- What is an Information Security Assurance?
The of guaranteeing information and managing risks associated with its use, processing, storage, and transmission is known as information assurance.

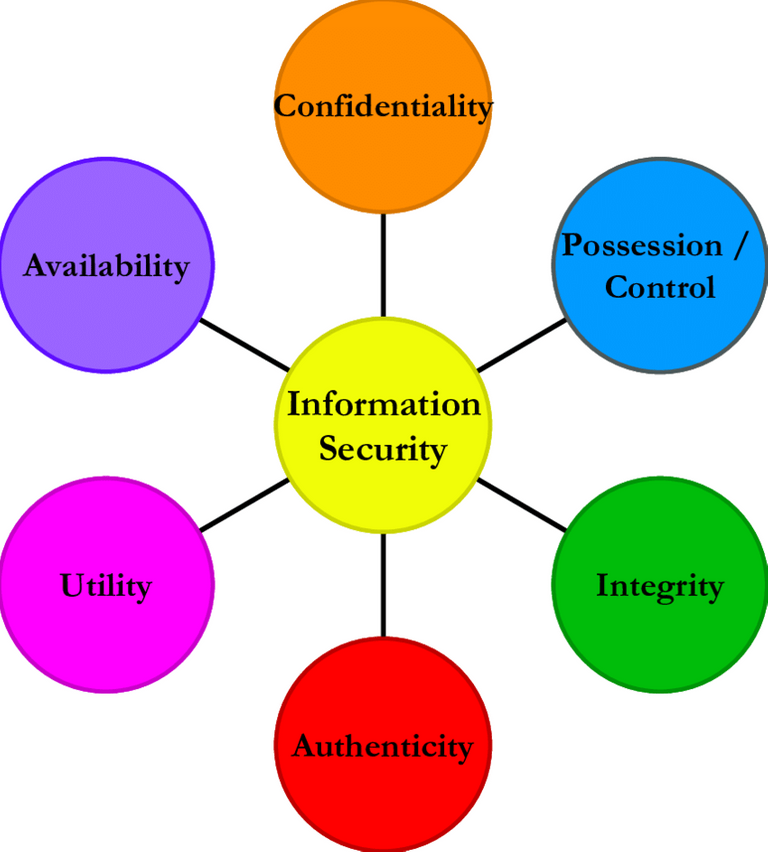
- Components Information Security Assurance?
The Five Components of Information Security Assurance
- Integrity
- Availability
- Authenticity
- Confidentiality
- utility
- Possession/control
- Differentiate the certification programs to Common body language?
This 'Body Language' course is meant to help you understand the various aspects of body language so that you may use the information to your advantage both personally and professionally. Where you can understand the range of nonverbal behaviors that comprise 'body language', the nuances of handshakes and touch, ,how your personal style influences your body language, match body language to words, know how to read facial expressions, interpret common gestures, eye contact and understand the differences in body language across cultures .

Differentiate the Governance and Risk management?
Governance is the system of rules, restrictions, policies, and resolutions put in place to prescribe a behavior is referred to as governance. Risk Management is the process of identifying, assessing, and controlling threats to an organization's capital and profitability is known as risk management.Different between Security Architecture to Design?
A security system's security architecture is the set of resources and components that enable it to function. The approaches and procedures that place those hardware and software parts to promote security are referred to as security design.

- Different between Business Continuity Planning to D-i-s-a-s-t-e-r Recovery Planning?
Business continuity consists of a plan of action. It ensures that regular business will continue even during a disaster. Disaster recovery is a subset of business continuity planning - What is Physical Security Control?
Personnel, hardware, software, networks, and data are all protected from physical security control and events that could result in serious loss or damage to an organization, agency, or institution.

- What is Operations Security?
Operational security (OPSEC) is a risk management and security process that keeps sensitive data out of the wrong hands.

- What is Law?
Law is the discipline and profession concerned with a community's conventions, practices, and rules of behavior that the community recognizes as binding.

- What is Investigation?
Investigation is the act of examining or researching something or someone in a formal or systematic manner. - What is Ethics?
Ethics is based on well-founded moral norms that dictate what humans should do, usually in terms of rights, obligations, societal advantages, justice, or special qualities. - What is Information Security?
Information security refers to a set of procedures for protecting personal information against unauthorized access and alteration while it is being stored or sent from one location to another.
