https://www.mintpressnews.com/displacing-wikileaks-is-securedrop-a-government-leak-graveyard/238339/
. . . . . . . . . . . . . . . . . . . . . Tor’s Connections to the US Government. . . . . . . . . . . . . . . . . . . . .

Recently new doubts have been raised regarding – not necessarily the credibility of SecureDrop – but the Tor project upon which SecureDrop is based. Winter told MintPress News that Tor, like SecureDrop, has a “reputation problem” because it was initially funded by the U.S. Naval Research Laboratory, but that the project’s past was no reason for concern. However, while conducting researching for his recently released book Surveillance Valley, investigative journalist Yasha Levine found that the U.S. government’s involvement in the Tor project continues well into the present with truly unsettling consequences.
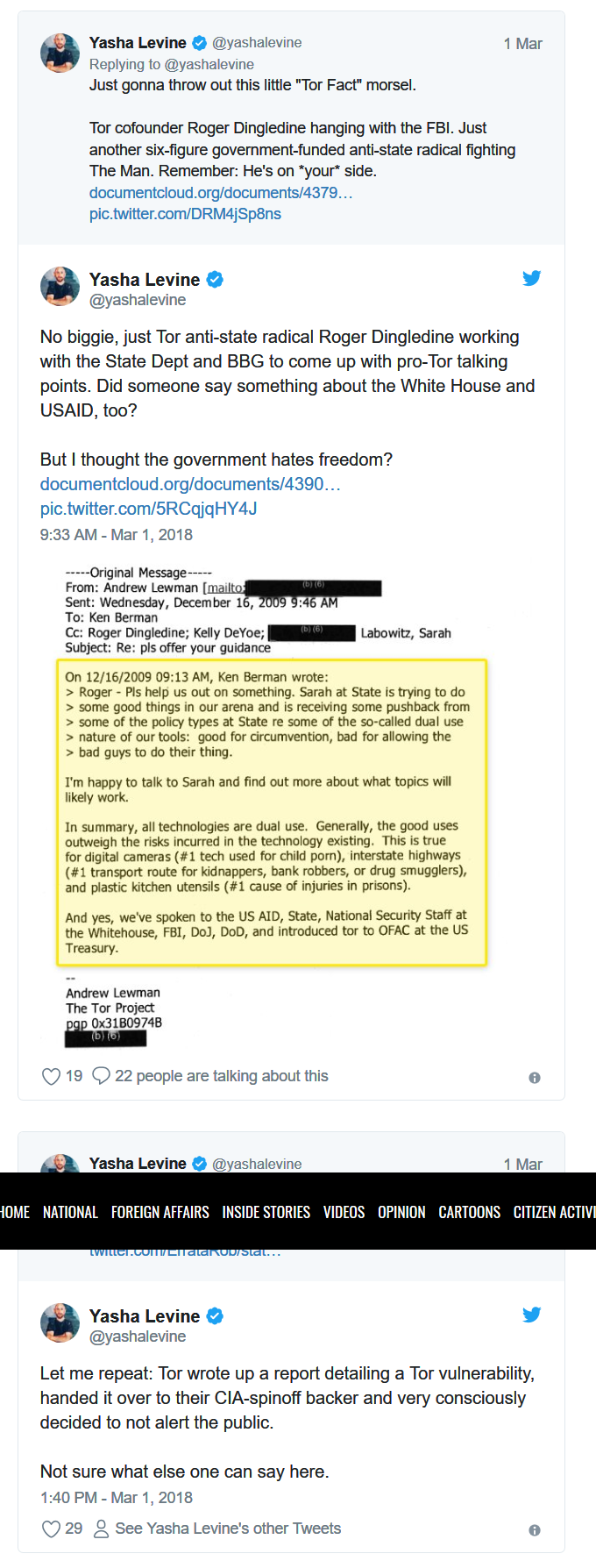
Levine recently detailed new, troubling information about the Tor project which he obtained after combing through thousands of pages of documents he received through FOIA (Freedom of Information Act) requests. The documents detail communications between Tor and the CIA spin-off the Broadcasting Board of Governors (BBG), which provides the project with much of its funding.
Levine had previously revealed that Tor was a U.S. military contractor with its own government contractor number, effectively making it an extension of the very apparatus that it claims to protect its users from. Indeed, Tor has long been promoted as the only means of protecting oneself from NSA intrusion online. Yet, Tor’s funding is the least of the problems it poses to the online security of its users.
For instance, the FOIA documents, which have recently been released to the public, reveal that Tor privately “tipped off” the federal government when finding security vulnerabilities well before the public was made aware of them – giving the government plenty of time to exploit the flaws to their benefit. One of those vulnerabilities “made Tor traffic stand out from all the rest and made it easy to fingerprint and single out people who were using Tor from the background data noise of the internet.” That vulnerability was known to the government in 2007 but was not made known to the public by 2011, over four years later.
Another troubling finding in the releases are documents detailing Tor co-founder Roger Dingledine’s work with USAID, the Department of Defense, the FBI, the Department of Justice, the National Security staff at the White House and other government agencies to come up with “pro-Tor talking points.” This type of communication between government agencies and the top echelon of Tor employees and promoters suggests a potentially sinister level of cooperation that undermines Tor’s ostensible commitment to keeping its users anonymous.
Such concerns are also heightened by the fact that Tor’s “exit nodes,” where traffic leaves the secure “onion” protocol and is decrypted, can be established by anyone, including government agencies – likely making Tor’s anonymity feature ineffective given Tor’s on-going cooperation with the government. Indeed, as Tor researcher turned hacker Dan Egerstad revealed in 2007, governments have been funding high bandwidth Tor exit nodes for just that purpose.
These new revelations about Tor have taken many by surprise, including WikiLeaks and Assange who had previously promoted the project. However, Assange recently tweeted a link to the FOIA request database compiled by Levine, suggesting that his promotion of the online tool is a thing of the past.
The implications of Tor’s vulnerabilities and cooperation with the government have startling implications for whistleblowers and SecureDrop users. Much of the SecureDrops’ security is based on Tor. If Tor is cooperating with the government and if the government is, therefore, able to surveil Tor users, government agencies could easily identify a source attempting to remain anonymous when sending leaked documents via SecureDrop to a news outlet.
This is likely already happening. As FBI whistleblower Sibel Edmonds told MintPress News in an earlier interview, former NSA employees had relayed to her the federal government’s interest in seeking out potential whistleblower communications from the internet. Though Edmonds was not aware of the technical means in which that was accomplished, Levine’s research points to Tor as a likely culprit.
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
http://www.jewworldorder.org/displacing-wikileaks-and-intercepting-whistleblowers-securedrops-security-problem/
Disclaimer: I am just a bot trying to be helpful.