to the people(@cryptosimplify) sharing the post on Twitter as long as they are registered with @poshtoken. Sign up at https://hiveposh.com.
Very interesting.
I'm glad that you like it
Posted Using LeoFinance Beta
Good information. I always wanted to know what is Zk-starks !
Posted using LeoFinance Mobile
I'm glad that you like it and know it is a litle more easy to understand how this works
Posted Using LeoFinance Beta
This is actually very nice explanation , now I get idea how ZK proof works.
!CTP
Posted Using LeoFinance Beta
I'm glad that you like it.
I will always try to bring good content.
Posted Using LeoFinance Beta
This content is very welcome in the Zcash community, feel free to hashtag #zcash and #zec for this to see it makes it way into the community feed.
Posted Using LeoFinance Beta
I updated the tags to see if can reach more people.
Thanks a lot for the advice
Posted Using LeoFinance Beta
!PIZZA
PIZZA Holders sent $PIZZA tips in this post's comments:
@phusionphil(1/5) tipped @cryptosimplify (x1)
Join us in Discord!
I'm glad that you like it.
I will try to always bring good content and share some knowledge.
Posted Using LeoFinance Beta