Hello everyone and welcome to yet another interesting work aimed at making us appreciate the internet and communications better.
I'll be talking about TCP and UDP and some IT guys among us might have heard about these abbreviations or might have had an encounter with them (personally, lol). Well, TCP is a protocol of the internet, sorry I always bring in the word "protocol" whenever I discus about the internet but, my sincerest apologies, but the internet is controlled by protocols. Just like the name implies, they're rules guiding the operations of the internet. The internet is already complex with these rules and standards, can you imagine how complex it would be without protocols and standards?
[Image credit: Creative commons images. A CC BY-SA 3.0 license. Author: Nick Youngson]
The truth is, we all have used TCP and UDP. For the fact that you're currently reading this work means that TCP is alive in your system! This is because both the secured hypertext transfer protocol (HTTPS) and normal hypertext transfer protocol used in surfing the web are both TCP protocols. Whenever you run an FTP (File Transfer Protocol), be you at the server end or at the client end, you're using UDP protocol. Whenever you pick up your voice over IP telephone in your office to call your secretary, appreciate UDP cause it just saved you some stress.
Who or what are these guys? I would like to start with TCP.
TCP is the protocol of the internet and to fully understand TCP we need to make reference to the general internet classification. This classification and specification is known as the Open System Interconnect (OSI) model. OSI model consists of 7 layers and I have made a post focusing on only OSI model feel free to check out here, hence, I will only summarize the model from layer 7 down to 4 which is our layer of interest.
OSI model is a move by ISO (International Organization for Standard) to simplify and enhance interoperability of internet equipment. The first layer (starting from the top) Application Layer. The application layer is the closest to the user and interacts with application software to deliver the necessary user communication and also system resource management (not network resources). The next is the Presentation layer which performs the function of ensuring that data is formatted appropriately as it enters into the system and as it leaves the system.
))
[OSI model protocol data unit (PDU), left and OSI model, right. Image credit: Wikimedia CC3.0 license. Author: Gorivero]
The third layer is the Session layer. Speaking to you without having your attention is almost useless. Hence, session layer ensures that communicating systems have each other's attention before communication can begin. Finally (our layer of interest) the Transport layer. Though every other layer is as important, this layer is tasked with how data would get to its destination. It necessarily won't do the transporting per se, that is the job of the layer below it, the network layer (Routing). On a very clear term, the transport layer is concerned with how data is "posted" and how it is "delivered".
For computer networks, there are two transport layer protocols and they are TCP and UDP. For pure telephony, we have Real-time Transport Protocol (RTP) but that is not in the scope of our today's discussion.
Transmission Control Protocol (TCP)
I have programmed myself to replace "TCP" with "reliability". Yeah, they can be used interchangeably. TCP ensures data is transmitted and delivered reliably. If there's an environment that is hungry for reliable information exchange, that environment must be the internet and as stated earlier, both HTTP and HTTPS makes use of the TCP.
Computer treats data differently, sometimes this is necessary for security reasons. Most data transfer make use of some sort of check sequences and once this check fails, the whole data is useless. Loosing one data packet which might be as small as a byte will likely render the whole data useless. When downloading movie using a Torrent client, you're able to play the movie with many hitches in an uncompleted mode because media servers in our devices makes its data calculations differently. Hence, when downloading a non media file, even at 99.99%, that file would still be unusable until download is accomplished.
))
[Credit: Wikimedia. Creative commons license. Author: liftarn]
What enables TCP to ensure data is transmitted reliably is Acknowledgments. TCP creates a kind of connection with receiving device, hence it is called connection oriented protocol. TCP initiates remote connection in a process known as three way handshake. Once connection has been initiated, TCP ensures no data is lost through what is called windowing.
Sounds quite interesting right? Yeah, but that comes with a price. TCP header contains so many information making the header very heavy. The fields in the header enables it to carry out data transmission reliably.
The TCP header
The TCP header is both TCP advantage and also its disadvantage. As already stated, the header contains both the data being transmitted and also the control information. The minimum size of a TCP header is 20 bytes (or 5 words) while the maximum size is 60 bytes (or 15 words). I will only explain all the fields available in the TCP header since all the header in the TCP are contained in the UDP and even more. Consider a TCP header shown below, let's get to know the field better.

[Image credit: Wikimedia. A creative commons license. Author: Ere]
The TCP header contains 10 fields with the first row containing the source and destination port field. I guess we all have seen a port number. A port number is used together with an IP address to form a socket. A very popular port number is the HTTP port number which is port 80. Any web request made from a client to a web server must do so using the port 80 or 8080. The source and destination port contains the number of the communication endpoints for both the sending device and the receiving device. The source and destination port field are 2 bytes each.
The second and third row is the Sequence and Acknowledgment number field respectively. I will explain them both in detail in the next heading, however, both numbers are used for reliable data transmission and error correction. They're both 4 bytes each.
On the forth row, we have the data offset, reserved and windows size field. The data offset field is used to save the size of the header and this is done in the multiple of four bytes. As already stated, the size of the header can vary between 5 words to 15 words (60 bytes). When a data is being transmitted with the parameter of this field not provided, the minimum header (20 bytes) size is automatically inserted and used as the data offset for the header.
The reserved field always have the value of 0 and has the function of ensuring that the whole TCP header size is aligned and is in the multiple of 4 bytes, this helps in ensuring the efficiency of data transfer.
The control flag field contains 7 flag bits which are the SYN (synchronize), CWR, URG (urgent), ACK (acknowledge), RST (reset), PSH (push) and FIN (finish) flag bits. The SYN flag bits are used to point out which packet that just participated in a successful handshake (I will explain this shortly). The CWR flag bit is used in conjunction with the ECE flag bit for notifying and resolving cases of congestion. The ACK flag bit is used for validating the successful reception of a transmitted packet. The URG flag bit is used for indicating QoS (quality of service) and indicating which packet needs to be transmitted urgently, this bit is not frequently used in today’s network.
The RST flag bit is used to reset the whole TCP operation and this is only used in the case of serious error during data transmission. The FIN flag bit is used to indicate the end of data transmission and the packets involved in this operation. Finally, the PSH flag bit is used to indicate unsaturated packets which deserves prompt delivery.
The window size field is used to ascertain the amount of data a receiver is capable of processing before accepting further transmission. The checksum field carries the result of calculations carried out by the sending party, this helps the receiver to detect if the data it received has been corrupted. The Urgent field is always not considered in recent data networks.
Also the options field contains complex algorithms used in acknowledging some sort of data transmissions which are very rare. Finally, the padding field is used complete the size of the header in cases where its size is below the minimum.
TCP Connection and Windowing
TCP is a connection oriented protocol. To do this, it makes use of both the SYN and ACK bits of its header. The process of setting up this connection is known as the three way handshake this is because three contacts made by both the sending end and the receiving end. Take for instance, data needs to be transmitted between two computers using the TCP. Computer A which is the transmitter first transmits a packet with the SYN flag bit set, once computer B receives the packet, it automatically knows that the computer at the other end wants to transmit some data, hence it responds with an acknowledgement packet (ACK).
[Connection setup in real network. Image credit: Wikimedia. Creative commons license. Author: Fleshgrinder]
When this packet reaches computer A, it does not just start sending the desired data, it first acknowledges the acknowledgement it just received. Hence, computer A also sends another packet, this time, with its ACK flag bit set. Once computer B receives it, it knows that data transmission has started. This process is known as the three way handshake of the TCP.
Windowing
When we copy files, maybe from a flash drive to our computer or from computer to computer using a simple network cable connection or from our computer to an external hard drive, we notice that the speed of transfer will either spike at the beginning or very slow at the beginning. This makes the computer sometimes set some crazy timing during file transfer, hence you see your computer writing "4 hours remaining" but will later complete the transfer within 20 mins.
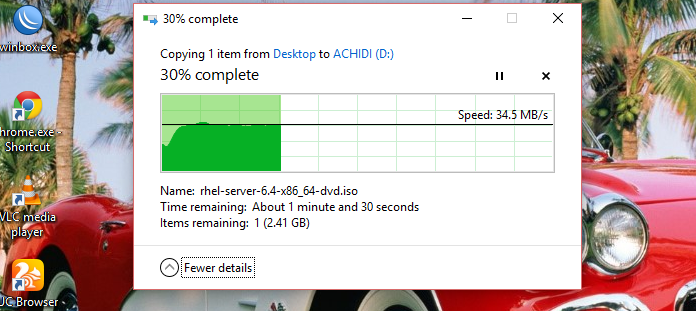
A screenshot of file transfer from my desktop to my external hdd. Notice the initial slow start and subsequent constant speed.
This is what windowing is all about. It ensures that the receiving device is not overwhelmed with data. This is where Sequence Number I stated earlier comes into play. The packet to be transmitted is assigned sequence number and this is used to regulate the rate of data transfer. Continuing with our example above, after the computers have exchanged handshake, remember, the sending computer was the last to send an ACK packet, it also goes ahead to transmit the first packet. lets say we want to transmit 12 packets, let the numbers represent the packets.
Illustration carried out using Cisco packet tracer Icons, MS word and Windows Paint
When computer A transmits packet 1, it waits for computer B to send ACK 2, which means that it received the first packet and is ready for the next packet. Computer A then on reception of the ACK2 from the remote device, it goes ahead to transmit packet 2 and 3 and pause for acknowledgment. If computer B is still capable of receiving both packets, it responds with ACK 4. Computer A then transmits packet 4, 5, 6 and 7 (exponentially). If computer B is not capable of handling 4 packets at a time, it will respond with ACK 7, which means re-transmit packet 7. This time, Computer A will reduce the amount of packet it transmits to computer B.
It is obvious that computer B can only handle 3 packets at a time, hence, its window size is 3. Got this? At this point, the transmission will constantly be at three packets per transfer and we see our transmission progress with a steady speed till the whole process is complete. This process is known as windowing.
UDP
User Datagram Protocol is a connectionless protocol and carries out data transfer unreliably. Why in this world will I carry out any transmission unreliably? Well, take for instance you're talking on the phone with your buddy and after 4 minutes, something he said in the first minute shows up, do you think you can accurately process it? Even if you can, I bet you wouldn't appreciate that, you would rather let the past be in the past right?
That is real time! Once voice channel is open for communication, whatever goes in or out is not checked for validity. There are some measures used to check the delays in voice transmission (Jitters) but nothing can be done about what is already transmitted or what is already received.
Hence, UDP is mainly deployed in voice transmission, in conjunction with the Real-time Transport Protocol (RTP) which is built on UDP to make the transmission tolerate more loss. The header of UDP is shown below.

[Image credit: Wikimedia. A creative commons license. Author: Ere
It has just a size of 8 bytes making is a very light protocol.
REFERENCES
- Transmission control protocol -intronetworks
- User datagram Protocol -intronetworks
- Transmission control protocol -wikipedia
- TCP and UDP headers -lifewire
If you write STEM (Science, Technology, Engineering, and Mathematics) related posts, consider joining #steemSTEM on steemit chat or discord here. If you are from Nigeria, you may want to include the #stemng tag in your post. You can visit this blog by @stemng for more details. You can also check this blog post by @steemstem here and this guidelines here for help on how to be a member of @steemstem. Please also check this blog post from @steemstem on proper use of images devoid of copyright issues here.




You made ur intentions..... I was already thinking of going to do a professional course on computing not possible........ I like the context of your article
I need and explain of the quote below
Are u saying as humans of our device used for reading
Yes we all have used the two protocols. You just made a comment, that comment was made using http which is a transmission control protocol and I guess you've made a call since yesterday, if so, you've made use of udp. Thanks
That is cool
Beautiful one here. I smell a Cisco certified personnel with great quality..You've written excellently well. Kudos bro!
Also working on a post regarding networking protocols.
Thank you bro. I'll always be very happy to see networking posts. Looking forward to seeing your posts
You the boss bro, went through your blog, it's more than just interesting..Good posts on there
I just learnt a lil of Networking (CCNA) coupled with a bit I learnt in school...I hail you professionals oooo
Now I know why my 99% downloaded files won't open. Although some media files from some particular websites don't play if it ain't 100% too.
Nicely written post
Thank you man. What I explained is the general form of operation of TCP and UDP some environments can tweak the header for some reasons but the tweaking must be within acceptable limit else the packet would be dropped. Also the way a computer program handles a packet it receives differs.
Thanks for the apt response
Some do open though. But the explanation here goes a long way.
The difference between user datagram protocol and transmission control protocol is the reliability like you stated. If you trust your network for to transmit data fast without interruption then udp is a good choice. But in the case of tcp, the complexity makes it slow because it checks if the data was transmitted successful. The transport layer is much intelligent than the network layer. Nice workdone. You killed it bro!
I beg to differ. TCP is not slow but compared to UDP, can accommodate more data per packet. But you have a good understanding of the concept. Thanks for stopping by.
am not generally saying that TCP is slow, but comparing between both, TCP is slow. because of its duties when handling packets. when comparing the fastest, UDP is faster because it handle errors.. In addition, TCP deals with segments or tcp package its data as segments.
Even with my growing career in IT, I haven't gotten grip of all these modules & their implications. This is quite a lift to my learning....
Nicely written..
Happy I could add to your knowledge. Thanks buddy.
You're welcomed... Keep steeming!
Hi @henrychidiebere!
Your post was upvoted by utopian.io in cooperation with steemstem - supporting knowledge, innovation and technological advancement on the Steem Blockchain.
Contribute to Open Source with utopian.io
Learn how to contribute on our website and join the new open source economy.
Want to chat? Join the Utopian Community on Discord https://discord.gg/h52nFrV