hello guys!!!
today i,ll tell you about five dangerous hacking attacks so let's begin.
and please don't forget to follow me and like my post.
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks
A denial-of-service attack overwhelms a system’s resources so that it cannot respond to service requests. A DDoS attack is also an attack on system’s resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker.
Unlike attacks that are designed to enable the attacker to gain or increase access, denial-of-service doesn’t provide direct benefits for attackers. For some of them, it’s enough to have the satisfaction of service denial. However, if the attacked resource belongs to a business competitor, then the benefit to the attacker may be real enough. Another purpose of a DoS attack can be to take a system offline so that a different kind of attack can be launched. One common example is session hijacking, which I’ll describe later.
There are different types of DoS and DDoS attacks; the most common are TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack and botnets.
.jpg)
- Phishing and phishing attacks
Phishing attack is the process of sending emails that appear to be from trusted sources with the goal of gaining personal information or influencing users to do something but usually don't belong to a genuine source. It combines social engineering and technical tricks for influencing victims. It could involve an attachment to an email that loads malware onto your computer. It could also be a link to an illegitimate website that can trick you into downloading malware or handing over your personal information.
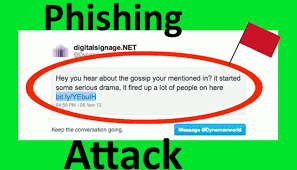
To reduce the risk of being phished, you can use these techniques:
=> Critical thinking — Do not accept that an email is the real deal just because you’re busy or stressed or you have 150 other unread messages in your inbox. Stop for a minute and analyze the email.
=> Hovering over the links — Move your mouse over the link, but do not click it! Just let your mouse cursor h over over the link and see where would actually take you. Apply critical thinking to decipher the URL.
=> Analyzing email headers — Email headers define how an email got to your address. The “Reply-to” and “Return-Path” parameters should lead to the same domain as is stated in the email.
3.Password attack
Because passwords are the most commonly used mechanism to authenticate users to an information system, obtaining passwords is a common and effective attack approach and used in our daily life. Access to a person’s password can be obtained by looking around the person’s desk, ‘‘sniffing’’ the connection to the network to acquire unencrypted passwords, using social engineering, gaining access to a password database or outright guessing. if an unauthorised person gains access to your passwords he can gain access to your social media accounts etc. The last approach can be done in either a random or systematic manner:

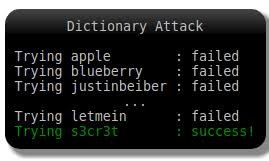
=>In a dictionary attack, a dictionary of common passwords is used to attempt to gain access to a user’s computer and network. One approach is to copy an encrypted file that contains the passwords, apply the same encryption to a dictionary of commonly used passwords, and compare the results.in this process,a file with common usable passwords are made and implemented to break up the passwords.Commonly used software for this is air crack ng.
In order to protect yourself from dictionary or brute-force attacks, you need to implement an account lockout policy that will lock the account after a few invalid password attempts and try to maintain a difficult password.
.
=>Brute-force password guessing means using a random approach by trying different passwords and hoping that one work Some logic can be applied by trying passwords related to the person’s name, job title, hobbies or similar items.Many apps are available on google playstore for brute forcing wifi passwords like wpa/wps tester.

so please guys comment and tell me how do you like my article and tell should i make more articles and blogs about hacking.
thank you.