
Long post.. I spent a few days coding these new features and organizing this post so it may be worth using an index, this time.. =]
INDEX:
- New reporting feature for the community
- Plans for Communities Mute Lists and Universal Script for Hive frontends
- New commands
- Screenshots of the commands in action
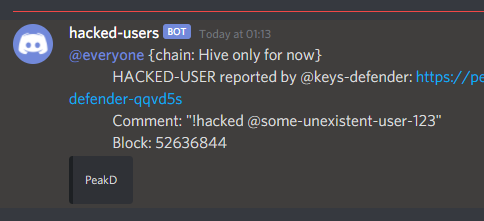
- Discord notifications for the community reports
- Preventing abuse of these new commands
- Testers required
- Future development
- How to consume my ban lists (10-line code snippet included)
Besides the phishing reporting feature ("!phishing" command) that I added to @keys-defender a couple of weeks back, starting from today the community can also report on-chain:
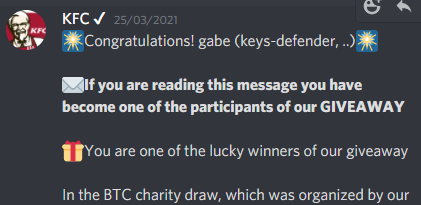
Eg. "you won 1 BTC" (you only have to deposit $ 500 and then wait a very very long time that tends to infinite). Reporting them early will prevent these scams from creeping into Hive.
the incident that happened with @threespeak
where a rogue dev took off with their domain.
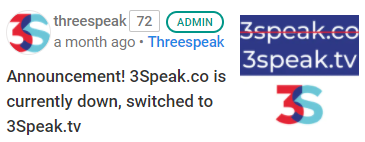
In order to mitigate security concerns @guiltyparties had to temporarily blacklist https://3speak.co as a phishing site. This new feature will now allow to avoid confusion between a website reported as compromised or plain old phishing. Also sites with known critical vulnerabilities may be marked as compromised until the security issue is patched.

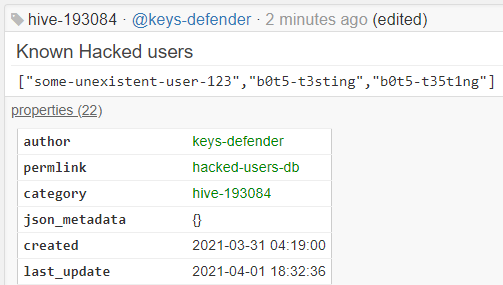
The improvement consist in the fact that instead of only consuming @spaminator's or @guiltyparties's list of hacked account,
I can now automatically use, in addition, this community-reported hacked accounts list.
Mm, auto-replies. That's it?
1. The hacked-users ban list will also be used by @keys-defender to implement the solution that some Hive devs suggested and that @louis88 explained in detail in his post 👉
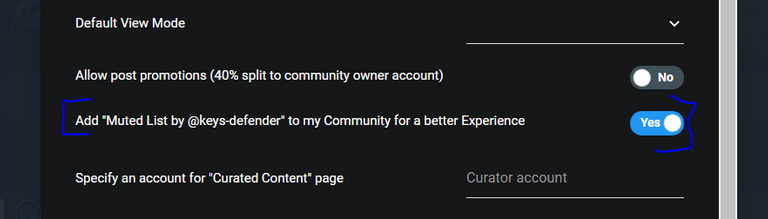
As part of the logic that automatically handles adding a hacked account to a banlist, in the near future I will also make it add it to my mute list (or likely to an alt account's). In this way community owners will be able to hide all phishing comments simply following my mute list in the community settings. FYI most-popular communities leaders 👆

2. All these new ban lists will be used by my Universal Script for Hive Frontends.
As requested by @quochuy (hopefully before the end of this week) I'll submit a Pull Request to the Hive condenser repository. I'll do that as soon as the version 2.0 of my script, improved and adapted among the other things to use my new ban lists, will be ready for release.
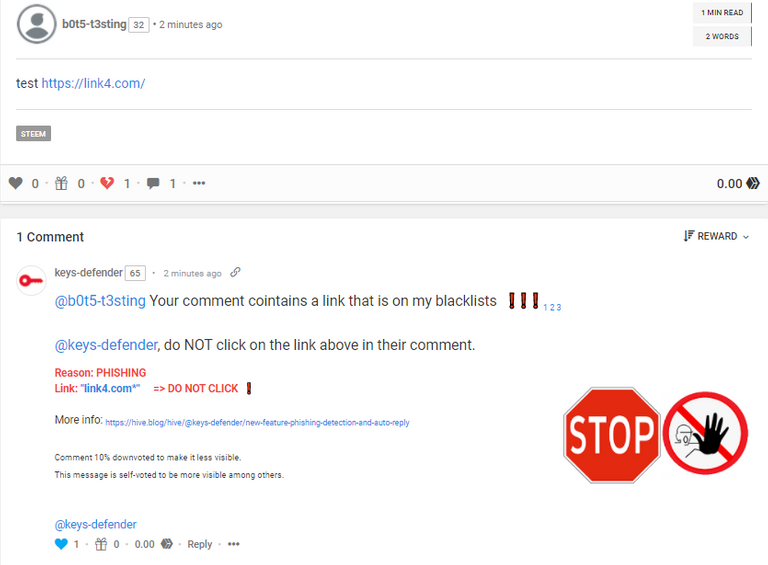
HOW do we report unsafe links and users, you ask?

Post a comment anywhere using the format below. You can leave it under your blog, as reply to another user, etc. You can use any Hive Frontend.
"@keys-defender command_to_execute link_or_user"
Example: "@keys-defender !SCAM https://nedspizzaforfree.com"
COMMANDS:
!INFO -> replies to your comment with the list of all available commands
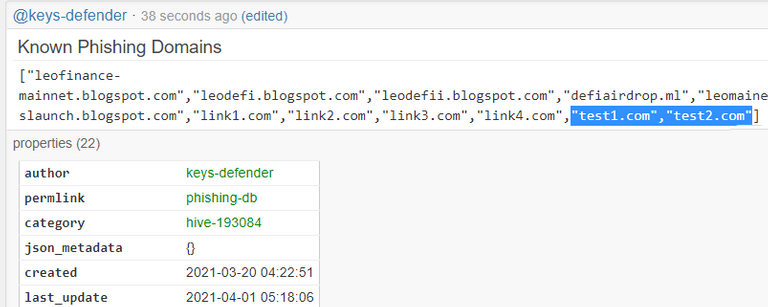
!PHISHING -> reports phishing links targeting the Hive ecosystem (see here)
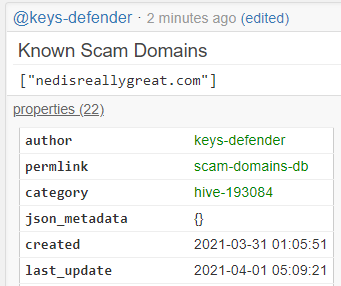
!SCAM - adds the target domain to the scam domains list
!UNSAFE - adds the target domain to the list of compromised domains
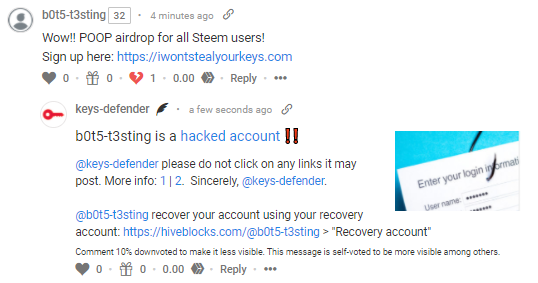
!HACKED - adds the target user to the list of hacked accounts
What will happen when you post a comment with those commands?
...in about 3 seconds you will get an auto-reply and a ~0.03 upvote.
Use these commands only when you are confident about the issue.
Users that intentionally abuse these commands will get $5 downvotes.
!INFO command
!SCAM command
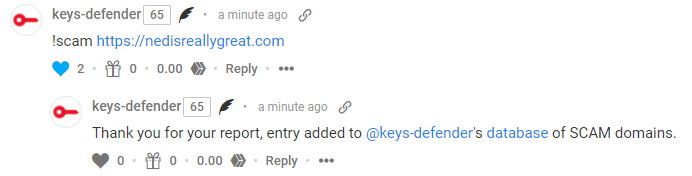
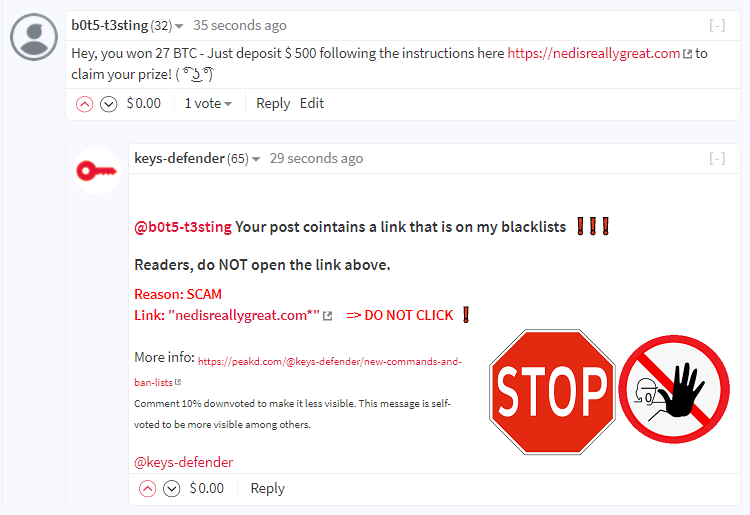
AUTOREPLY TO SCAM LINK IN MEMO: [supported for all commands]
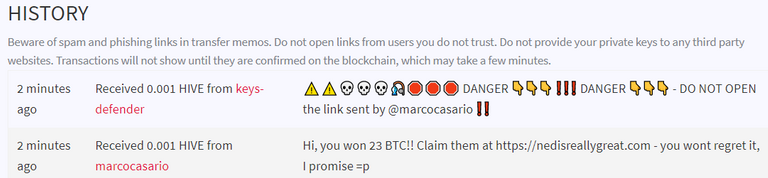
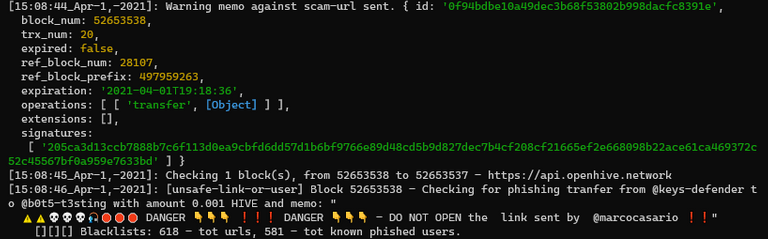
!UNSAFE command
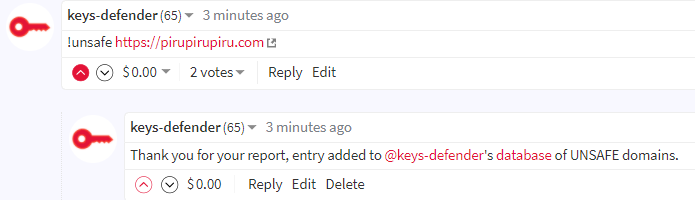
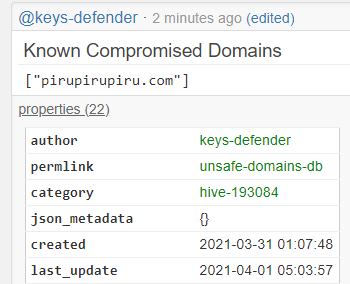
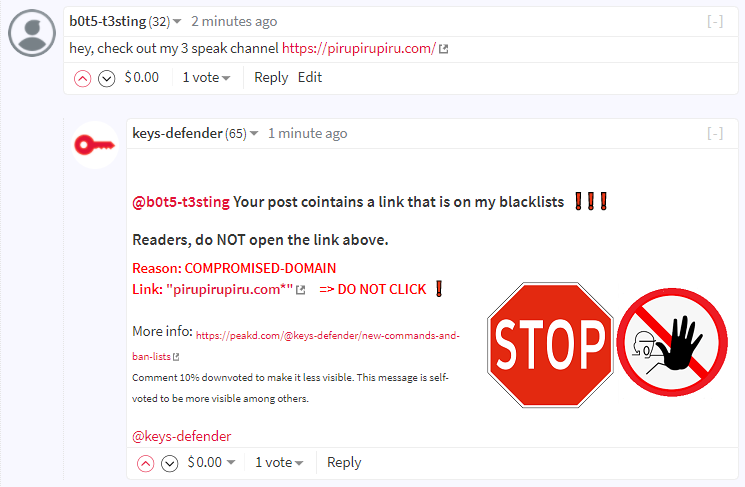
!HACKED command
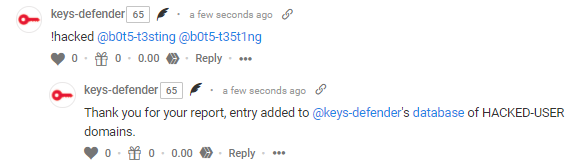

> NOTE: multiple domains and users in reports are now supported !!
eg. for the phishing command...
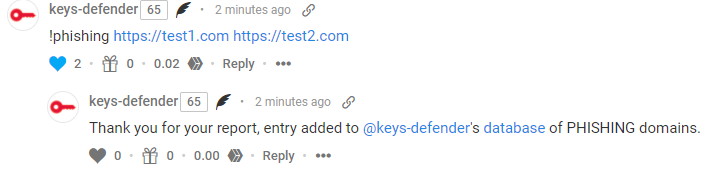
Hacked user notification:
Scam link notification:
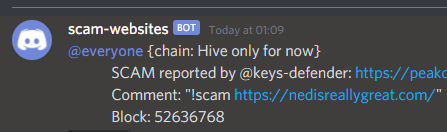
Compromised domain notification:
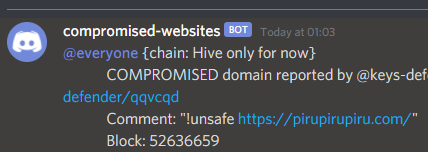

In order to reduce abuse, a domain whitelist is in use. Meaning that for example a newly created user cannot add hive.blog to the scam websites banlist =]
All top40 witnesses and a list of whitelisted users can send just a single report to add entries to the ban list.
That's not the case for regular users:
Minimum reputation for the reports to be processed: 50
Amount of reports required for regular users for each type of report:
-- Phishing domains: 3
-- Scam domains: 10
-- Compromised domains: 0 (only whitelisted users and top40 witnesses can)
-- Hacked accounts: 5 (will increase if abused - keep in mind the $5 downvotes..)

For 24 hours please feel free to test these commands using as targets non-existing domains and non-existing users.
Add the word "test" to your comment/report so that it will be easier for me to clean up the DB afterwards.
These scenarios should be covered too:
- Phishing/scam/unsafe links hiding
in shortened links;
- Unsafe links added to a comment
afterwards as edits.
Unfortunately your tests wont get reward$ because at the moment the voting power of my accounts is drained to fight against a comment farming campaign. See my latest post on @gaottantacinque if you are willing to help, anyone can help using that 10 line script easily executable in your browser.
PS - UPDATE: rewards doubled thanks to new delegations!!
- Besides the automated mute lists that communities leaders will be able to automatically follow, and the integration of these ban lists into my Universal Script for Hive frontends.. I plan on adding commands that allow whitelisted users to remove entries from the ban lists.
Priority will be for automating removal of users marked as hacked, in case they manage to recover. This is already partially implemented but not released yet.
- More commands to report abuse on Hive and get small rewards for it.
This will be handled in my newly created account @hive-defender !!
Example of JS/NodeJs code to use in your project:
const HIVE_API = 'https://api.hive.blog';
const TARGET_BANLIST = 'phishing-db'; // <<<< BANLIST PERMLINK HERE
const fetch = require(node-fetch); // <- for nodejs only, not needed in websites
fetch(
HIVE_API,
{
body: JSON.stringify({
jsonrpc: '2.0',
method: 'condenser_api.get_content',
params: ['keys-defender', TARGET_BANLIST],
id: 1,
}),
headers: {
'Content-Type': 'application/x-www-form-urlencoded'
},
method: 'POST'
},
)
.then(res => res.json())
.then(({ result } = {}) => console.log('Banlist:', result.body));
Again, if you are a maintainer of one of the Hive frontends you won't need to integrate my ban lists yourself if you use my Universal Script for Hive forntends.
FYI Hive Frontends maintainers:
@blocktrades @quochuy @asgarth @jarvie @khaleelkazi @good-karma @theycallmedan @starkerz @chrisrice @lemouth @enforcer48 @emrebeyler @heimindanger @arcange @engrave @nicniezgrublem @jesta @aggroed @penguinpablo @roadscape @holger80 @tobias-g @yabapmatt @stoodkev @aggroed @louis88 @mahdiyari @acidyo @fbslo @rishi556
PERMLINKS of the ban lists:
DB PERMLINK: 'zy71ydsnp4o1ufhs6j7ksz' - parent post containing all the banlists
- PHISHING LIST: 'phishing-db'
(click to open) - SCAMS LIST: 'scam-domains-db'
- UNSAFE DOMAINS LIST: 'unsafe-domains-db'
- HACKED USERS LIST: 'hacked-users-db'
- PHISHING LIST: 'phishing-db'
To track changes to the ban lists over time you can use:
https://scribe.hivekings.com/?url=https://hive.blog/@keys-defender/PERMLINK_HERE
- XSS vulnerabilities in #########.com
- XSS vulnerabilities in hive-db.com
- XSS vulnerabilities in scribe.hivekings.com
- XSS vulnerabilities in hiveblockexplorer.com
- Malicious ads redirecting all Steemit iOS users to a phishing site
- Reverse tabnabbing and clickjacking in steem.chat and steeemit registration page
Other contributions:
- Universal script to prevent phishing in all Hive frontends
- Commands for community reports and ban lists
Keys-Defender features:
- Phishing protection [live scan of commentsa and posts to warn users against known phishing campaigns and compromised domains, scan of memos]
- Re-posting detection [mitigates the issue of re-posters]
- Code injections detection [live scan of blocks for malicious code targeting dapps of the Hive ecosystem]
- Anti spam efforts [counteracts spam from hive haters]
Take care,
@keys-defender (@gaottantacinque)
If you like what I'm doing with @keys-defender please upvote, reblog,
delegate or auto-vote my posts.



Thanks for the great Update and your hard work in the last days!!!

!hacked (just to test communities following mute lists) @b0t5-t3sting
cc: @louis88
Thank you for your report, entry added to @keys-defender's database "HACKED-USER".
copy that
!PHISHING https://t.co/7YEWHX0iDT?amp=1
Careful, REAL ongoing phishing campaign!
Thank you for your report, entry added to @keys-defender's database of PHISHING domains.
!discovery 30
This post was shared and voted inside the discord by the curators team of discovery-it
Join our community! hive-193212
Discovery-it is also a Witness, vote for us here
Delegate to us for passive income. Check our 80% fee-back Program
!INFO
- [!phishing command and universal script]
- [!scam, !unsafe and !info commands]
👉 Don't abuse them or you'll get heavy downvotes
- !phishing {link}
- !scam {link}
- !unsafe {link}
- !hacked @{user}
- !recovered @{user}
- !info
- [!phishing command and universal script]
- [!scam, !unsafe and !info commands]
👉 Don't abuse them or you'll get heavy downvotes
- !phishing {link}
- !scam {link}
- !unsafe {link}
- !hacked @{user}
- !recovered @{user}
- !info
Good work @keys-defender.
Posted via D.Buzz
No, for obvious security reasons (eg. black hats could simply clone my repo and try to be faster than me, they could find bugs/vulnerabilities, etc etc)
Hmmm, but if its not open source, each abuse fighter and front-end team, must build from scratch.
Posted via D.Buzz
For new abuse fighter groups yes. It’s all in the @keys-defender code base so I cannot open up that repository.
Frontends can directly consume my banlists or the other banlists offered by the other groups (the 4 links are in Louis88’s article about phishing). If they integrate my universal script that will be done out of the box with all available ban lists. I’m a bit behind on that but v2 will come out soon (got distracted by adding new countermeasures in my code against farming).
Nice! And yeah, that's true.
Posted via D.Buzz