
This article was published by myself with Disobedient Media in December 2017. It is my own intellectual property.
New Zealand Internet Party leader Suzie Dawson and this author have continued to analyze Snowden Files that have so far never received public scrutiny. Disobedient Media previously reported on findings stemming from Batch Three of the Intercept's Snowden File archives. Dawson and this author have analyzed over 100 documents from the Intercept's Batch Four of the Snowden Files to date, and have noted numerous items of key significance revealed in the never-before-publicized data. The collaboration, under the title DecipherYou, will continue until some time in early 2018. A selected group of our findings is presented here, with the rest of Batch Four findings to be discussed at a later date.
One of the first documents in batch Four discussed the NSA's definition of Denial and Deception. The document advertises a seminar which would be presented by Dr. Larry Gershwin, the National Intelligence Officer for Intelligence Assurance and Chairman of the Foreign Denial and Deception Committee (FDDC). The description of Gershwin's presentation reads in part:
Dawson noted that while the definition of 'denial' was marked secret, the description of 'deception' was marked unclassified.
Another finding of interest from episode 10 of DecipherYou was in regards to the definition of the 'Office of Target Pursuit." The Snowden File read in part:"After completing a 6-month tour in a TOPI, interns choose two additional tours from other S2 target offices, the Target Analysis Center, Cryptologic and Exploitation Services SIGDEV elements (including the Office of Target Pursuit and the Network Analysis Center)." With the help of a viewer, we were able to find definitions in regard to the initial file in a Wikileaks pdf document.
The document states that Special Source operations oversees the PRISM program, one of the most infamous examples of mass surveillance revealed by the publication of the Snowden Files. The Washington Post and other outlets have reported extensively on PRISM. The Verge describes the program: "PRISM is a tool used by the US National Security Agency (NSA) to collect private electronic data belonging to users of major internet services like Gmail, Facebook, Outlook, and others. It’s the latest evolution of the US government’s post-9/11 electronic surveillance efforts, which began under President Bush with the Patriot Act, and expanded to include the Foreign Intelligence Surveillance Act (FISA) enacted in 2006 and 2007."
While PRISM is a relatively recent development, Special Source Operations are decades older.
Another document revealed that the US does indeed intervene militarily in order to secure the flow of oil to the US and its allies. The admission was made in a file relating to a seminar on "African Petro-Politics." The document reads in part: "By 2015, the United States will depend on West African oil for 25% of its oil imports... Oil production in Sudan has been a factor in the Sudanese civil war, with oil wealth sharing being a primary negotiating issue in the peace process. Oil has played a role in the extent of corruption and in sustaining military might in several African countries... Finally, threats to - and security of - the oil producing areas in West Africa will be discussed (including U.S. engagement to improve security)."
This afterthought in the description of a Petro-Politics seminar is particularly relevant in light of the recent deaths of US Service members in African countries. News of their deaths struck a chord of dismay in much of the American public, who were largely caught off guard at the news that the US was active in African nations. Reuters noted in October this year that US deaths in Niger highlighted "Military Mission Creep" in the continent, writing: "[the deaths] shine a light on Washington’s increasingly aggressive Special Forces-led counter-terrorism strategy in Africa and its risk of casualties." The Washington Post described the incident as indicative of a "Shadow War."
The influence of oil and concerns surrounding the security of the flow of oil in the decision-making process behind such missions are often left out of such reports, but are nakedly and outright stated in the NSA documents. The concept of War-for-Oil is not new, with legacy press outlets including CNN readily reporting the admission of military leaders that the Iraq War was based on securing oil interests. The NSA's admission that conflicts are entered into in order to benefit oil flow in plain words adds corroboration to such admissions which were at one time dismissed as speculation.
Another significant document covered in this author's collaboration in the DecipherYou stream was that the NSA routinely outsourced Network security, and that the NSA showed very little concern for defensive security measures to protect their data. Concern for catastrophic security breaches is not shown in the hundreds of documents Dawson has analyzed thus far, dating up to late 2004. Dawson discussed the way in which improper data breaches by foreign states, terrorist organizations, or other entities should have been a major concern of the NSA.
This notable lack of concern with security and potential security breaches was especially ominous, Dawson explained, given the increased number of people who were given access to sensitive material thanks to the NSA's use of corporate outsourcing. She said " transferring data across corporate networks... as they expand the pool of who can receive data, all of that has security implications, so they are opening more and more and more breach points,... proprietary networks .. and it's impossible to secure it if they are using corporate parties and having to go through their support channels, it's insane." Dawson stated that the NSA might have assumed that their systems were essentially bulletproof, adding: "If Hewlett-Packard types are responsible for network security, God help the NSA."
Dawson added that even denial and deception documents did not address network-wide compromises, leaks, or breaches from another state. However, some documents illustrate preparation for disaster recovery in case of real-world disasters like hurricanes, tornadoes, and the like. It should be noted that disaster recovery is totally separate to network security and that the presence of one variety of preparedness only serves to highlight the utter lack of regard for the other.
The only reference to such concern was mentioned in the discussion of the fact that if a breach occurred, Congress was to be notified. While the NSA appears to have largely ignored network security, multiple documents Dawson analyzed described offensive hacking tactics. In light of the numerous breaches in security that have taken place over the years since these documents were penned, one hopes that a concern for data security has manifested since 2004.
Dawson remarked that many of the NSA documents emphasized 'Executive Accessibility,' while simultaneously, executives were shown to employ an 'amnesiac approach to their role. She used the example of Snowden's attempt to raise constitutional issues resulting from mass surveillance as an example of the type of dangerous self-policing groupthink that can occur in environments that extoll the virtues of executive accessibility but also punish those who bring up serious questions. Dawson said: The function of corporatism is to create a veneer of executive accessibility, but to discourage employees asking hard questions."
An additional Snowden file Interview titled "Interview with Jim Cusick, SID/Assistant Deputy Director for Data Acquisition," provided insight into the mindset of the leaders operating within the NSA in concert with figures like Michael Hayden. Cusick states in the interview: "I let it be known to NSA leadership that I was willing to take on virtually any task as long as it was in the middle of the fray, it was challenging, and it made a difference... Being a Senior Operations Officer in NSOC has to rank as the best job in SIGINT by orders of magnitude... Heading up Unconventional Operations and managing NSA's largest budget category was the hardest and most demanding job I ever took on. Representing Lt Gen Hayden at the Pentagon during the aftermath of 9/11 and Operation Iraqi Freedom was fascinating and added a whole new perspective on support to the warfighter and national-tactical integration."
Additional documentation regarding Cusick's role at the NSA reveals that: "James M. Cusick, Assistant Deputy Director of the NSA for data acquisition... He’s Mr. Data Acquisition. He’s the specialist in charge of building collection systems that can acquire vast amounts of data, and his unit is the one that is running this program... To the best of my knowledge, in the five years in which the program has been running, it has not caught a single person."
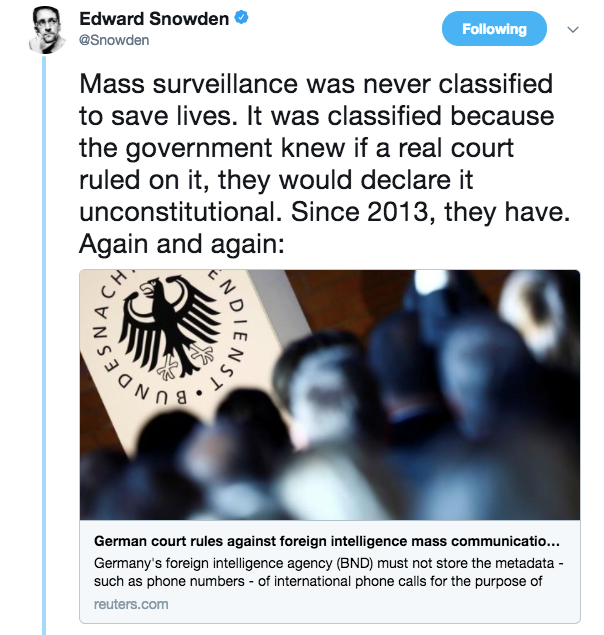
That Cusick described his values in NSA documents as willing to participate in virtually anything so long as the task "Was in the middle of the fray, it was challenging, and it made a difference" is concerning given his participation in the illegal mass surveillance of American citizens that has reportedly not delivered enough actionable intelligence to 'deliver a single person,' suggesting that mass surveillance is not intended to address terrorism and national security so much as to monitor and effectively control the public. Snowden's take on the illegality of mass surveillance practice:
Former NSA Technical Director William Binney has been a long-time critic of the NSA's mass surveillance activities. His criticism of the practice is especially important because he helped create the program, but was horrified to later learn that the system he had developed was used against American citizens in a vast domestic spying program. Binney's resignation in protest of domestic mass surveillance came years before the publication of the Snowden files. The issue of domestic surveillance as described in the Snowden documents has been thoroughly publicized by various outlets. However, the ready willingness of individuals like James M. Cusick, a major figure in the NSA's data acquisition program, to betray legal and ethical principles as openly stated in unreported Snowden documents creates a sharp contrast with the moral and constitutional stance shown by figures like William Binney.
Suzie commented at one point during our discussions that a little-discussed factor in the current neo-McCarthyist obsession with Russia may stem from the fact that the country took in Edward Snowden despite the US and Western Nation's desire to apprehend him. Dawson said: "If you're on the shitlist of the US Empire, the Western Mafia - [Russia is] one of the few countries you can go to and still live and work. So part of all this is a huge vendetta against Russia for providing safe refuge [for whistleblowers]." Dawson has often spoken of the double standard employed against dissidents who speak out against the wrongs of Western nations and allies in comparison with the large outpouring of support from Western NGO's and humanitarian groups in response to activists and whistleblowers from states opposed by the West and their allies, including Iran and Russia.
A further issue that Dawson and this author noted during the analysis of multiple unreported Snowden documents was the collaborative interaction between various intelligence agencies. This is significant because it works against the commonly held perception of Snowden as publishing NSA data due to animosity between the agencies.
Dawson noted that the content of the Snowden files did not support such an interpretation, instead revealing a revolving door between the agencies, and the large extent to which the various agencies were interdependent, providing necessary services for each other. This is significant because it goes against the framing of Snowden's release of NSA documents as the culmination of a rivalry between the CIA and NSA. The agencies are so intertwined that they deploy employees and establish offices within other agencies to handle specific issues relating to their specialization. Much of the content revealed in the Snowden documents reveals information that would harm the overall interests of the CIA much more than the agency would benefit from the wounded reputation of the NSA. Overall, Dawson and this author concluded in our analysis of the documents that it is highly unlikely that the CIA had any part in Snowden's decision to leak NSA information.
The CIA is also a principle 'customer' of the NSA. One of the numerous documents that discussed the interdependence between the NSA and CIA was the file from batch four titled: "CIA's Directorates ... Understanding More About Them." The document describes the collaboration between the CIA's Directorate of Intelligence (DI) and the NSA's Signals Intelligence (SIGINT): "Although there is certainly collaboration between CIA/DI's analytic community and NSA's SIGINT analysts, the CIA/DI is mostly a SIGINT customer using finished NSA/SID product as one of their most valuable sources in producing allsource intelligence products." That the CIA is an important customer for the NSA further suggests that the CIA would be unlikely to damage the NSA through the release of documents like those leaked by Edward Snowden, and adds to the conclusion that Snowden is indeed an unbiased whistleblower.
The same document goes on to describe the interdependence of the CIA and NSA regarding the CIA's Directorate of Operations and the NSA's Signals Intelligence Directorate: "There are many examples of DO and SID partnerships with HUMINT and SIGINT enabling each other.." The file goes on to describe the various directorates of the NSA and CIA and their customer-supplier relationship as well as their interdependence and joint efforts: "Some joint CIA-NSA efforts, which actually include people from across CIA directorates and SID organizations, offer the best examples of how these two agencies can work well together. The Special Collection Service (SCS) is a joint NSA-CIA organization whose mission is the covert collection of SIGINT from official U.S. establishments abroad. The Clandestine SIGINT Program (ClanSIG), run by the jointly staffed Technology Management Office (TMO) at CIA, provides numerous excellent examples of HUMINT enabling SIGINT and vice versa." Suzie Dawson compared the relationship between the agencies to the 'left hand and the right hand of the same body.'
Further documents illustrated the revolving door between the NSA and CIA as well as the corporate sector. A file titled "Perspectives from a Summer Intern," stated: "He worked at a wide variety of stops in the public sector -- including a tour as the deputy director at the CIA -- and later served in executive positions for private sector companies."
When The Huffington Post spoke with William Binney, he stated his belief that the NSA's dragnet surveillance practices were used by the FBI for the purpose of protecting big banking interests. This statement is particularly relevant in the discussion of an NSA document that shows meddling in foreign banking institutions. Although the Intercept has reported on this particular file, the outlet's coverage of the information amounted to one paragraph, and failed to discuss key questions raised by the agencies self-professed interference in foreign banks.
The document in question, titled "CRASH Team," states: "One key to the CRASH team's success has been its access to North Korean financial transaction data routed through foreign banks, a lucrative source for intelligence production and SIGINT Development (SIGDEV) efforts." The document continues: "In order to curtail North Korea's banking presence in Europe....Targeted financial institutions as collection targets in their own right. This revealed several instances of their complicity in North Korea's efforts to avoid scrutiny of its activities."
As Dawson and I discussed, the CRASH Team file raises serious questions about NSA's power over banks and financial institutions both domestically and internationally. Dawson described the significant questions raised by the revelation that the NSA had interfered with foreign banks: "The NSA spying on the commercial sector is probably much more rampant than we typically hear about. The next question is what they are doing with that information: the power of that information is unbelievable, they are collecting the strategic planning documents of those entities, knowing what they are going to do ahead of time. The capacity to act on that ahead of time is phenomenal. It's the power not just to respond punitively to what has happened or is happening, but to respond to what will happen, alter that future and prevent it from happening."
An additional document discussed during the DecipherYou livestreams listed a number of entities and institutions who are customers of the NSA's intelligence product. The file, titled: "The Washington Liaison Office: Who Are Those Guys?" lists the Federal Reserve Banking system as a customer of the NSA among other entities:
The document also states: "The [Washington Liason Office] customers usually have competing priorities totally unknown to each other requiring a delicate balancing act in providing timely SIGINT to all. For example, what the Secretary of Agriculture needs for her afternoon meeting with EU representatives is completely different from what the NASA Administrator needs prior to his visit to India." Again, serious questions arise from the fact that the Federal Reserve Bank is not a government entity, yet is able to buy intelligence services from the NSA. This raises obvious objections as to what varieties of services the Federal Reserve Bank buys from the NSA, and for what purpose this intelligence is used. The document's description of its customer's "competing priorities" implies an incredibly delicate and potentially disastrous amount of power held by the NSA. From the agencies track record in terms of both legality and ethics, this document raises serious concern.
An additional file titled "Conference on GSM Collection in Iraq," which has not been previously discussed by media outlets, indicated that as far back as 2004 simply being in a targeted geographical location was enough to cause the NSA to surveil handsets. The file iterates that: "... A profile was created to include only the calls that were made near 27 known heroin-processing labs in the country. When run against the available metadata, the program produced a list of the handsets that were used in the targeted area. The top 20 handsets were then tasked for collection, and at least one has produced reportable intelligence." This is significant because it shows that of 20 surveilled handsets, the vast majority produced no actionable data.
Dawson pointed out that issues of collecting data on random people physically present at domestically targeted events, including protests, could be comparable to the geographically determined spying shown in the document. Dawson discussed that in such examples, even those who were not protesting but happened to be in the physical vicinity of the protest (shop-keepers, passers by, etc) would be targeted in such an instance, illustrating the pervasiveness of intrusive mass surveillance.
The NSA file titled "Big Changes at the U.S. Mission to the United Nations (USUN)" proved exceptionally noteworthy, providing key insight into the NSA's role at the UN and the agency's self-concept regarding its influence in the lead up to the Iraq War. The file also illustrated the influence of the United States in crafting narratives that would drive decision-making at the UN. While Dawson and this author read the document, we were prompted to research a number of secondary sources including George W. Bush's speech to the UN in 2002. The NSA admits that the agency participated in crafting Bush's speech for the purpose of garnering support for the war in Iraq, as well as using as many UN resources as possible for the conflict.
In light of the 'Weapons of Mass Destruction' argument Bush employed during the UN speech crafted in part by the NSA, Dawson raised the issue of the suspicious death of Weapons Inspector Dr. David Kelly. The BBC reported on Kelly's death, stating that he had been outed as a possible source of a report that "cast doubt on the government's claim that Iraq had weapons of mass destruction capable of being deployed within 45 minutes." The BBC wrote that, soon after the controversy erupted, Kelly was found dead in "woodland a few miles from his Oxfordshire home after apparently taking his own life."
US and the NSA described the desire to use the UN infrastructure for the US agenda. The document brags about the NSA's success in crafting a global narrative regarding the War in Iraq and the UN's support of the conflict. The document also describes: "Our very own NSA representative to USUN, [redacted,] had announced not only the August 2004 end of his 3-year assignment but also his retirement from federal service in early September!" That the NSA has a representative of the agency which interfaces directly with the USUN is troubling.
Dawson described the report as the NSA's implicit admission that it controls the UN. She also noted that the 'Weapons of Mass Destruction' argument for the war, according to the NSA document, originated with SIGINT intelligence produced by the NSA. Effectively, the NSA is taking credit in the file for the WMD narrative that helped initiate US involvement in one of the longest, most devastating, and costliest wars in history. By 2013, Reuters reported that the war in Iraq had cost over $2 trillion. The Huffington Post reports that over 500, 000 Iraqi civilians have died during the conflict to date. That the NSA would claim responsibility for a narrative that led to one of the most expensive and harmful conflicts in recent memory makes it truly one of the most destructive forces the planet has ever seen.
Dawson commented that the NSA's admission suggests that the agency has taken part in constructing narratives and aiding in the creation of UN Resolutions for decades. The NSA document reads:
"As the U.S. mounted a strategic response to these attacks and worked with the UN to garner world support for the global war on terrorism, SIGINT proved vital in the U.S. negotiations that resulted in two key and unanimously-approved Security Council resolutions on Iraq. SIGINT also contributed to the composition of the U.S. President's speech at the UN General Assembly in September of 2002, and to Secretary Powell's presentation to the Security Council on the case against the Iraq dictator, among other events. SIGINT also helped USUN and State officials in their decisions regarding Afghanistan, countless peacekeeping operations around the world, Africa, Sudan and so many other situations."

Powell holding a model vial of anthrax while giving a presentation to the United Nations Security Council in February 2003.
The file emphasizes this point when it states: "SIGINT also contributed to the composition of the U.S. President's speech at the UN General Assembly in September of 2002, and to Secretary Powell's presentation to the Security Council on the case against the Iraq dictator, among other events." This passage indicates that the NSA's Signals Intelligence contributed to the now-infamous presentation to the UN given by former Secretary of State Colin Powell, who called that speech a "great intelligence failure,' according to PBS.
Crucially, the document also states that the NSA's Signals Intelligence: "Helped USUN and State officials in their decisions regarding Afghanistan, countless peacekeeping operations around the world, Africa, Sudan and so many other situations." This statement indicates that the NSA was not only responsible for providing faulty intelligence that led to the Iraq War, but that it has also contributed directly to foreign policy decisions made by the United Nations and the United States, in regards to: "Afghanistan, countless peacekeeping operations around the world, Africa, Sudan and so many other situations." The statement amounts to an admission that the NSA has been a driving force in the American foreign policy and United Nations decision-making process for years if not decades.




Either Snowden is a hero or not, but exposing the files from the US government would be a win win situation for Russia, China and other country.
Amazing Article @elizbethleavos
Thanks so much!
Nice post
Visit my blog
Please help vote me And flbck
Curated for #informationwar (by @openparadigm)

Relevance: Data Breach
Our Purpose
Thank you!
its a very helpful post, thank you :)
Disclaimer: I am just a bot trying to be helpful.
I note your professional reserve and find it appropriate and admirable.
I am not a held to such a standard, and can employ more direct statements.
I looked for the discussion of financial surveillance that would deliver actionable intelligence regarding business plans and undertakings, and was not disappointed. I sought this information because of the common apprehension of contractors and employees conducting 'love-ins', an agency euphemism for surveillance of current, potential, and past romantic interests of the stalkers (for some reason called 'analysts' in official parlance. They're really just creepy stalkers) in the agency, using government resources to spy on them for personal reasons, while on the clock.
In the context of financial concerns, I became certain the individuals with access to actionable business information attained the most lucrative possible insider information permitting trading and other operations to financially reward themselves using that information.
An example of how such surveillance covertly obtained could be used profitably would be learning of a business or high value individual being in financial difficulty, and seeking to divest assets. Knowing the specific price points would enable buyers to cut the deals to the bone, and pocket the sweet meats. Far more potential of lucrative profiteering is blackmail. There is no doubt copious discovery of information that would empower racketeers on government salaries or paid through government contract to rake in secret riches.
I noted the lack of discussion of either 'love-ins' or profiteering in this post, and guess none of the documents you reviewed dealt specifically with either. However, I am synthesizing information from other reports with what you review here, and find the surveillance of international financial institutions you did reveal extremely troubling, as clearly actionable insider information was available to stalkers infamous within the agency for such weak ethics as to so commonly use surveillance resources to stalk romantic interests thereby being labeled euphemistically.
It is certain that no ethical bars to using those resources to profit financially might either impede those parties.
Further, I noted the revelation that regional surveillance was undertaken and was undoubtedly often conducted in business districts, which would far more broadly potentiate illegal financial profiteering from the business plans and operations of more esoteric and less obvious targets. Such insider information would be vastly more difficult to detect being used profitably by those who attained it covertly, and particularly when such targets aren't typically either commonly considered targets of insider trading, or corporate espionage.
I bet none of these guys will retire poor. Given the atrocious record of government 'servants' regarding corruption, I consider this certainly widespread problem to be as significant, if not more so, due to it's immediate impact on private citizens and their assets and income, than the insidious effect ubiquitous surveillance has on public policy.
Lastly, I note the reference to Colin Powell's categorization of the SIGINT informing his speech to the UN as 'an intelligence failure' that somehow managed to supportively underpin the propaganda effort to demonize Saddam Hussein and Iraq, in the drive to war.
I will call this what it clearly appears to be: they made that shit up, and lied through their teeth, so they could kill millions of innocent people, and destroy a prosperous and sovereign nation, for profit. They kept doing it, and are still doing it today, not only in Iraq, but across the entire Middle East, and beyond, from Niger to Mongolia, from Chile to Norway. Maybe, just maybe, they're making shit up about Russia too ;)
Thanks very much for your hard and diligent work bringing previously obscure and highly relevant information into the sunshine of public disclosure.