Beam is a cryptocurrency that allows its users authority of privacy while maintaining its value. Beam is built with amazing features on the blockchain which makes up the advantages beam offers.
Features of Beam
• Private and secure
Beam is built in with protocols that enables users have decision as to what information is made public so users have a 100% control over their data information.
• Scalable and fast
Using the blockchain beam crates a smaller block different from other blockchain which make it less cumbersome and make transaction processing faster and easily scalable.
The Challenge
The blockchain has been a pace setting for the revolutionalization of major industries today as it transcends from digital finance for example bitcoin and the rest, to data computing, technology, medical science, banking e.t.c. with this evolution we have seen new innovations we never deemed possible and there are many yet still to come.
But bitcion which can be said to be a success is several aspects has failed to meet the standard of perfection when it come to privatizing transfer of asset and information IIn peer-to-peer transactions. The blockchain which has been proven to be a very secure platform on which most cryptocurrency run has also been proven to be so transparent that their can hardly be any secret or privacy so long it resides on the blockchain. this has led Users and industry who seek this form of confidentiality to go elsewhere looking for where their needs can be met.
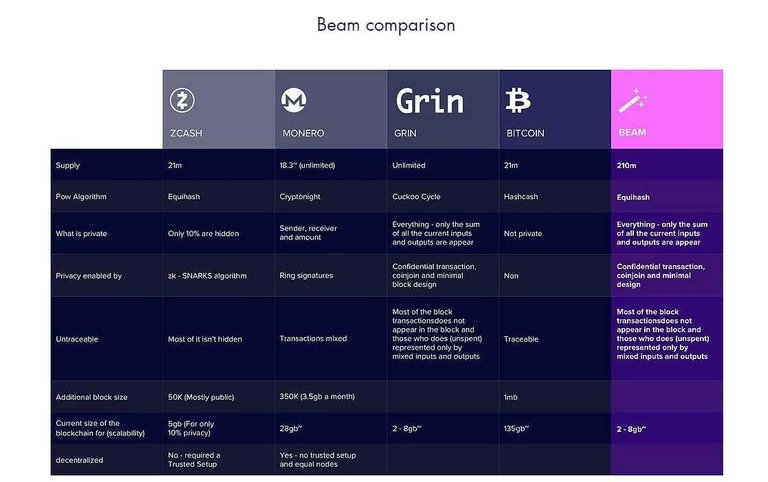
BEAM
Beam offers real time solution to this pressing needs as it is built to offer true anonymity on peer-to-peer transactions.
Beam can be said to be the most confidential cryptocurrency when it comes to privatizing and concealing information transfer form one person to another. It is also scalable and reliable. Beam is built using the Mimblewimble protocol which is a adaptation of a spell from the famous "Harry potter movie". The Mumblewimble protocol has to concepts which was created by Greg Maxwell which are the ** Confidential Transactions and the Cut-Through transactions.
Confidential Transactions
Confidential transactions is a cryptographic commiitment scheme that also has tow basic concepts which are the (I)binding and (ii)hiding. The binding stage is more like an acredition stage that doesn't disclose the information but verifies the authenticity of the information without giving access. The hididng stage ultimately conceals the information except the key which is held by the user is given to the third party only then can the have access to it and also to changing the key to one only known to the user.
cut- through transactions
A block in a block chain is a large list of transactions and can be thought of as one large transaction to be “cut through” (combining all the transactions in between A-Z). Applying this principle even further from individual blocks to the entire blockchain creates a system that only needs the current state of transactions instead of the entire history of all transactions as they occurred (which is how Bitcoin works).
With this system, unspent transactions outputs (a transaction received by a user which has persisted in the blockchain) can be proved to belong to the receiving user via the value of the message and the value of the blinding factor. After creating the transaction, only the commitment is recorded on the blockchain; not the addresses of the users or the amounts exchanged.
Cutting down the amount of data required to store and verify transaction data allows Mimblewimble to work with smaller blocks!
More in depth information about the protocol as it relates specifically to r values, range proofs and other technicalities can be reviewed in the Mimblewimble WhitePaper and in the Beam Position Paper.
Privacy
The role privacy plays In storing cryptocurrency value cannot be over emphasized as it is pertinent that some sensitive information and asset/transaction informations are kept private in other not to attract hackers. Some large organizations make use of cryptocurrency to store investment or fund micro investments and at such they require some form of privacy to carry out these transactions also not all information should be available publicly. Some corporate cypto financial firms in order to adequately satisfy their clientele needs a levels of privacy as to which clients information is made public and also some clients have a need to be quiet about some form of monastery transactions they process through the firm.
Use Case
Beatrice runs a cryptocurrency asset management firm and she is having issues as her investors are requesting anonymity as regards their identity being available or traced back to them through the blockchain. Which can be understood as most of her investors are prominent men with global recognition. Beatrice is given an ultimatum to look for a medium when their identity and funding can be anonymous to public eye. as she research she finds out about beam and is super excited as it's a win for her, her firm and her investors. Everyone is happy.
Use case 2
Deji hold several crypto tokens which he has acquired for himself by working hardand others he also has invested in. Rumor has it he's now a millionaire and hacking are looking for means to trace and track his funds. Deji is on the run as he looks for ways to code his transaction records and also privatize his information from the public eye in other not to loose any. A friend introduces him to beam and Deji is excited and can now take a breather.
Summary
Beam is confidential, scalable and fast. It gives users control over who they share information with and whom they give access to. with a linear blockchain it makes it possible for swift transaction processing and also enhances scalability. It has the ability of thing multiple transaction into one thereby hiding transaction value and is also comparable with different froms of transactions including escrow. Beam solve and brings answers to several questions on the blockchain.
beam2018