Brutal force is used by hackers to penetrate or block a system.
There are two main options with brutal force : DDOS or Password Cracking.
Zombies and Botnets
To understand Brutal force you need to understand what are zombies and botnets.
Before beeing able to perform brutal force attacks, you need to accumulate calculation power and/or ip adresses.
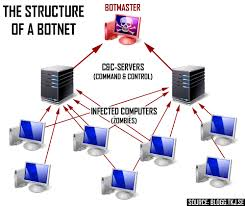
So the first goal of a hacker is acquiring zombies, a zombie is a captured machine he can control.
To get control of a zombie he needs to deposit a tool on it, often done using Trojan horses. The trojan horse is a malware installed via, for example, an infected program "offered" (downloaded by the owner) to the owner of the machine.
Once installed, it remains dormant, until the hacker considers he has enough zombies to activate them all at same time, creating by this the botnet.
DDoS
Distributed Denial of Service
When the hacker activates his botnet, he forces them to contact a specific ip address, for example log into steemit.
Problem, many servers are not configured to accept that many incoming trafic at once, making it crash or at least beeing unrachable for legit users.
Load balancing is one of the ways to fight DDoS, as it spreads the trafic to several available servers.
Password hacking
When the hacker activates his botnet, he shares an enormous password list, randomly generated and including some of the most often used passwords. Each zombie receives a part of the list.
Making the cracking task much easier, remember a computer is able to perform millions and millions of operation per second, you can imagine when a whole network is concentrated on the same task.
Some of the ways to fight this, is to force delays between errors, limiting to three attemps before requesting another password to unlock ( like your puk on your cellphone) or even using a second password, like the sms you receive on your cellphone (2FA)...
Hope you liked this ;)
Cya later
 We do not forgive, We do not forget, Expect us.
We do not forgive, We do not forget, Expect us.