Since 2017 CIA has been planning a decentralized internet, where we have to AUTHENTICATE to get in, Thats just a fancy way of describing how we login with KEYCHAIN https://wikileaks.org//vault8/#Hive
thats what it is... authentication
its all just buzz words
look at the logos


Come chat about this on @projectcamelot telegram https://t.me/projectcamelot

https://wikileaks.org//vault8/document/repo_hive/
Vault 8
Source code and analysis for CIA software projects including those described in the Vault7 series.
This publication will enable investigative journalists, forensic experts and the general public to better identify and understand covert CIA infrastructure components.
Source code published in this series contains software designed to run on servers controlled by the CIA. Like WikiLeaks' earlier Vault7 series, the material published by WikiLeaks does not contain 0-days or similar security vulnerabilities which could be repurposed by others.
Releases Documents
Hive Repository
The files in this code repository were created between August 2013 and October 2015, but the development of Hive started much earlier. Older versions of the code are not available as the previous source code control system (subversion) was not properly migrated to git.
The repository contains the following branches: 'armv5', 'autotools', 'debug', 'dhm', 'makemods', 'master', 'mt6', 'polar-0.14.3', 'polar-1.1.8', 'polar-1.2.11', 'polar-1.3.4', 'solarisbug' and ' ubiquiti'.
N.B.: The files below originate from the master branch of the repository; if you want to access other branches or revisions, please download the zipped repository file and checkout branches and/or revisions on your local computer.
https://wikileaks.org//vault8/document/repo_hive/hive.zip
ancient CIA Hive Source code
https://wikileaks.org//vault8/document/ documents
chat about HIVE BLOCKCHAIN here on telegram https://t.me/hiveblockchain
https://wikileaks.org/ciav7p1/cms/page_7995396.html
CIA HACKING TOOLS: HIVE lol wow
https://wikileaks.org/ciav7p1/cms/files/UsersGuide.pdf
https://wikileaks.org/ciav7p1/cms/files/DevelopersGuide.pdf

coincidence?
nah this is the cia lol ... this is a fight against China CCP . CIA vs CCP steem vs hive eos vs telos
Centralizationists vs Decentralizationists
A WHOLE NEW INTERNET based on decentralized protocols with HIVE blog as one of its OGs will make HIVE worth anywhere from $100 to $10 to $50,000 EACH because we can do so many more transactions than BTC. We just need more faucets and curators and people willing to post with #share2steem style system , we nEEED SHARE2HIVE !!!
more
https://wikileaks.org/vault7/#Hive
Vault 7: HIVE
Today, April 14th 2017, WikiLeaks releases six documents from the HIVE project created by CIA's "Embedded Development Branch" (EDB).
does @dan know about this lol
Hive
14 April, 2017
Today, April 14th 2017, WikiLeaks publishes six documents from the CIA's HIVE project created by its "Embedded Development Branch" (EDB).
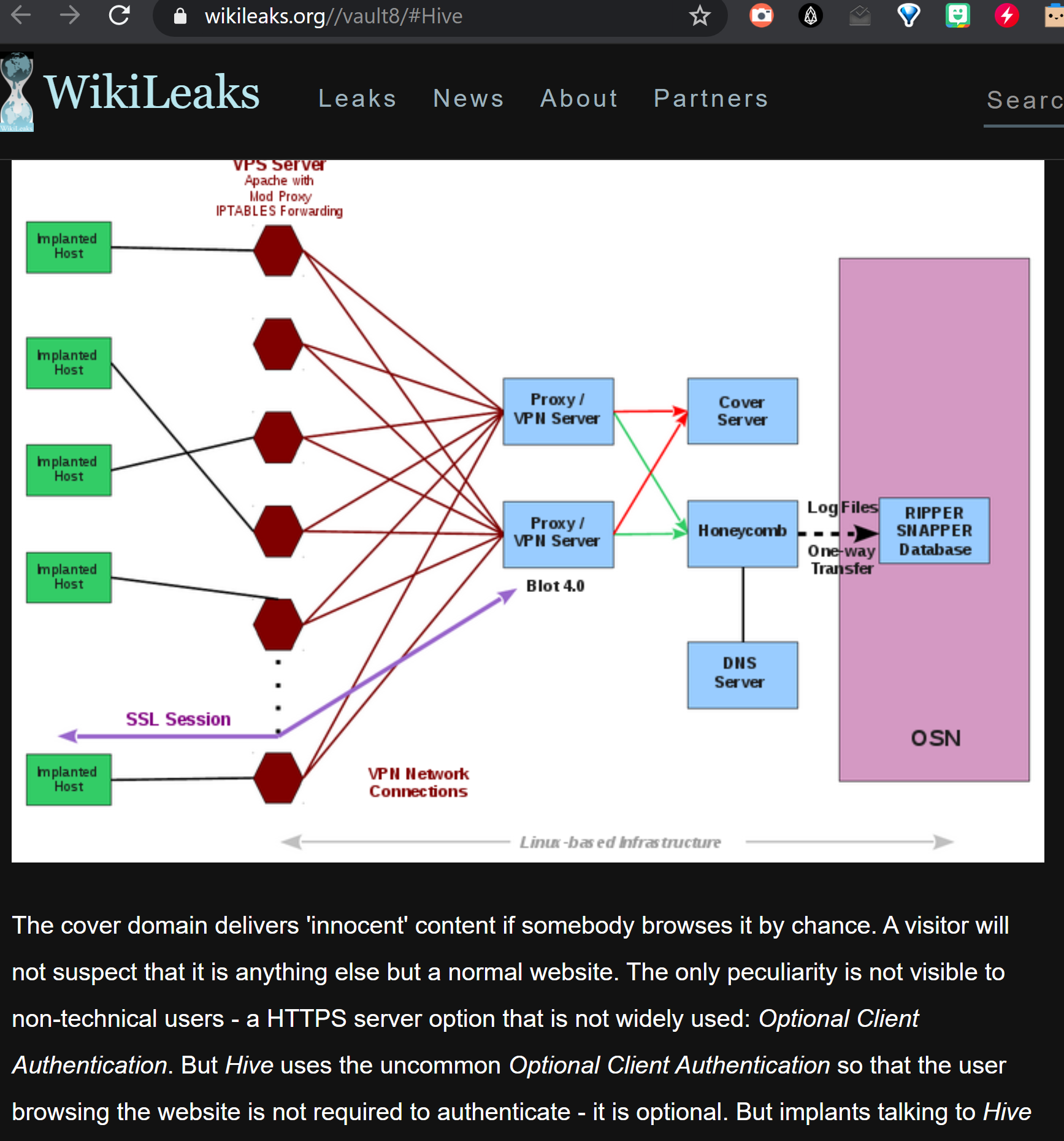
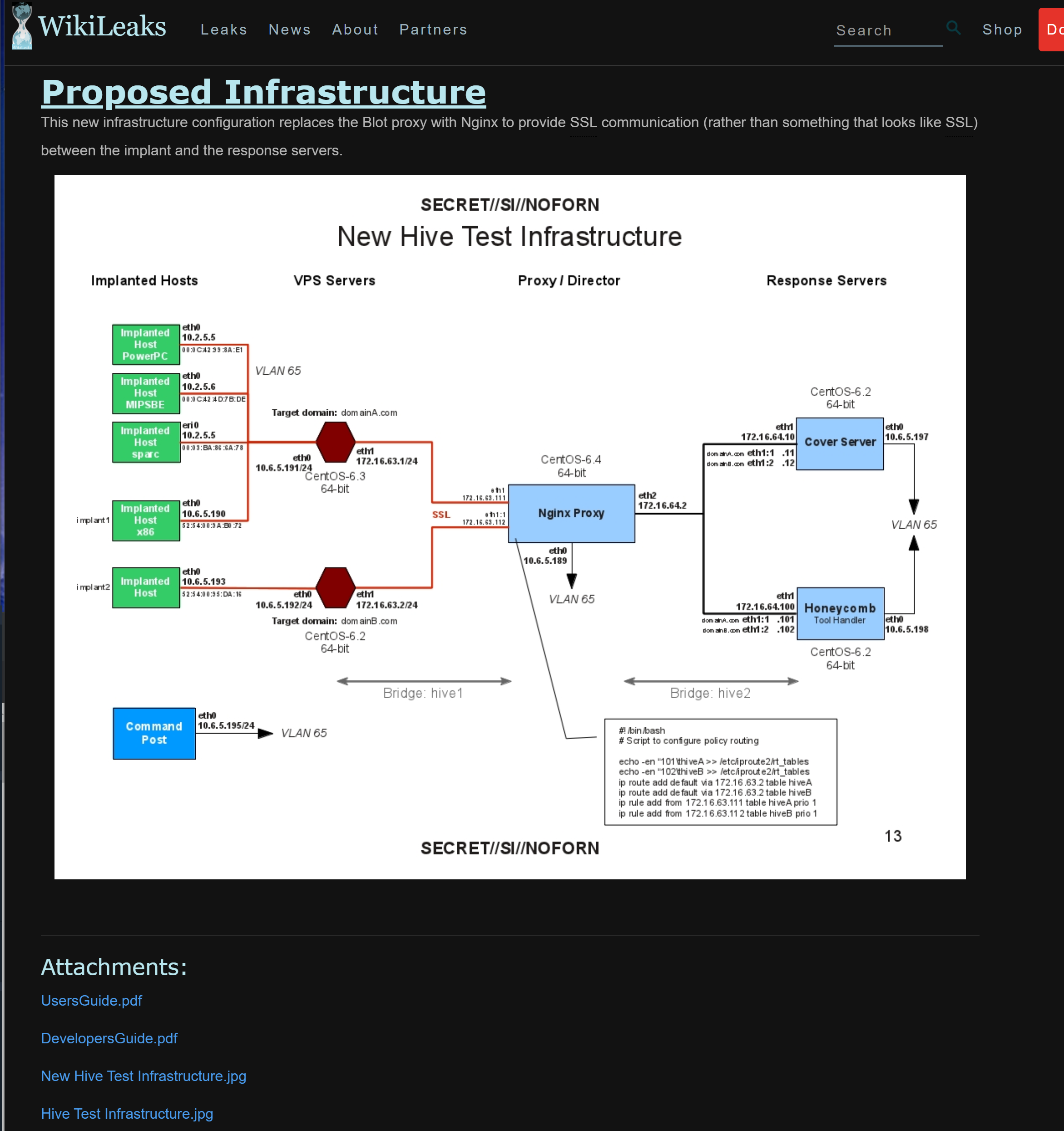
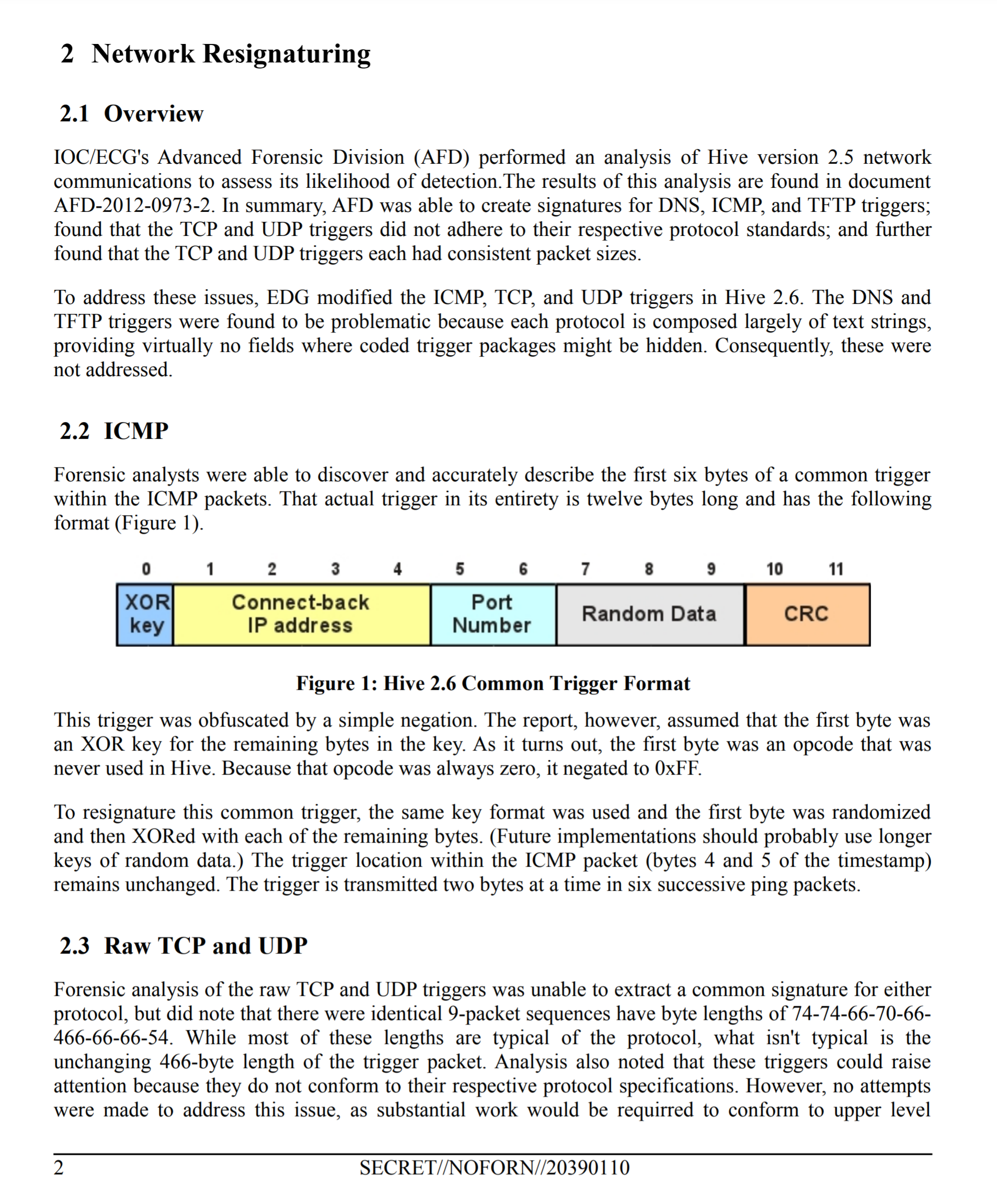
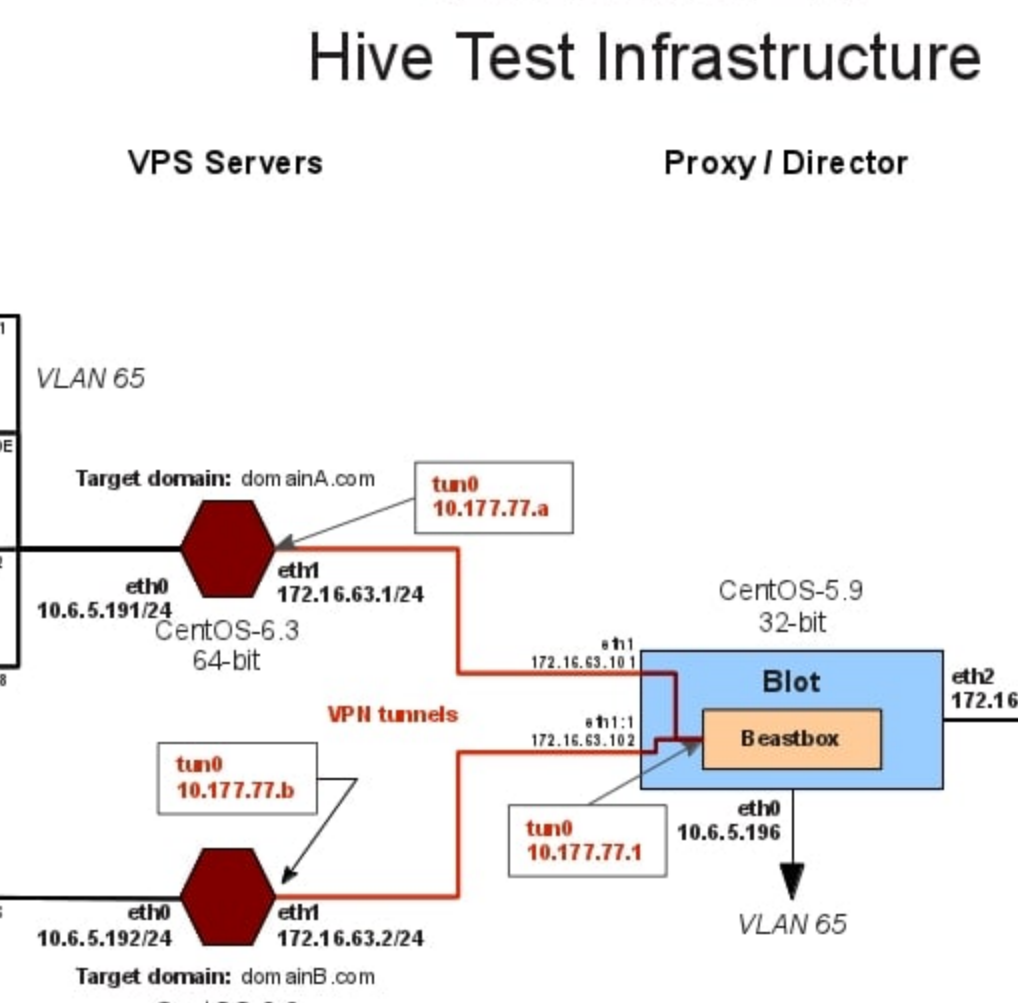
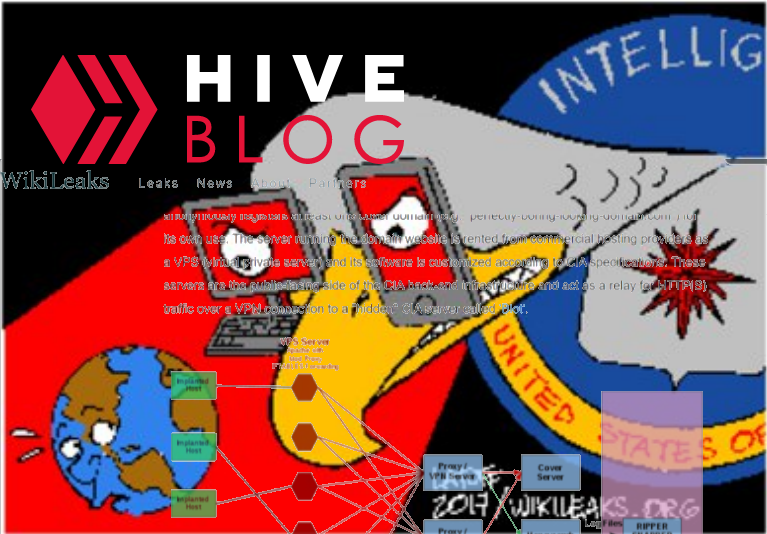
HIVE is a back-end infrastructure malware with a public-facing HTTPS interface which is used by CIA implants to transfer exfiltrated information from target machines to the CIA and to receive commands from its operators to execute specific tasks on the targets. HIVE is used across multiple malware implants and CIA operations. The public HTTPS interface utilizes unsuspicious-looking cover domains to hide its presence.
Anti-Virus companies and forensic experts have noticed that some possible state-actor malware used such kind of back-end infrastructure by analyzing the communication behaviour of these specific implants, but were unable to attribute the back-end (and therefore the implant itself) to operations run by the CIA. In a recent blog post by Symantec, that was able to attribute the "Longhorn" activities to the CIA based on the Vault 7, such back-end infrastructure is described:
For C&C servers, Longhorn typically configures a specific domain and IP address combination per target. The domains appear to be registered by the attackers; however they use privacy services to hide their real identity. The IP addresses are typically owned by legitimate companies offering virtual private server (VPS) or webhosting services. The malware communicates with C&C servers over HTTPS using a custom underlying cryptographic protocol to protect communications from identification.
The documents from this publication might further enable anti-malware researchers and forensic experts to analyse this kind of communication between malware implants and back-end servers used in previous illegal activities.
A stupid question, if you assume this shit belongs to the CIA, why do you use it? I understand some things - but that does not seem so logical to me.