So, earlier today, I was alerted to an active phishing campaign targeting Steemit users by the wonderful @mars9 in this post. I might be currently on my holidays, but people like me who work in computer security never really take a fucking break.
Now, in their post, they redacted some details. I don't do redaction. So I decided, despite it being my holiday, to do some quick and dirty investigation of this phishing campaign. Outlined below is what happened. This post will be screenshot heavy, as it is kind of a visual walkthrough of how I did a quick investigation of this whole thing.

The "Deceptive Comment"
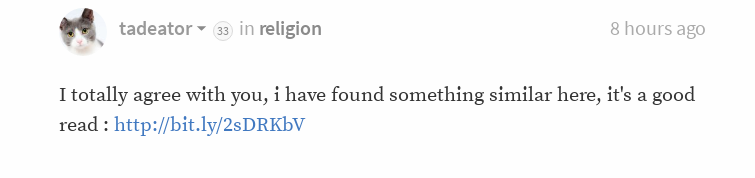
So, from mars9's posting, I quickly located the deceptive comment in question, which I have added a screenshot of below. As you can see, it contains a bit.ly link, which is our first point of investigation.
Analytics Pages are Useful.
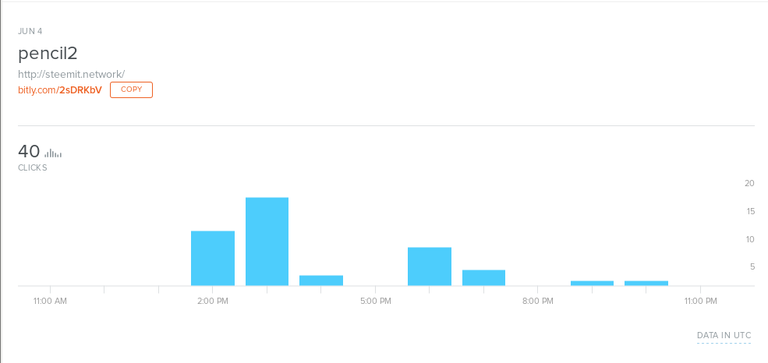
So, a bit.ly link. There is a neat trick where we can check its analytics by appending a "+" to the end of the URL, so we do that... At this time, the link has had 40 "clicks".
Following the Phish...
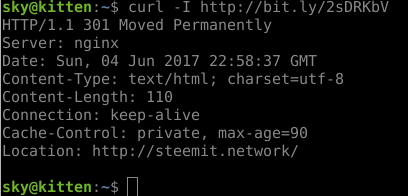
Our next trick, is using the command line utility "curl" to request the bit.ly link and see where it is taking us. For now, I don't want to hit the phishing URL in a browser at all.
Further Down the Rabbit Hole...
So, we are being redirected to something called "steemit.network". This seems like a good lead, lets follow this trail onward... By opening it in the Tor Browser for safety. I did not want to open this in a browser with any active login sessions as a precaution!
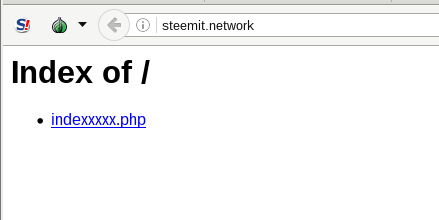
So, we see it is a... Open directory with one link, to an "indexxxxx.php" script. Lets click it!
The Phishing Page
I really, really regret not grabbing the HTML source of the page while I had the chance. You will see why this is not possible in a few minutes ;)
The page is pretty clever - it mimics the Steemit interface pretty well, and people are used to having to login again when their session times out. Quite evil, really!
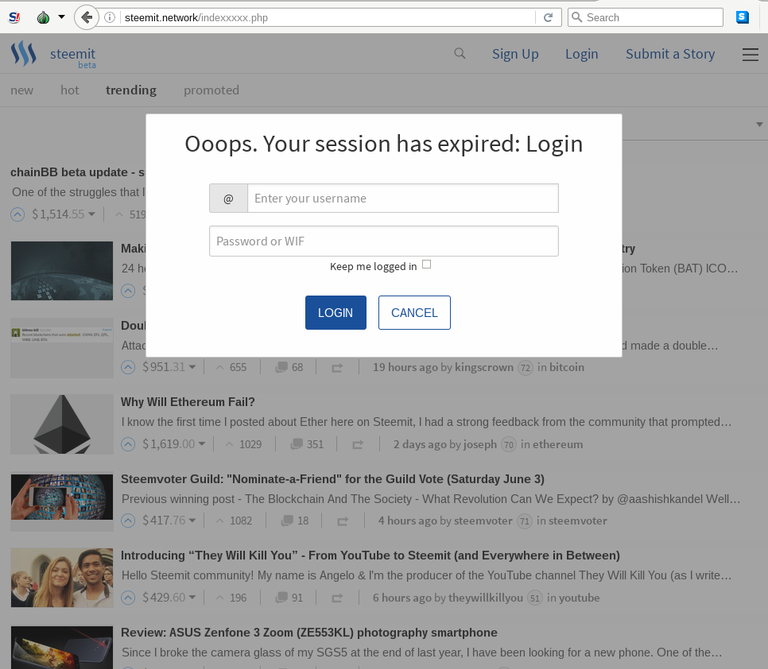
The DNS Story
So I decided the logical next step would be to use the PassiveTotal service to dig up Whois data and other DNS data on this threat actor. The following screenshots tell that story.
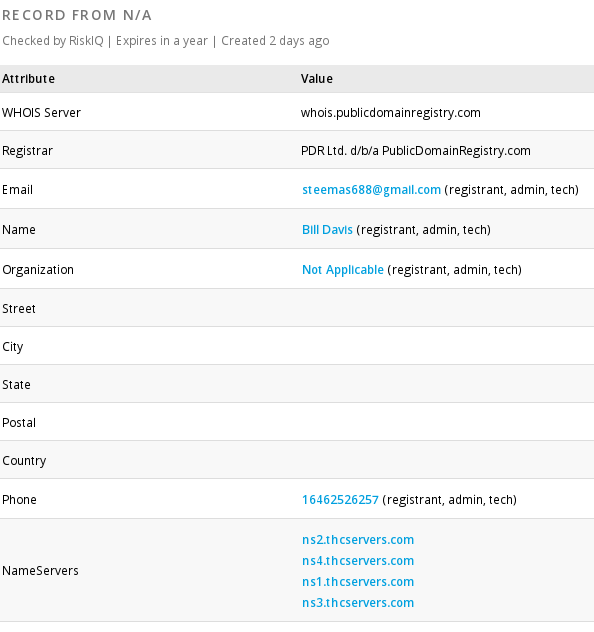
And here we have OSINT data of "places this link/site was posted to"... It seems our phishing person was quite active.
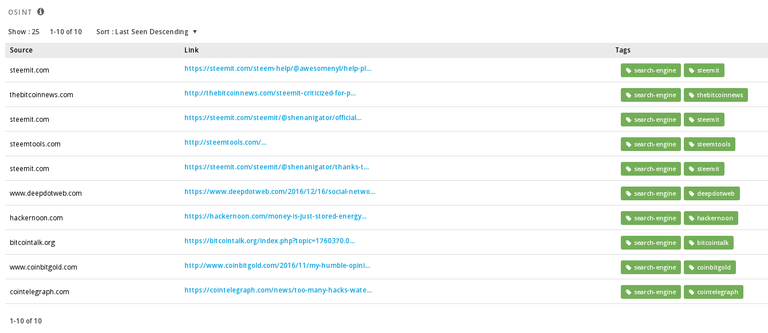
We also were able to determine that the phishing page was hosted on THC-Servers. So...
The Happy Ending
I quickly got in touch with the THC-Servers abuse team. They responded incredibly quickly and terminated the site and its user, eradicating the threat. A happy ending for all involved!
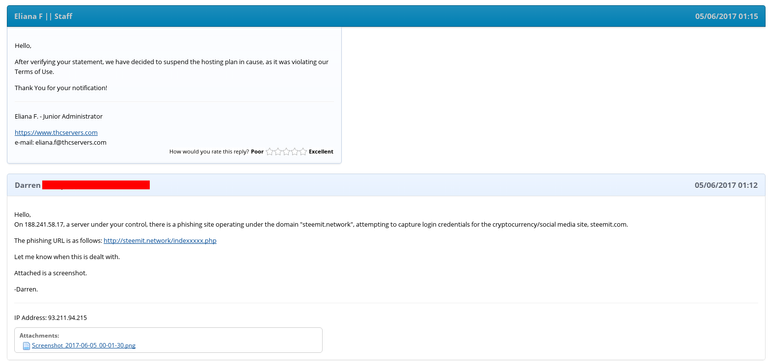
Lessons Learned
Fucking asshole criminals are targeting Steem users. Be vigilant, be wary, and if you see anything, feel free to drop me a line or tip me off and I will look into it. Also, THC-Servers are very good at responding to abuse complaints!
Thanks man. Can never be too careful on ANY platform nowadays. Fist rule of thumb: Do not EVER click on links that look fishy. a bit.ly link? Um, nooo.
Using TOR was a good idea! You're bringing me back to a few years ago where I was working on computers everyday. Actually a lot of fun. I'm glad you are helping bring this information to the community.
You can always use tools like GetLinkInfo to know where the link is redirecting you, there are some userscripts too but if you are in paranoid mode (which is the correct mode to be) I don't recommend it to you if you don't know javascript.
@synapse ... having been hacked before and coins stolen https://steemit.com/steemit/@bitrocker2020/i-got-hacked
I am glad to know that you've taken your time and efforts to hunt down these bastards who thru their cunning and technical knowledge tries steal precious coins from innocent people. Great work and fantastic sharing buddy. up, re & fo ... hope to hear more from you . @bitrocker2020
It's despicable. There is nothing that gets under my skin more than hackers who are trying to steal from innocent people.
Hi brother thanks a lot to you
On protection and distinctive explanation
Really thank you brother...
Wow, you certainly know all the tools, thanks for the heads up about Steemit phishing. STEEM has a quite high value now so naturally it would become a target.It's great that it was caught early. Law enforcement should be set upon the perp.
Resteemed, very useful.
the site is down, you did a great job
You have good post my friend. Best one.
This my introduce.
https://steemit.com/introduceyourself/@joe28/steemit-is-my-palace-hi-steemians-lets-read-this-one
so I gotta ask, did you call him from a pay phone?
I was tempted to phone the number, but no pay phones out in the place I currently am. Might give the number a call from the airport tomorrow though...
you think that's his real name?
I really doubt the name is real. I might email the email address though. The phone is likely bogus, but could be hilarious to try calling anyway :)
please do post what happens when you call!
Great post, we are always learning, thanks for sharing with the comunity! <3
resteemed
It is good to know there are people in the know on here. People who don't can get tricked and lose. Thanks, upvoted ,followed,and resteemed
Congratulations @synapse! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honnor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPBy upvoting this notification, you can help all Steemit users. Learn how here!
This is really fascinating. I didn't know about the bit.ly + trick, so that was new to me. Thank you for continuing to protect Steem!