Top of the day to everyone in this great community. Today I want to talk a little bit about internet security. Well, it is not usually everyone's favorite topic, we usually care about our internet connectivity but care less about how secured such connections actually are. As far as the modem is connected to the internet or so long the internet service provider connection is intact, we assume there's virtually no problem, moreover, what could go wrong besides loosing connection to the internet?
[Credit: Pixabay. CC0 creative commons license. Author: TheDigitalArtist]
Though I will talk briefly about VPNs, the major focus of this work is the internet protocol security (IPsec).
So what is VPN? Well, I'm struggling to explain the concept without using professional terms. To understand what a VPN really is, one has to first understand what is a private network. A private network is a network connecting only a set of people or a set of groups. Such networks are not meant to be accessed by anyone outside these boundaries. Examples of private networks include, a local area network, a connection to file sharing server within an organization, a hotspot setup for information transfer between to computers, etc. Hence, virtual private network is a connection type which allows private network connections within public networks.
Hence, VPN allows you to remotely and safely connect to that your private network in your organization or office through a public network like the internet. VPN connections are usually in the form of point to point or point to multipoint. The point to point connection allows, just like the name implies, a connection between just two devices or network hosts while the point to multipoint allows connection between one device and many other device, like a server and its clients.
))
VPN connectivity. Credit: credit: wikimedia. Creative Commons Attribution-Share Alike 4.0 International, 3.0 Unported, 2.5 Generic, 2.0 Generic and 1.0 Generic license. Author: Ludovic.ferre]
Traditionally, the only available VPNs are the point-to-point VPNs which are also referred to as Layer three (L3) VPNs. Layer three in the sense that the VPN has routing functionalities, i.e, VPNs that are aware of networks other than its local network. The good part is that devices connected to such VPNs are not aware of the network complexities, hence, only the networking equipment like the routers and Layer three (L3) switches take care of such VPNs. The problem of such VPNs (layer three VPN) is that it does not support a form of communication called Broadcast communication. Broadcasts are used by devices to locate other devices within a network and can only travel within a network.
Another form of VPN is the Layer two (L2) VPN which does not support routing. Devices connected using such VPN, though they may be millions of miles away, see their connections as within the same locality. Hence, addressing schemes such as the private IP addresses which are not allowed within the internet can be used such connectivity. A more robust form of VPN which combines the capability of both L3VPN and L2VPN is the multiprotocol switching.
A very popular multiprotocol switching is the Multiprotocol Label Switching (MPLS) which is neither a Layer two VPN nor a Layer 3 VPN, rather it is in between the two. Within the MPLS network (i.e, before traffic reaches its destination) IP addresses are not used to transmit data rather a label is used which performs the job of IP addressing even faster.
IPsec
IPsec consists of sets of interactive protocols which provide security for private communications across internet protocol networks. To private communications, IPsec provides services such as:
Confidentiality
One of the first notification we receive after installing Whatsapp in our phones is a message assuring us our chats are private and secured due to end-to-end encryption. End-to-end encryption does not mean that our traffic can not be hijacked or intercepted in transit, but when such occurs, data obtained from such actions are useless and meaningless because the information is scrambled before transmission. Scrambling in this respect means encryption.
[Credit: Wikimedia. Creative Commons Attribution 3.0 Unported license. Author: Ford Prefect]
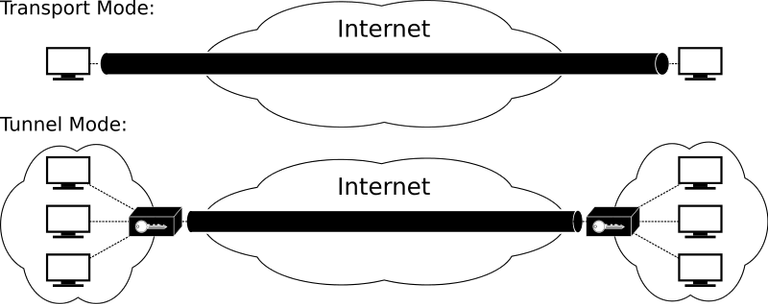
Encryption by IPsec is done in two modes, which are Tunnel mode and Transport mode. The tunnel mode uses a key (set of characters) to encrypt the actual data being transmitted and its header. A header contains the information necessary to identify and direct data. IPsec is used in tunnel mode if the destination of the IP packet is not the same with as the termination point of the IPsec services. In a general term, IPsec is used in tunnel mode when the IP traffic being protected by the IPsec is not generated by the device configured for the IPsec.
Transport mode encryption is used in encrypting just the data in a packet and not the whole IP packet. This type of encryption is mostly applied when IPsec is setup between host to host or a host and its gateway.
Integrity
Data usually are not sent from a sender to a receiver as a lump rather they're divided in packets. Take for instance, when we're traveling and we ain't traveling light, we could label our luggage in the order like 1of 4, 2 of 4, 3 of 4 and 4 of 4. This shows that our luggage is actually 1 but it is divided into 4 and can be reassembled using the order of numbering. With such numbering, when any of the luggage is compromised, it could easily be noticed.
Same happens in data networks, and IPsec utilizes such operation. Data integrity ensures that data is not modified or totally altered on transit. This is done by allowing network equipment of host perform a form of calculation at the transmitting end and also perform similar calculation at the receiving end. The result of such calculation is called a Checksum value or a Hash.
Checksums or hashes are not transmitted along with the packet, rather, they are calculated at both ends and the results are compared. A matched result shows the integrity of the data was not compromised while a mismatch in calculation result shows the data has been modified and necessary measures will be initiated such as dropping the packet or requesting for a new one.
Authentication
When we work in corporate environments, we wear tags or ID cards. These tags or cards answers a certain question by default. This question is, Who are you?
))
[An IPsec authentication header. Credit: Wikimedia CC4.0 license. Author: Buyanjargal123]
Same with authentication, authentication asks the user the question, who are you?, while the user responds with a password (I know there are digital ID cards, yes, but IPsec only understands passwords for its authentication. Authentication is carried out by computing a form of cryptographic hashed message code from an entered password and the authentication is carried out on every field of internet protocol. When authentication is carried out, the result is stored in an authentication header (AH) and can be referenced by any questioning device or protocol.
Anti-replay
Hackers are very intelligent set of people. Take for instance, a camera situated just above an ATM machine, a hacker can have access to the pins ATM users just by having access to the CCTV camera near the ATM machine.
Not exactly but similar similar scenario is prevented by IPsec using the antireplay operation. When an attacker gets hold of a packet containing a successful login to an account (this captured packet may be encrypted), they can have access to the account by replaying such packets.
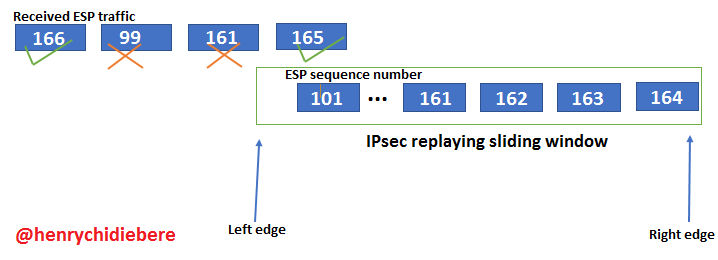
[packets with already accessed sequence number are droped. Image designed using MS word and windows paint.]
IPsec prevents antireplay of IP packets by ensuring there is no duplicate packet per session. This is done by assigning each packet a sequence number which is unique. By so doing, any packet arriving with an already assigned sequence number is discarded as a rogue packet.
Working principle of the IPsec
The main purpose of IPsec is to secure an IP packet as it is transmitted through an unsafe or open network, like the internet. To do this, IPsec sets up a tunnel which passes only IP traffic marked as "interesting" traffic. Setting up and tearing down this tunnel summarizes IPsec operation and occurs in five steps:
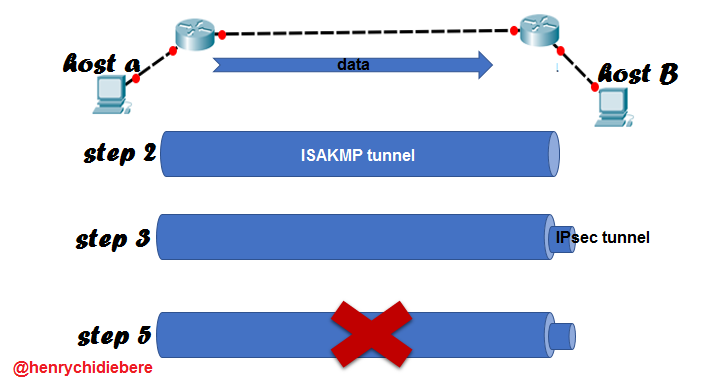
[Steps for setting up IPsec tunnel. Designed by me using Cisco packet tracer, MS word and Windows paint]
In explaining what IPsec is, I mentioned that it is a set or collection of protocols, one of such protocols is the internet key exchange (IKE). It is used to set up security associations (SA). These associations provides information used to setup a tunnel such as the type of encryption used or the type of hashing used. Security Associations are identified using two (2), 8-byte security parameter index which is transmitted by each peer wanting to initiate the IKE exchange.
Step 1: The interesting traffic
Consider two devices that desires to initiate an IPsec tunnel, the first step a network device would take is to examine the traffic being transmitted. If the traffic is marked as an interesting traffic, the traffic is put into an IPsec tunnel. In order to map a traffic as interesting traffic, a policy is first set indicating which IP addresses to match.
The policy is usually in the form of access-lists. An access-list is a list describing how an IP address or IPV6 address would be treated as it travel into or out of a network. Usually there is a condition stating if the traffic would be dropped or allowed to pass. Once an access list is created, it is combined with a policy mapping and applied to the interface of interest. This is how a network equipment identifies if an IP is eligible to be created a secured tunnel for. If it is eligible, the second step is carried out.
Step 2: IKE Phase 1
Once a traffic is marked as interesting traffic, the two network devices sets up a tunnel called IKE phase 1 tunnel or ISAKMP (Internet Security Association and Key Management Protocol) tunnel. The ISAKMP is used by the two end network devices in negotiating the necessary security parameters needed to setup the IKE phase 1 tunnel.
When a matching key has been exchanged, this helps in the creation of the second tunnel in step 3. Setting up the ISAKMP tunnel can come in two modes which are main mode and aggressive mode. In the main mode, the peers that will transmit packets through the IKE phase two exchanges three parameter. The first parameter is the agreed algorithm for data encryption and hashes. The second parameter is the exchange of generated secret key while the last exchange is responsible for the verification of peer identity on the other side of the tunnel.
There are few information exchanged in the aggressive mode and even the remaining exchange are made to occur in a very fast sequence. One downside of the aggressive mode is that it is vulnerable to attack since authentication information is shared even before the tunnel is setup but as already stated, this mode is very fast.
Step 3: IKE Phase 2
A second tunnel is setup under the protection of the ISAKMP tunnel setup as described above. This second tunnel built inside the first tunnel is called IPsec tunnel. It is also known as the cone of silence and it is within this cone of silence that data is transmitted securely between peers.
Step 4: Data transmission
Just as the name suggest, the traffic of interest is allowed to be transmitted within the already created tunnel (the IPsec tunnel). Packets that are transmitted are encrypted from the sender’s end and decrypted from the receiver’s end. These encryptions and decryptions are done using the negotiated security associations created by the internet key exchange (IKE).
Step 5: Tunnel tear down
During the setup process, many parameters will be set determining how the tunnel will be used. These parameters could be time, amount of data, etc. When a tunnel is setup based on time, when the said time times out, the tunnel will be terminated or when the tunnel is set up stating that a particular amount of data is allowed to pass, when such threshold is reached, the tunnel will be terminated.
Summary
Sometimes there might be need to have access to private network resources remotely, such resource could be office file sharing server, access to home internet of things network, or we could desire special dedicated connection between two very important individual sharing highly classified information, in such situations, IPsec VPN is here to help. The operations of IPsec is very detailed and is applicable in real environment.
REFERENCES
- Introduction to IP Security (IPSec) -Cisco
- Introduction to IPSec VPN -hillstonenet
- Basics of IPsec -rapid7
- Virtual private network -Wikipedia
- Server virtualization -Softwareadvisory
If you write STEM (Science, Technology, Engineering, and Mathematics) related posts, consider joining #steemSTEM on steemit chat or discord here. If you are from Nigeria, you may want to include the #stemng tag in your post. You can visit this blog by @stemng for more details. You can also check this blog post by @steemstem here and this guidelines here for help on how to be a member of @steemstem. Please also check this blog post from @steemstem on proper use of images devoid of copyright issues here.


I hold this close to my heart, living in a country where I basically need it on 24/7, but even then, they're basically banned and many of them have to concede and share all the data traffic with the regime in order to continue functioning!
Thankfully the one I use at least claims to have a way around it... Didn't even consider how complicated they can be as this post demonstrates...
For IPV4, the IPsec functionality is optional but with IPV6 it's not optional. Hence my hope is high. Thanks for your time @mobbs
Yeah, in China, that is the only way to access a lot of things :)