![]()
I did a search and saw this has been talked about here in the past, even as far back as a year ago, but it is morphing, or to use the more specific term, polymorphing. As the snippet shows below from MS-ISAC, this was just put out by MS-ISAC in July of this year and it is still running rampant because its not easily contained by signature based antivirus solutions. See snippet below and then I will go on...
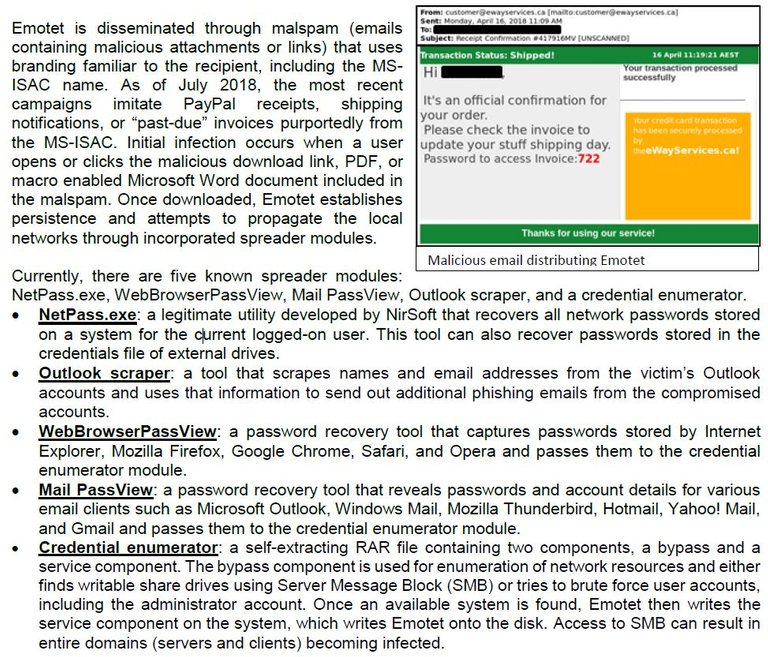
Source: MS-ISAC - July 2018 bulletin snippet authorized for free distribution
This virus is taking advantage of machines that have administrative privileges especially and you can see the component breakdown in it, as shown above. It's quite the nasty worm to have on your personal PC, or even worse, your workplace domain. It is even scraping and decrypting saved passwords in the popular browsers and uploading them to its central hub. It parks itself in hidden names with keepalives to revive itself for when it gets discovered to come back. It puts itself on available network shares. As you can also see from the snippet above, they are trying the malspam methods, and it is working. People with PayPal accounts are falling for this, left and right. People are opening PDF and DOC or DOCX files without fear or clicking on links without a care in the world, except to make themselves right by the email they received.
Some of the better virus and malware scanners out there are detecting this in emails, and simply discarding the messages rather than even bothering quarantining them. Some of them are getting right through though because of their encrypted nature, or appearance as a harmless message from somewhere like PayPal. The downside of this discard is that the message is just lost and might have been a false positive. There is too much of it going around right now though to analyze quarantines.
After I first started hearing about this one last week, I thought it was new. My web research showed me at least 3 or 4 steemit posts about it, but the most recent one was months ago. This is an active issue right now and it doesn't seem like many are talking about it.
Are any of you other IT professionals dealing with this? What are you doing to mitigate it? Obviously, taking administrative rights away from user's desktops can hinder it's progression. What are you doing to prevent it or quarantine it and stop it in its tracks? Has anyone done anything with firewall rules or ACL's that seem to limit its capabilities or stop it altogether, at least at the routing level? I am guessing at layer 2, this will just run like crazy unless there is some good detection agent that will shut it down.
I follow you
Plz check my post
https://steemit.com/steem/@amitahl15/improve-the-safety-of-cryptocurrency-f683424b47006
Thanks for following me. I'm glad you find my content worth reading.