Got a spam comment today from @drhoofman, seems like his account has been compromised, thought he just hadn't been active for a while but looks like some of his powered down hive was sent to another account (not tagging, but it's wwefun) that has similar transfers in from other accounts. Here's a pic of the account's recent history:
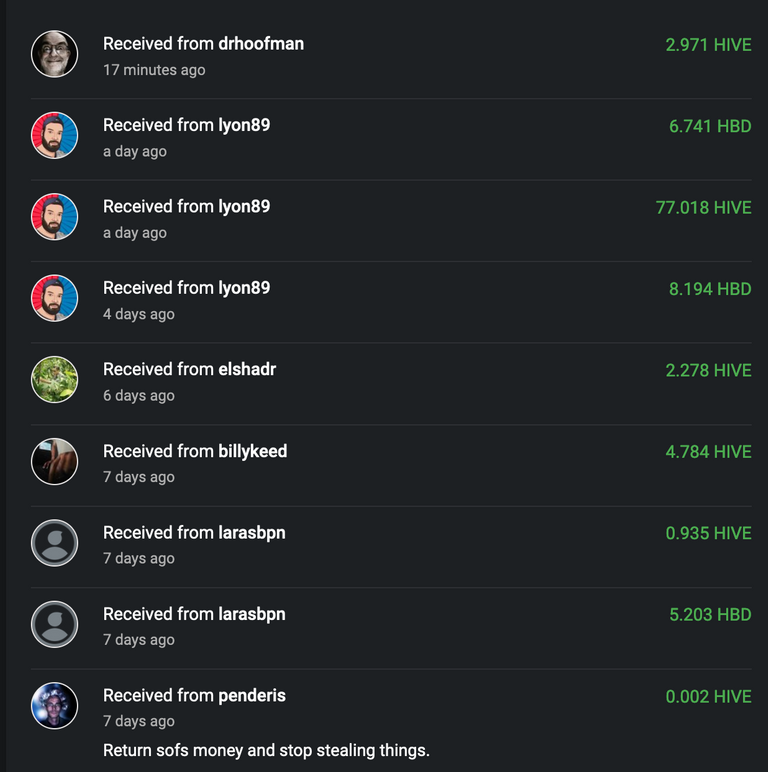
And based on how the URL in the spam comment looks, haven't clicked since I'm honestly not sure if there's a safe way to do so, it's some sort of phishing that probably convinces you to sign a tx or put in a key to "vote for LeoFinance's witness" (I know they're not behind it, using them as the bait is what made it seem fishy in the first place). Guessing @penderis might know a bit about it if you can share, kinda surprised I hadn't seen any posts about it yet.
Early edit: looks like the account that wwefun is moving the hive to is probithive, has 55k in there plus HBD and savings.
Heads up for those spam links though, check URLs & https before you sign anything, don't put keys into websites if you can avoid it. Anyone who can contact people who've been compromised (hoofman's account is already drained unluckily) should do so if they can to try to recover.
Been a minute since I've posted & been trying to get a real post together, but I was close to clicking the link & want to make sure word gets out about it. Tagging into leofinance so this pops up there as well.
Second Edit, did some more digging on the links & sites, copied from reply below, CHECK YOUR URLS & DO A GUT CHECK PEOPLE :
Huh this is kind of interesting, thanks for commenting! Was in a meeting for a bit but decided to check out the link myself, see if I could figure it out. Opened in a private window in brave, because I don't use brave but I still have some extensions on there and the private window turns them off. Not sure if it hits keychain, going to check in a second, but otherwise it seems pretty clear, first off you've got this comment at the top of the website, just interesting to me:
Mirrored from leofinance-steem.web.app/ by HTTrack Website Copier/3.x [XR&CO'2014], Wed, 07 Jul 2021 13:38:19 GMT
- not sure the date is accurate unless they've been updating it, but the tool is just a regular utility to download a website for offline use.
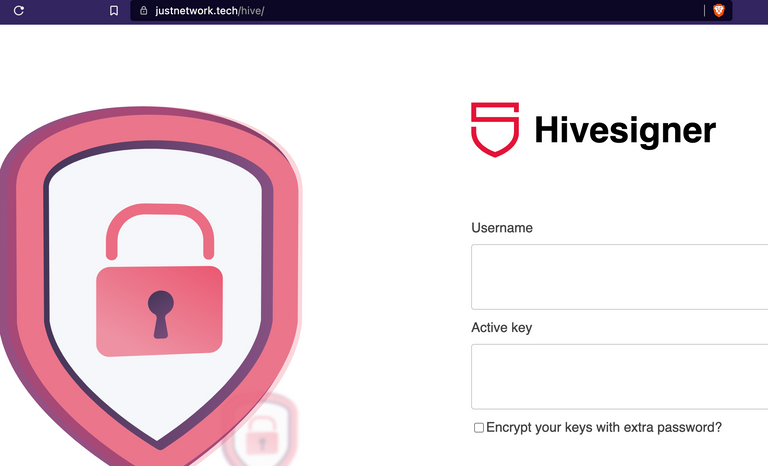
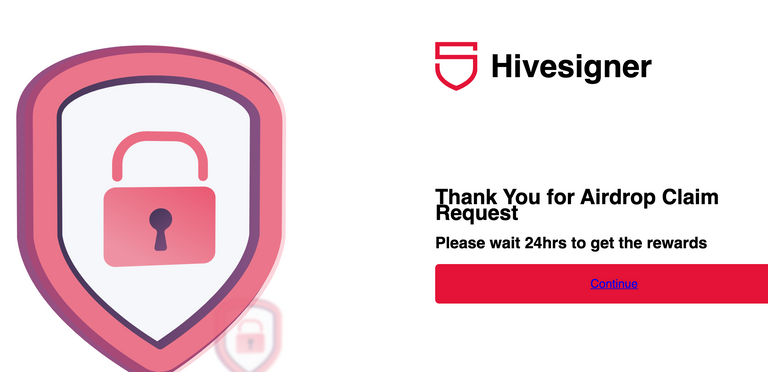
Then you have this, after the big "get 300 hive now for voting", a vote now button that leads to a very off looking version of hivesigner - not copied in the same way, not gonna link it directly but it's host: justnetwork dot tech (at root path, there's a steemconnect clone too actually), path: /hive. After entering literally anything since they don't validate the text input, sends the form data in a post to insert.php. The first site looks like a firebase hosting instance maybe, while the second is probably a full php server, don't know php so know less about that. After checking to make sure it wasn't gonna blindside me, checked in my normal browser and it didn't open up keychain, so they're definitely going after active keys. Luckily, that means if you catch it fast enough, you should be able to recover, just have to get to it before they get to your wallet. And once again, gotta check your URLs & https, & do a gut check on the site, that weird zoom (I didn't change it) should be at least a yellow flag.
Sorry for dumping this in a reply, started typing it out and got through more than I expected, gonna edit this into OP too, I've gotta get back to work though, hopefully this info can help someone out. Wasn't able to find any info on the domains used, both have privacy protection on. May also be able to spam their API/endpoints & break something, but idk if that's technically legal, nor do I really know how unless just running while(true) {fetch(...)} would work.
Did not dig too much but from the account that reported it to me it is a phishing /attack which will make you authorize transfers some people are caught off guard by keychain requests and don't read what is being requested. Did not seem like they were adding further permissions to the account so not super necessary to change keys if using keychain but like said did not dig since she already was changing keys etc. Not sure if blacklist api listed the people who made those comments but hopefully that still a default on most intorfaces so people know not to interact with those accounts.
Huh this is kind of interesting, thanks for commenting! Was in a meeting for a bit but decided to check out the link myself, see if I could figure it out. Opened in a private window in brave, because I don't use brave but I still have some extensions on there and the private window turns them off. Not sure if it hits keychain, going to check in a second, but otherwise it seems pretty clear, first off you've got this comment at the top of the website, just interesting to me:
Mirrored from leofinance-steem.web.app/ by HTTrack Website Copier/3.x [XR&CO'2014], Wed, 07 Jul 2021 13:38:19 GMTThen you have this, after the big "get 300 hive now for voting", a vote now button that leads to a very off looking version of hivesigner - not copied in the same way, not gonna link it directly but it's host: justnetwork dot tech (at root path, there's a steemconnect clone too actually), path: /hive. After entering literally anything since they don't validate the text input, sends the form data in a post to insert.php. The first site looks like a firebase hosting instance maybe, while the second is probably a full php server, don't know php so know less about that. After checking to make sure it wasn't gonna blindside me, checked in my normal browser and it didn't open up keychain, so they're definitely going after active keys. Luckily, that means if you catch it fast enough, you should be able to recover, just have to get to it before they get to your wallet. And once again, gotta check your URLs & https, & do a gut check on the site, that weird zoom (I didn't change it) should be at least a yellow flag.
Sorry for dumping this in a reply, started typing it out and got through more than I expected, gonna edit this into OP too, I've gotta get back to work though, hopefully this info can help someone out. Wasn't able to find any info on the domains used, both have privacy protection on. May also be able to spam their API/endpoints & break something, but idk if that's technically legal, nor do I really know how unless just running
while(true) {fetch(...)}would work.Then guess it good she reset her keys, I will have a look at the link myself seems interesting but off the top my head I think at some point you still doing the approval and in that signature and URL should always be the actual transaction info? if putting keys into that site direct though definitely can see them storing it, why not, and since ecency does not give new users their keys and just lets them use their master that is also pretty scary since mainly I think they will get hit with odd "login" "approval" behaviour and just submit without thinking. I will give it a look to understand the flow better myself. As was initially explained to me it seemed a simple oh look there is a popup thingy from an unknown domain.
Congratulations @petertag! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
Your next target is to reach 15000 upvotes.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPCheck out the last post from @hivebuzz: